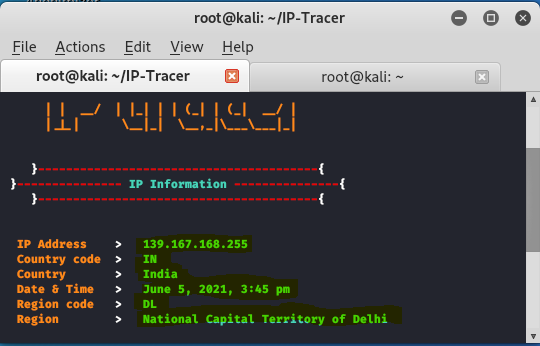
Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools

How to Overcome Credential Stuffing Attacks, by Kuba Zarzycki
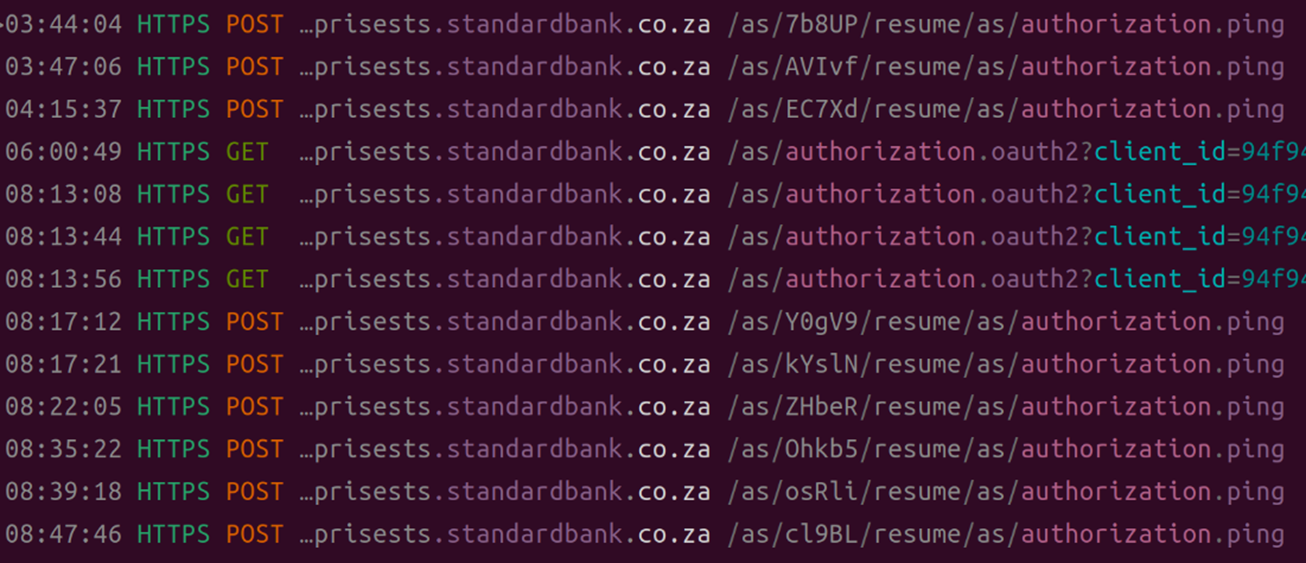
How Residential Proxies and CAPTCHA-Solving Services Become Agents of Abuse - Security News - Trend Micro IE

The State of Credential Stuffing and the Future of Account Takeovers.
How Residential Proxies and CAPTCHA-Solving Services Become Agents of Abuse - Security News - Trend Micro IE

The Account Takeover Kill Chain: A Five Step Analysis - ReliaQuest
Captcha Solver: Auto Recognition and Bypass
Best CAPTCHA Proxies in 2023 - ZenRows
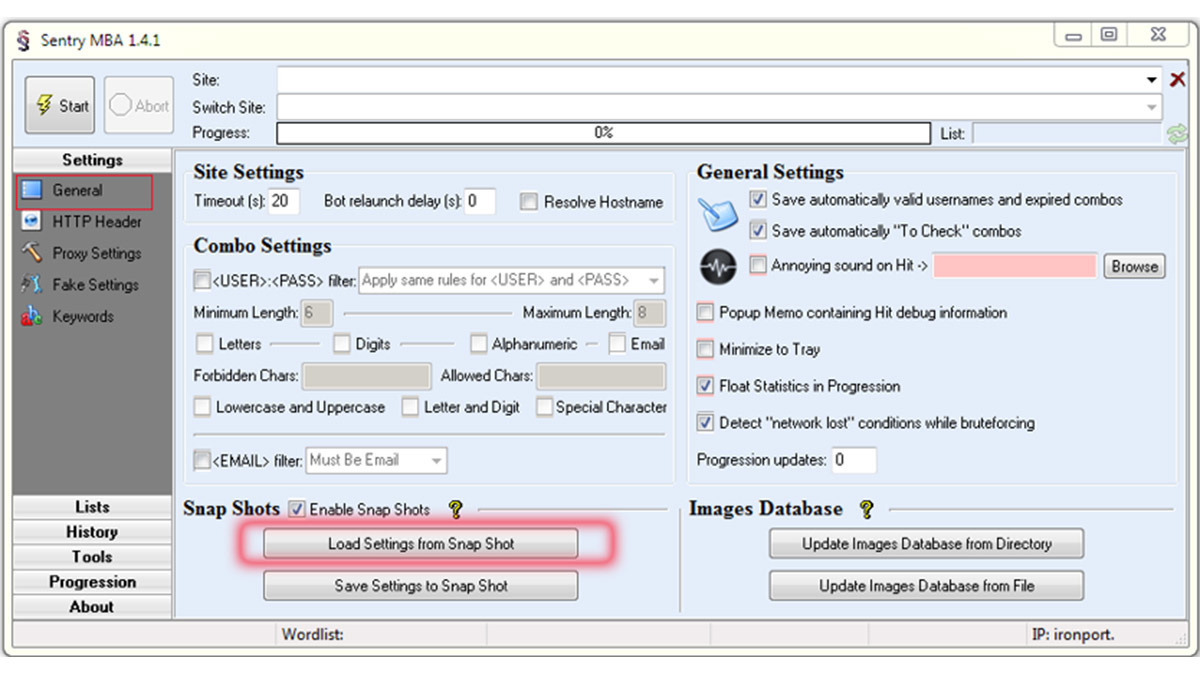
Credential stuffing attacks: How to protect your accounts from being compromised
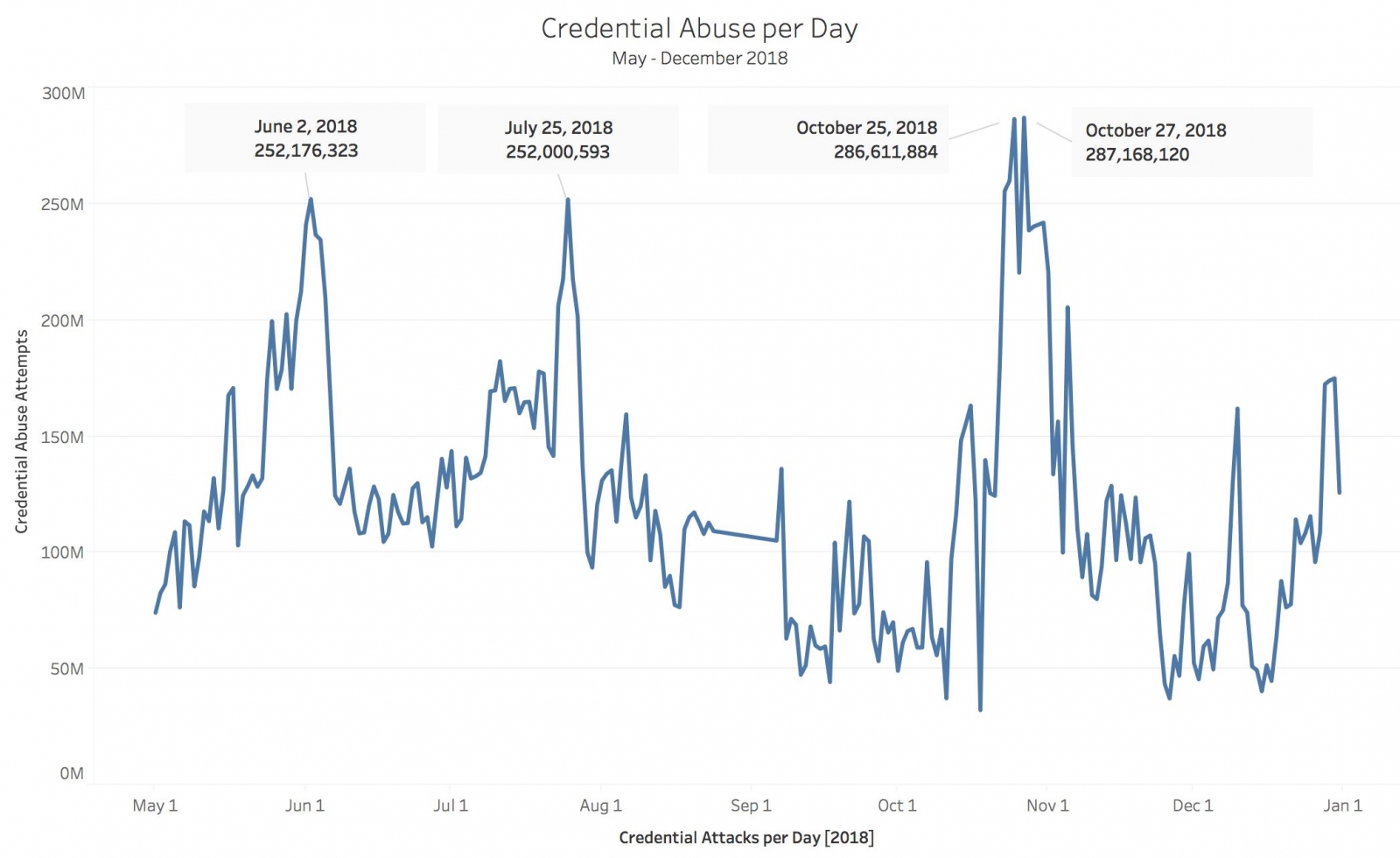
The Anatomy of Highly Profitable Credential Stuffing Attacks

Everything about Credential Stuffing (Video Included) – Inflow Technologies

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
de
por adulto (o preço varia de acordo com o tamanho do grupo)