6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Descrição
Behringer, Product

Center for Internet Security (CIS) Controls - TermsFeed

ADHD by the Numbers: Facts, Statistics, and You

Computer security - Wikipedia

Unleashing the Power of the Ford 6.4L Power Stroke: Double Horsepower with One Modification

Hyper Tough 16-inch Toolbox, Plastic Tool and Hardware Storage, Black
Understanding PCI DSS's New Client-side Security Requirements: Section 6.4.3
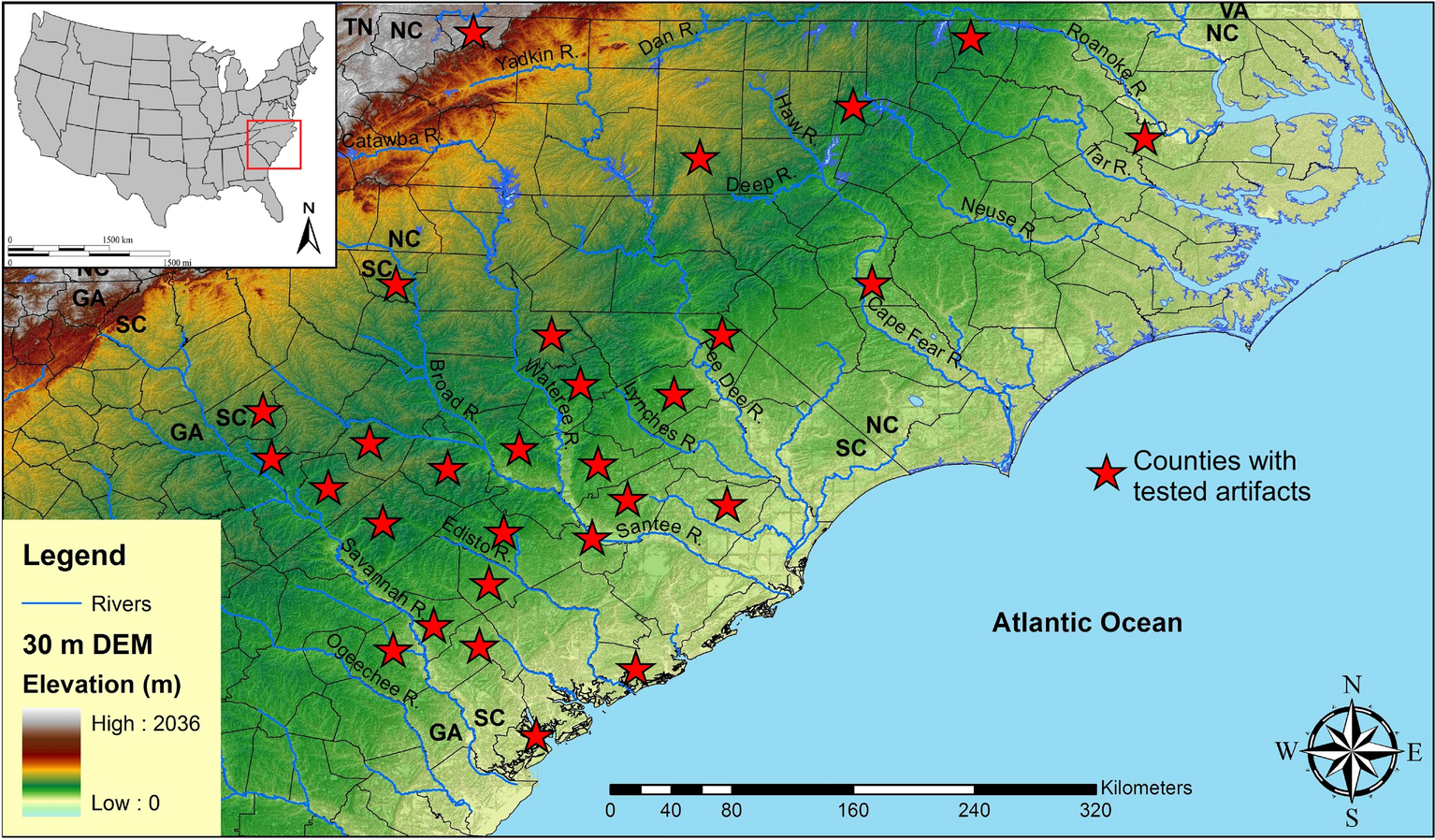
Paleoamerican exploitation of extinct megafauna revealed through immunological blood residue and microwear analysis, North and South Carolina, USA
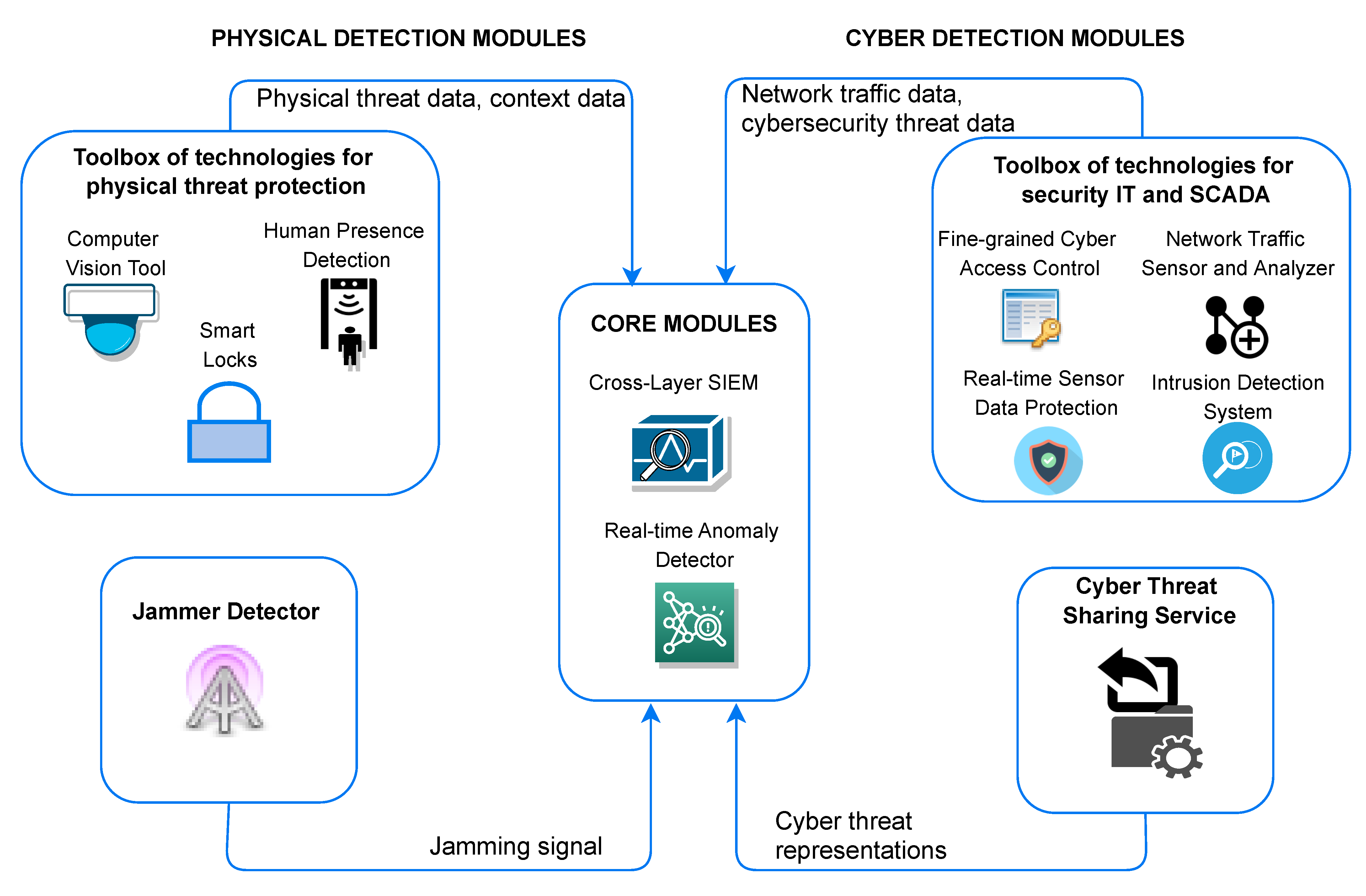
JCP, Free Full-Text

Introduction To Business Architecture – Part 1
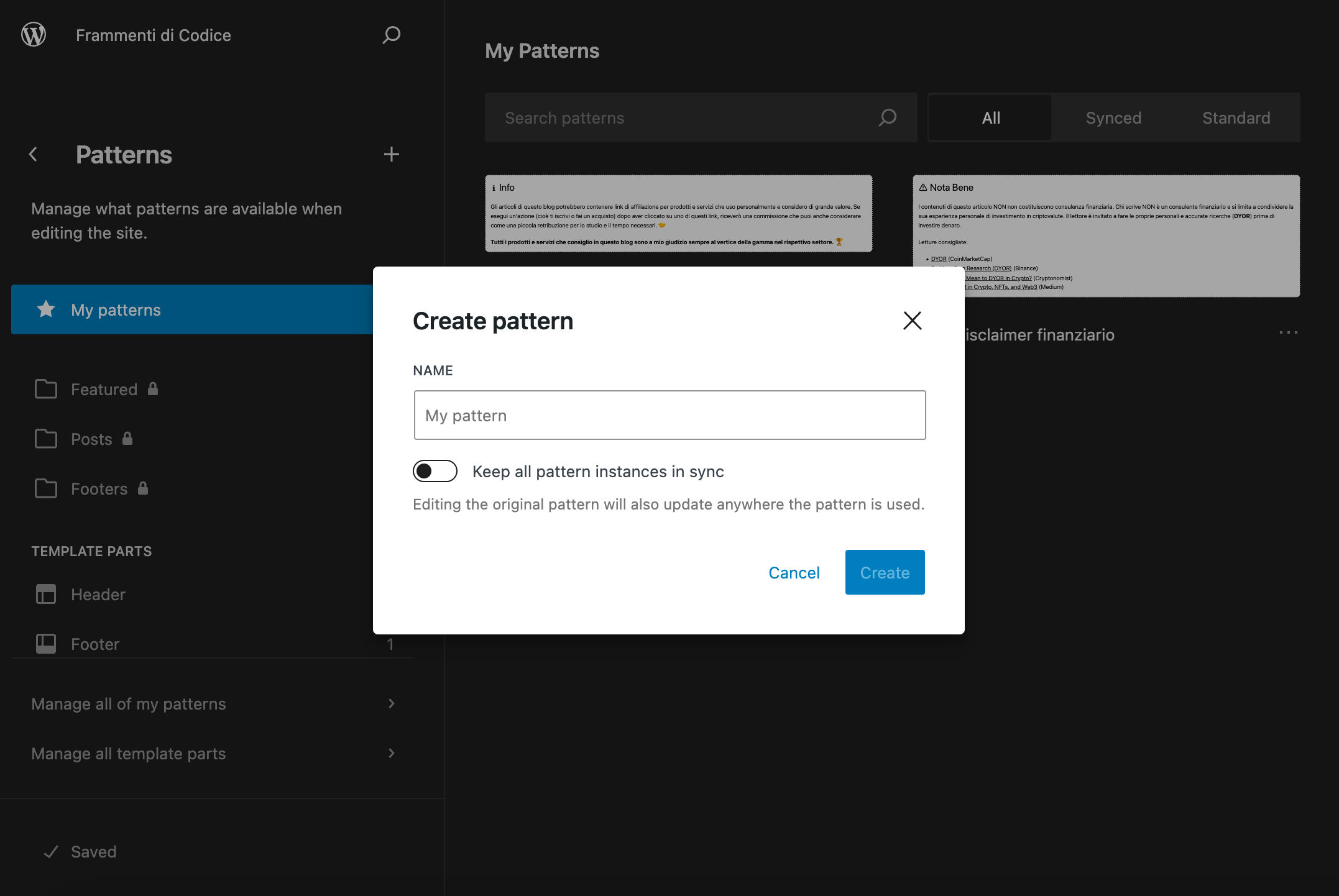
What's New in WordPress 6.4 - Kinsta®

Blind SQL Injection: An Expert's Guide to Detect and Exploit

Microorganisms Special Issue : 10th Anniversary of Microorganisms: Past, Present and Future

Amna - formerly Refugee Trauma Initiative

Makita T-01725 Contractor-Grade Bit Set, 70-Pc. - Jobber Drill Bits
de
por adulto (o preço varia de acordo com o tamanho do grupo)