Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

FastJSON deserialization bug can trigger RCE in popular Java
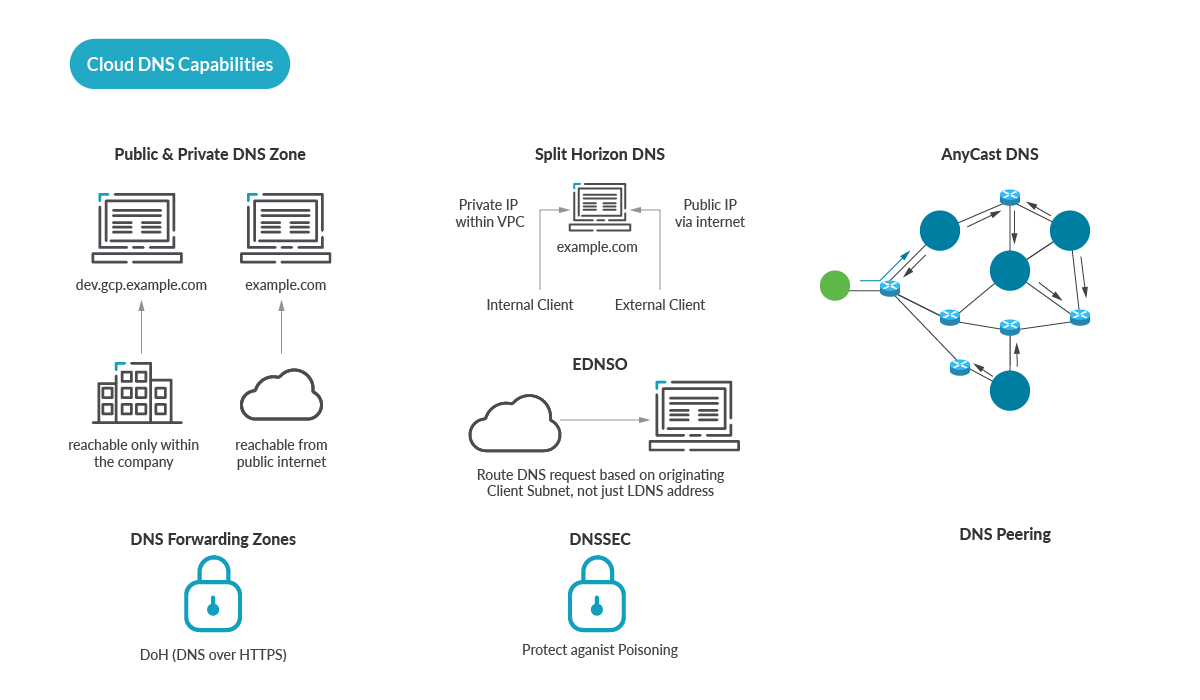
Cloud DNS Security - How to protect DNS in the Cloud – Sysdig

Project Zero: Lifting the (Hyper) Visor: Bypassing Samsung's Real
Handle Exceptions - OutSystems 11 Documentation

TryHackMe OWASP Top 10 - 2021

101 Landing Page Optimization Tips & Ideas
Aligning Substance Abuse Confidentiality Regulations With HIPAA to

Orange: Hacking Jenkins Part 2 - Abusing Meta Programming for

General Tools Digital Angle Finder Ruler #822 - 5 Stainless Steel

HIPAA Compliance Checklist 2024
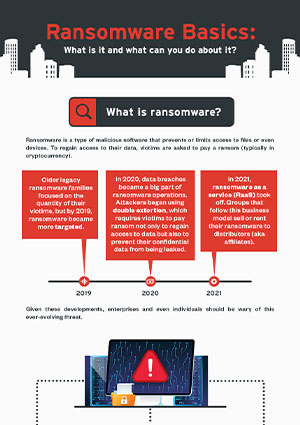
Ransomware - Definition

Nested Exceptions in Java: Definition & Example - Video & Lesson

Hunting for Suspicious Windows Libraries for Execution and Defense

The Lancet Commission on the future of care and clinical research
de
por adulto (o preço varia de acordo com o tamanho do grupo)