Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.
Por um escritor misterioso
Descrição
Discover the potential security risks of Bluetooth technology, including various types of attacks like bluejacking, bluesnarfing, bluebugging

Bluejacking vs Bluesnarfing: Exploring Bluetooth Hacking Variations.

bluejacking

Bluetooth Attacks (BlueJacking, BlueSnarfing, Blue bugging)

How Secure is Bluetooth? A Full Guide to Bluetooth Safety

Hacking Bluetooth Devices: Bluebugging, Bluejacking, Bluesnarfing
Exploiting Bluetooth driven devices — Bhargav.R, by Bhargav Ravinuthala
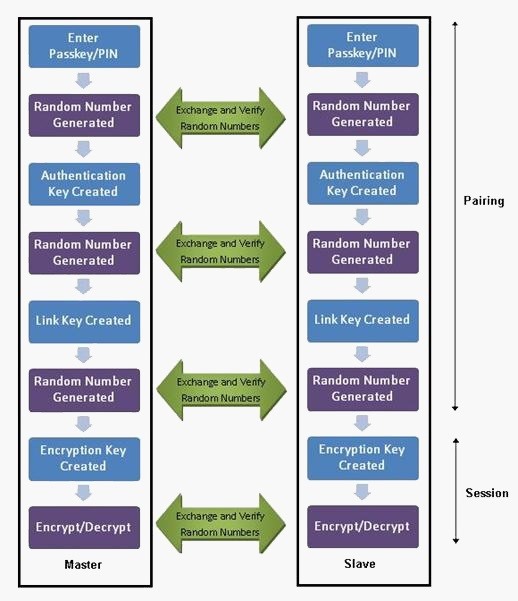
How to Hack Bluetooth, Part 1: Terms, Technologies, & Security « Null Byte :: WonderHowTo

Taming the Blue Beast: A Survey of Bluetooth Based Threats
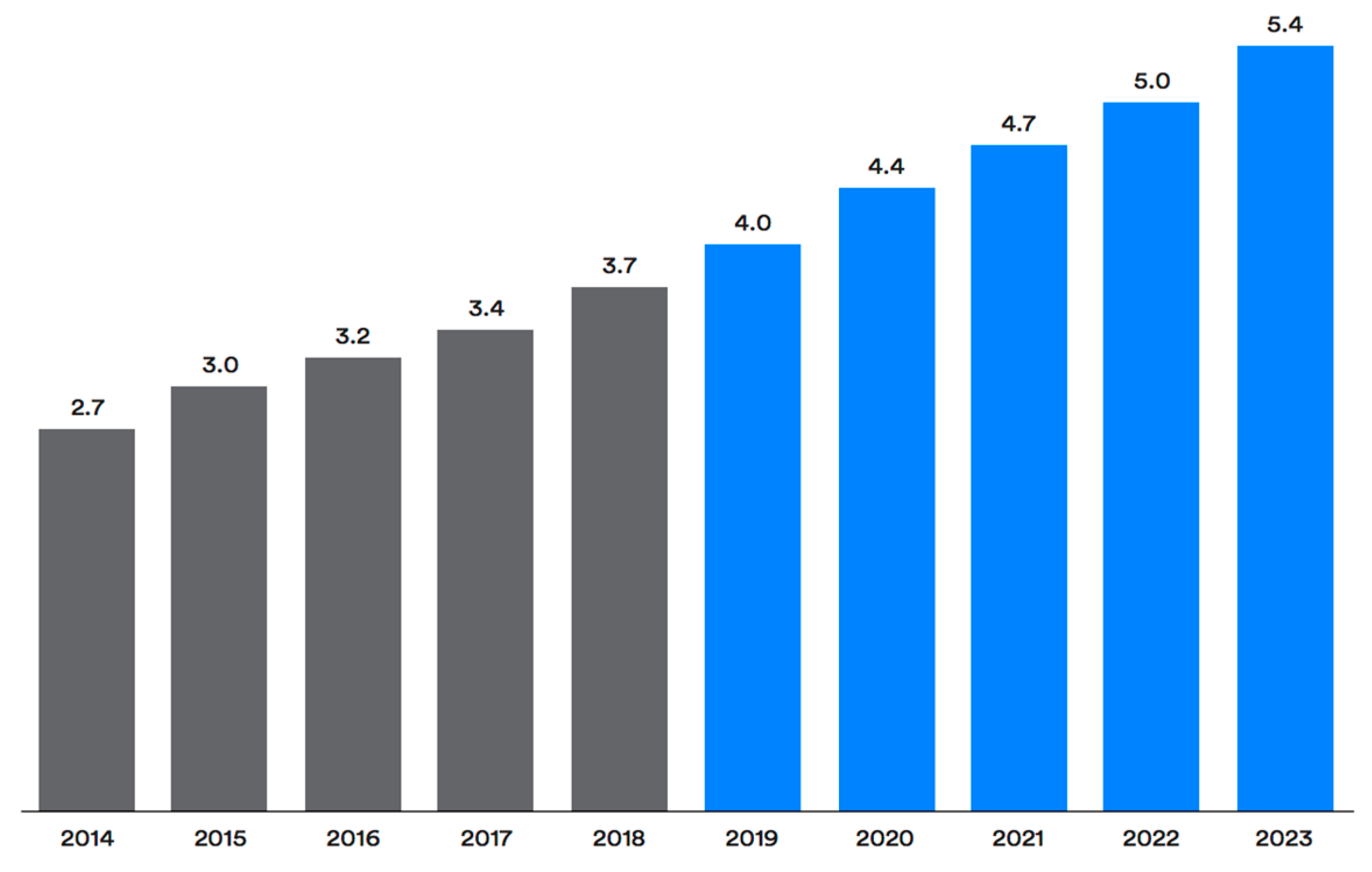
Future Internet, Free Full-Text

Diferencias entre los principales ataques por bluetooth: Bluesnarfing, Bluejacking y Bluebugging - CNET Technology Systems
PDF) Bluejacking Technology: A Review

Security threats in Bluetooth technology - ScienceDirect

How to Target Bluetooth Devices with Bettercap « Null Byte :: WonderHowTo
de
por adulto (o preço varia de acordo com o tamanho do grupo)