Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Descrição
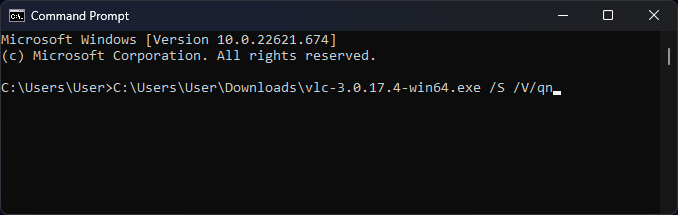
The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

T1202: Indirect Command Execution - Red Team Notes 2.0
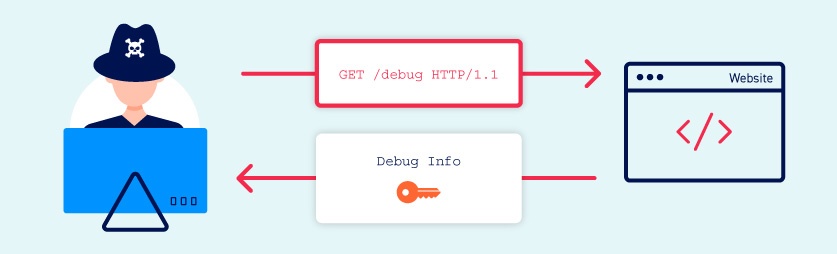
Information disclosure vulnerabilities

Indirect Command Execution – Penetration Testing Lab

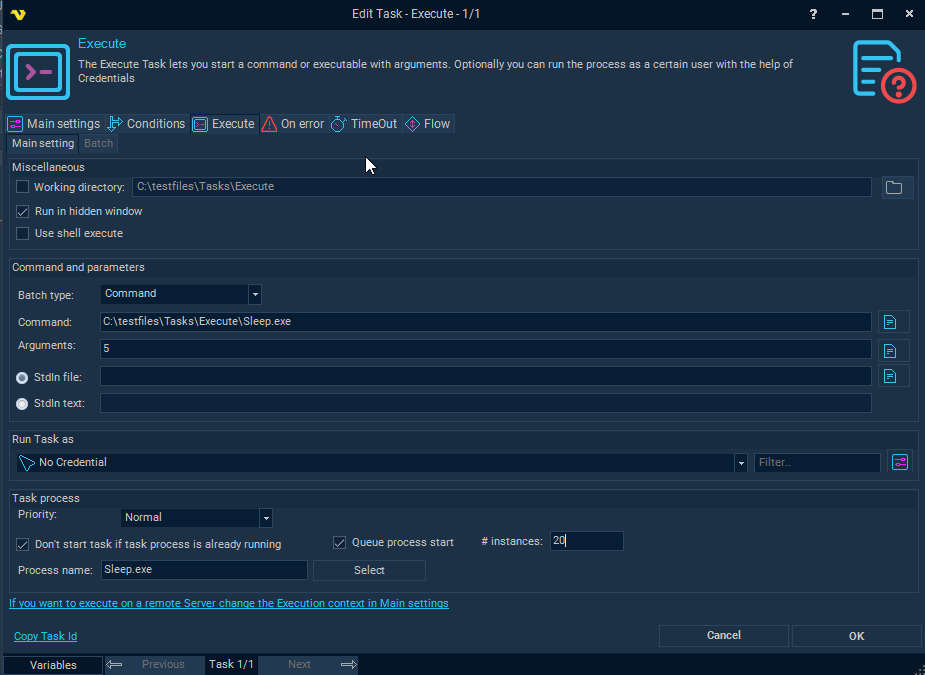
command execution walkthrough – Penetration Testing Lab
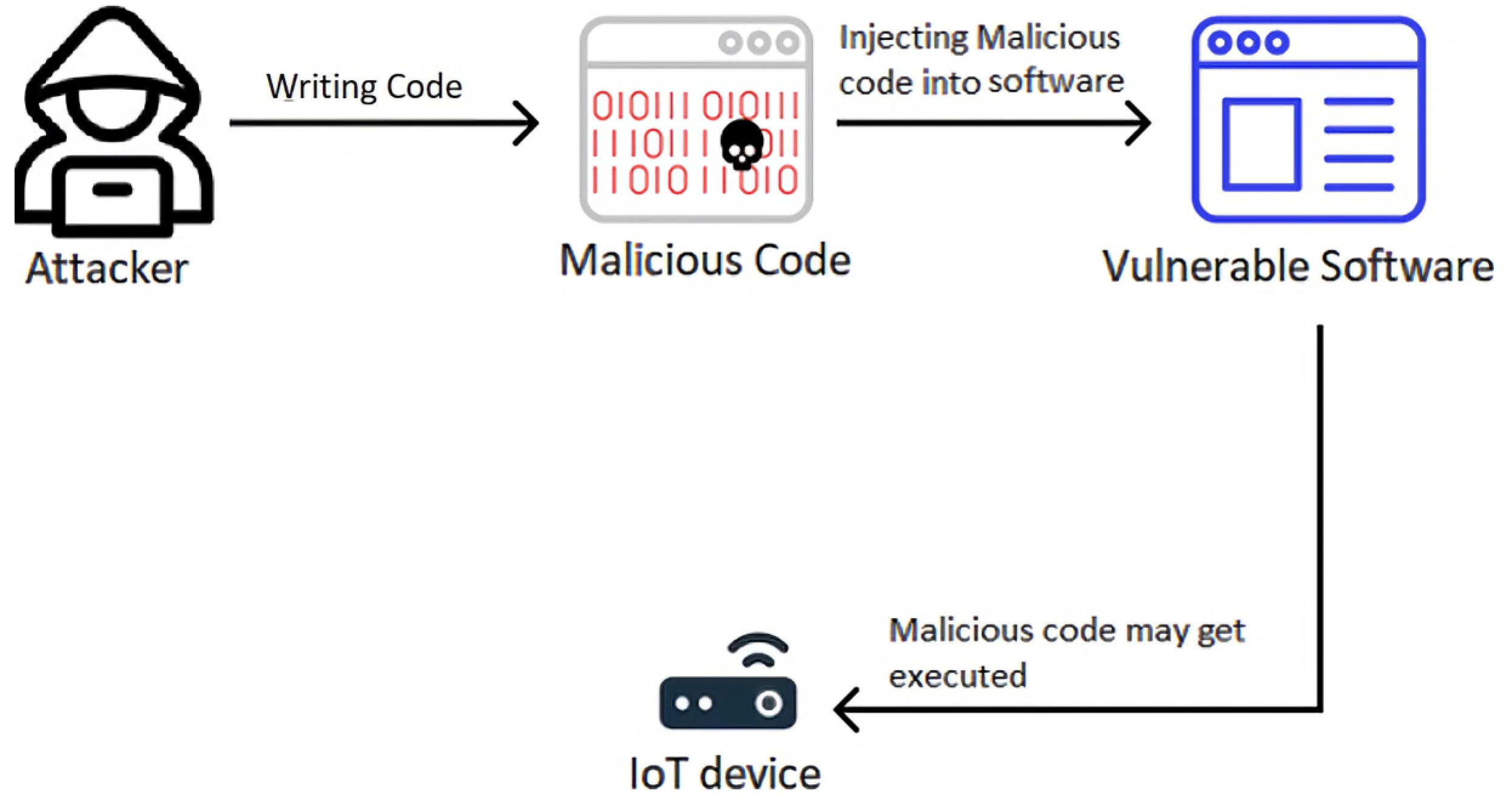
Sensors, Free Full-Text

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles

Command Execution – DVWA – Penetration Testing Lab
Next level for Siemens Industrial Edge: New cloud service, more devices, and low-code integration, Press, Company

Indirect Command Execution – Penetration Testing Lab
Pentesting CI/CD Methodology - HackTricks Cloud
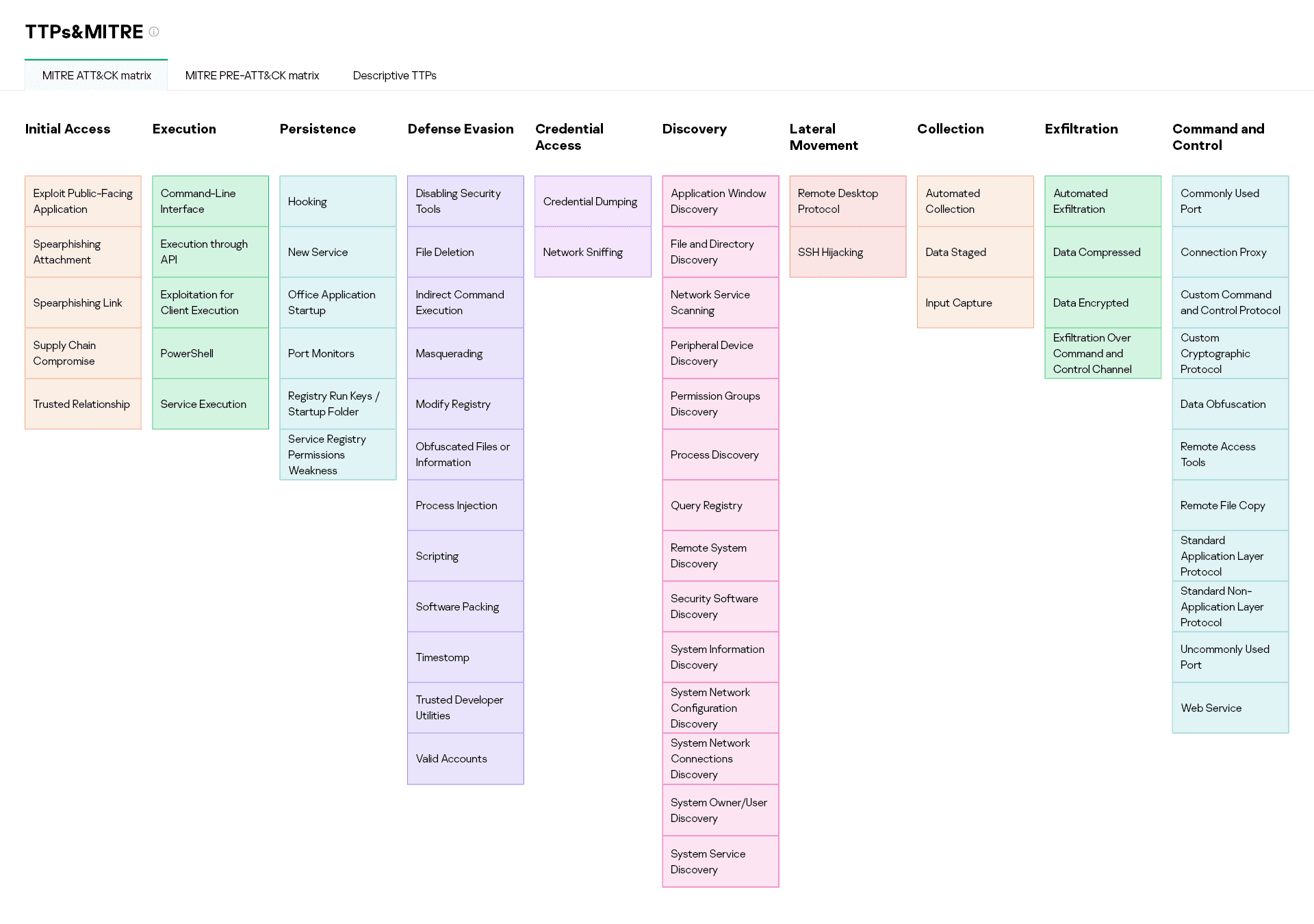
ATT&CK in APT Reports

How Much Does Red Team Penetration Testing Cost In 2023?

Command Injection - Lab #3 Blind OS command injection with output redirection
de
por adulto (o preço varia de acordo com o tamanho do grupo)