Complete UAF exploit - UD Capture
Por um escritor misterioso
Descrição
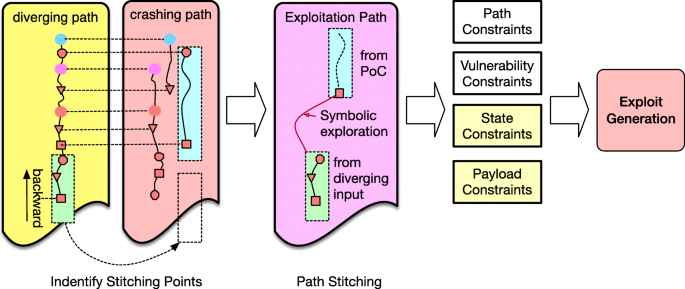
From proof-of-concept to exploitable, Cybersecurity
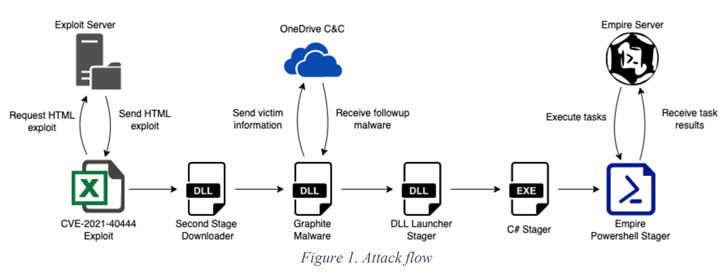
Hackers Exploited MSHTML Flaw to Spy on Government and Defen
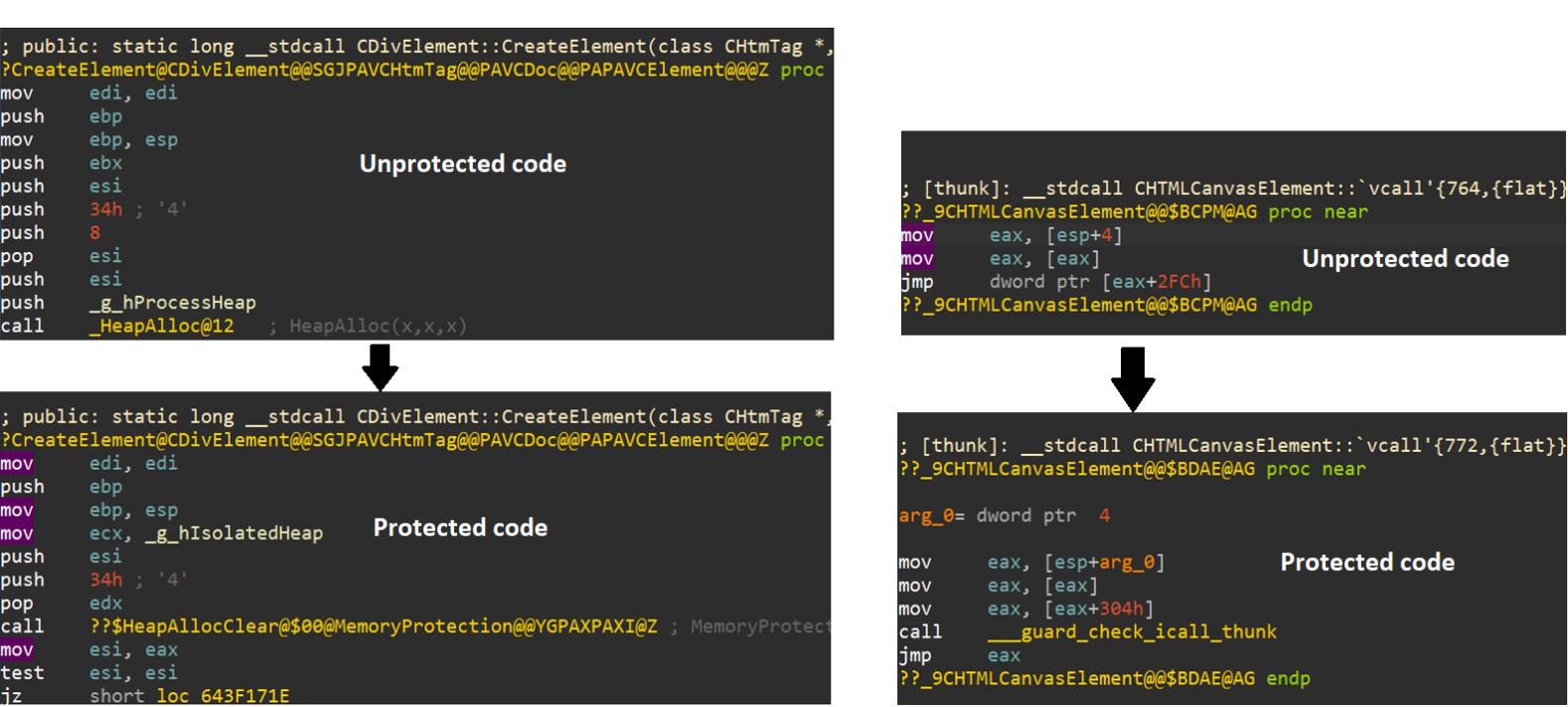
Beyond Memory Corruption Vulnerabilities – A Security Extinction

HITB2021SIN D1T1 - Exploiting UAF By Ret2bpf In Android Kernel

Google Reports 27 New Chrome Browser Exploits

Automated Use-After-Free Detection and Exploit Mitigation: How Far

Estimating the Bit Security of Pairing-Friendly Curves

Heap Exploit Development
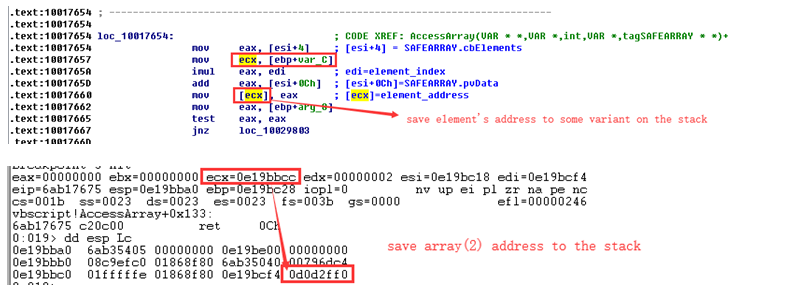
UAF Bug Affects Internet Explorer, Runs Shellcode

A fine-grained classification and security analysis of web-based

Firefox Referrer-Policy: Use-after-free vulnerability

Pwnable-Sherpa: An interactive coaching system with a case study

Reverse Engineering Coin Hunt World's Binary Protocol
The big heap adventure. Mastering heap exploitation techniques on
de
por adulto (o preço varia de acordo com o tamanho do grupo)




)


