Easier XSS payloads using HttpPwnly
Por um escritor misterioso
Descrição
Quite often you can find a Cross-Site Scripting (XSS) vulnerability in a web application. The minimal approach is to inject a JavaScript "alert" which says hello or something in there.

TrustedSec Tricks for Weaponizing XSS
GitHub - kleiton0x00/XSScope: XSScope is one of the most powerful

TrustedSec Tricks for Weaponizing XSS
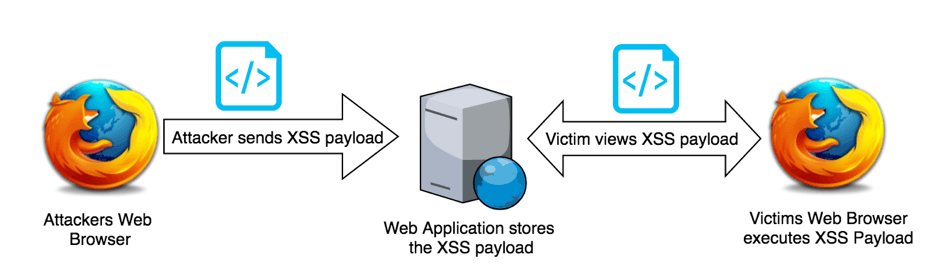
What is Cross-site Scripting (XSS)? Stored, DOM & Reflected Examples

TrustedSec Tricks for Weaponizing XSS
xss · GitHub Topics · GitHub

xss payload -confirm``- - Information Security Stack Exchange

How to make XSS payload manually - NanoTechx
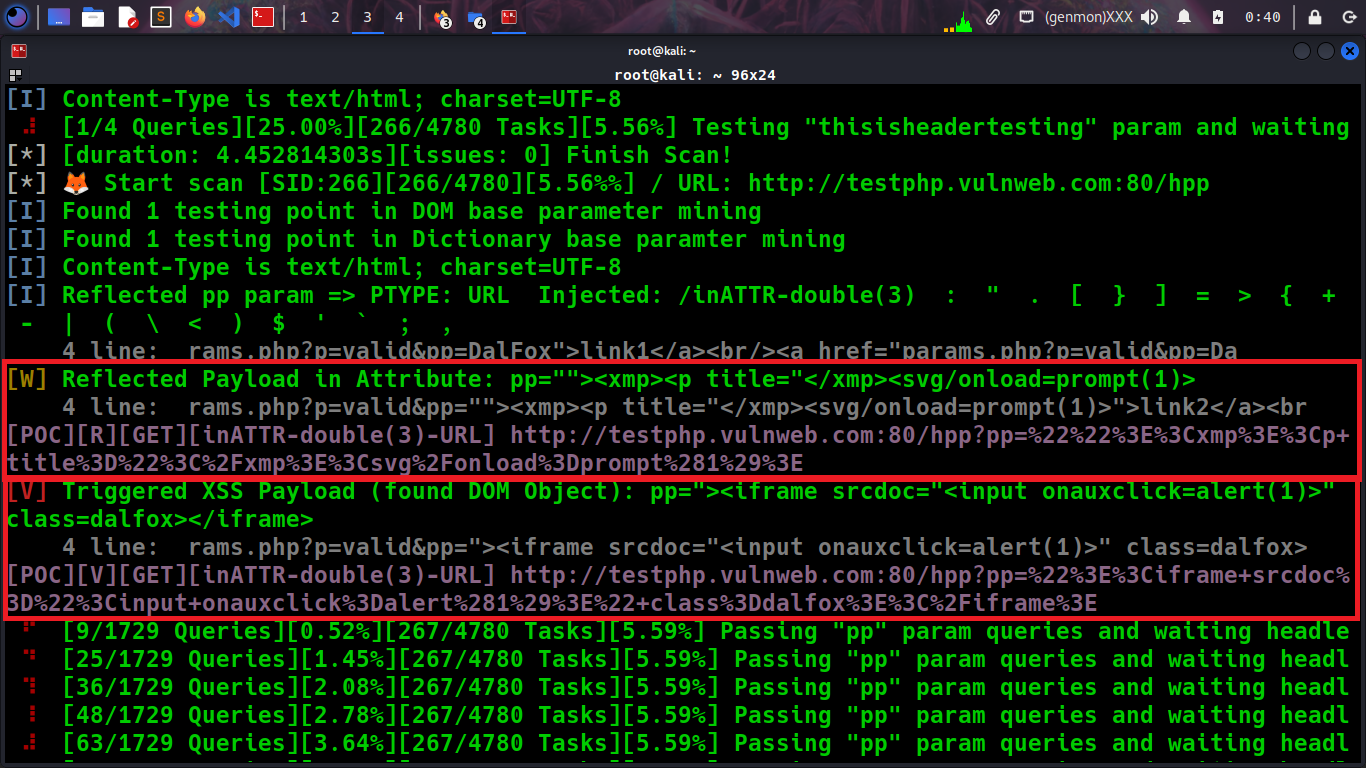
Exploit XSS Injections in a one-line powerful Technique

Weaponising Staged Cross-Site Scripting (XSS) Payloads
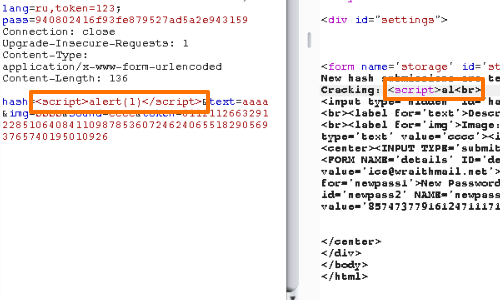
XSS Filters: Beating Length Limits Using Spanned Payloads
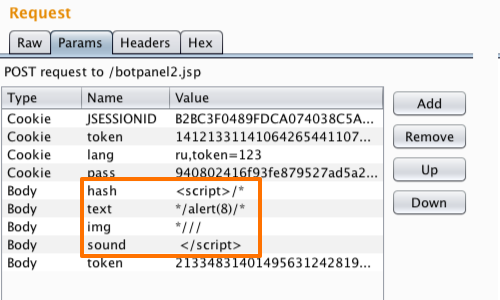
XSS Filters: Beating Length Limits Using Spanned Payloads
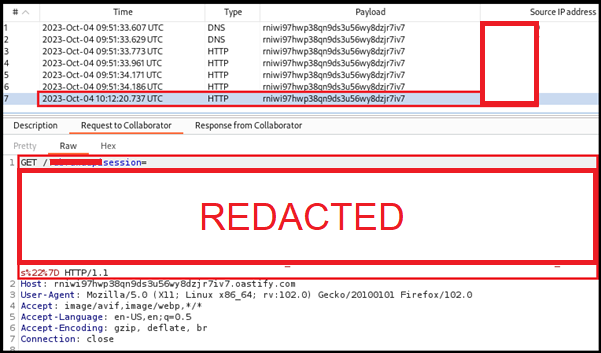
Weaponising Staged Cross-Site Scripting (XSS) Payloads
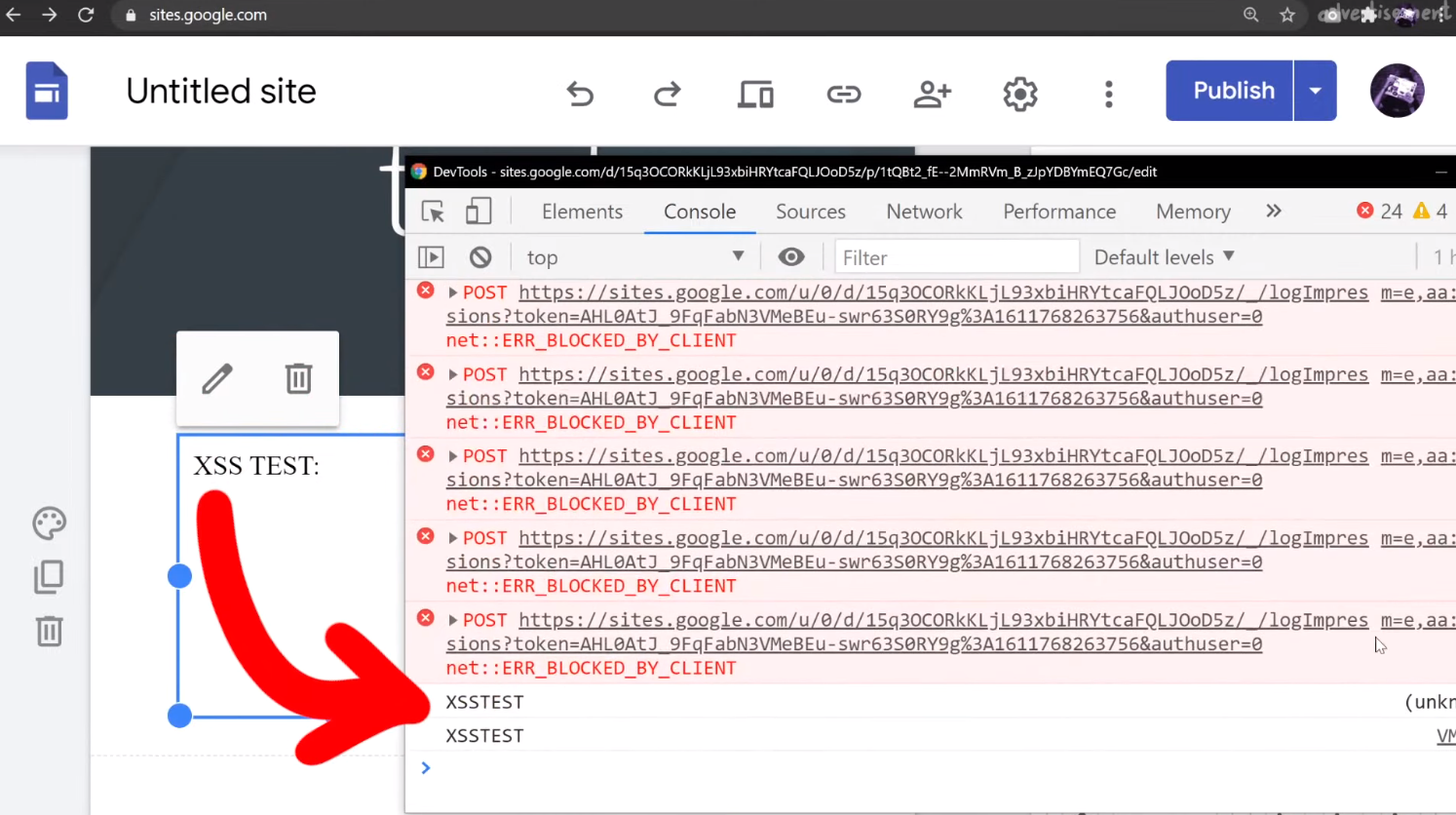
Do NOT use alert(1) in XSS
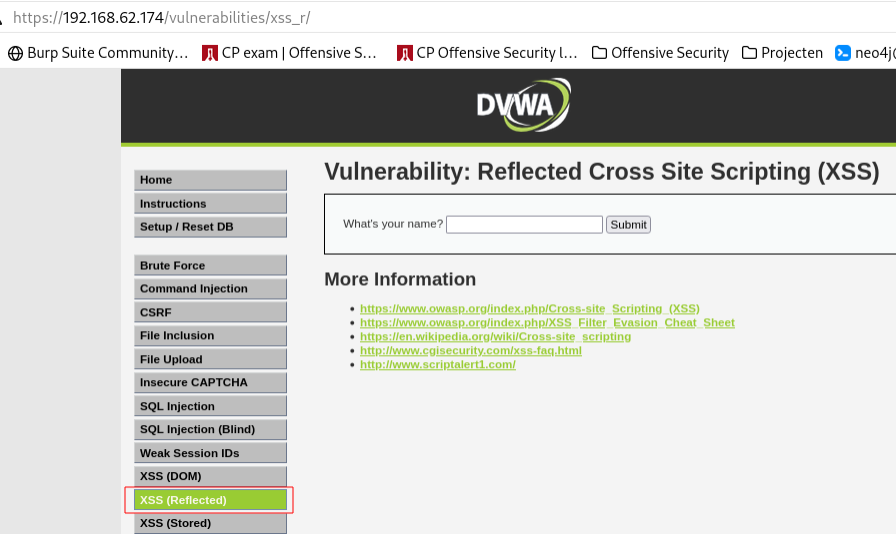
XSS exploitation without using the