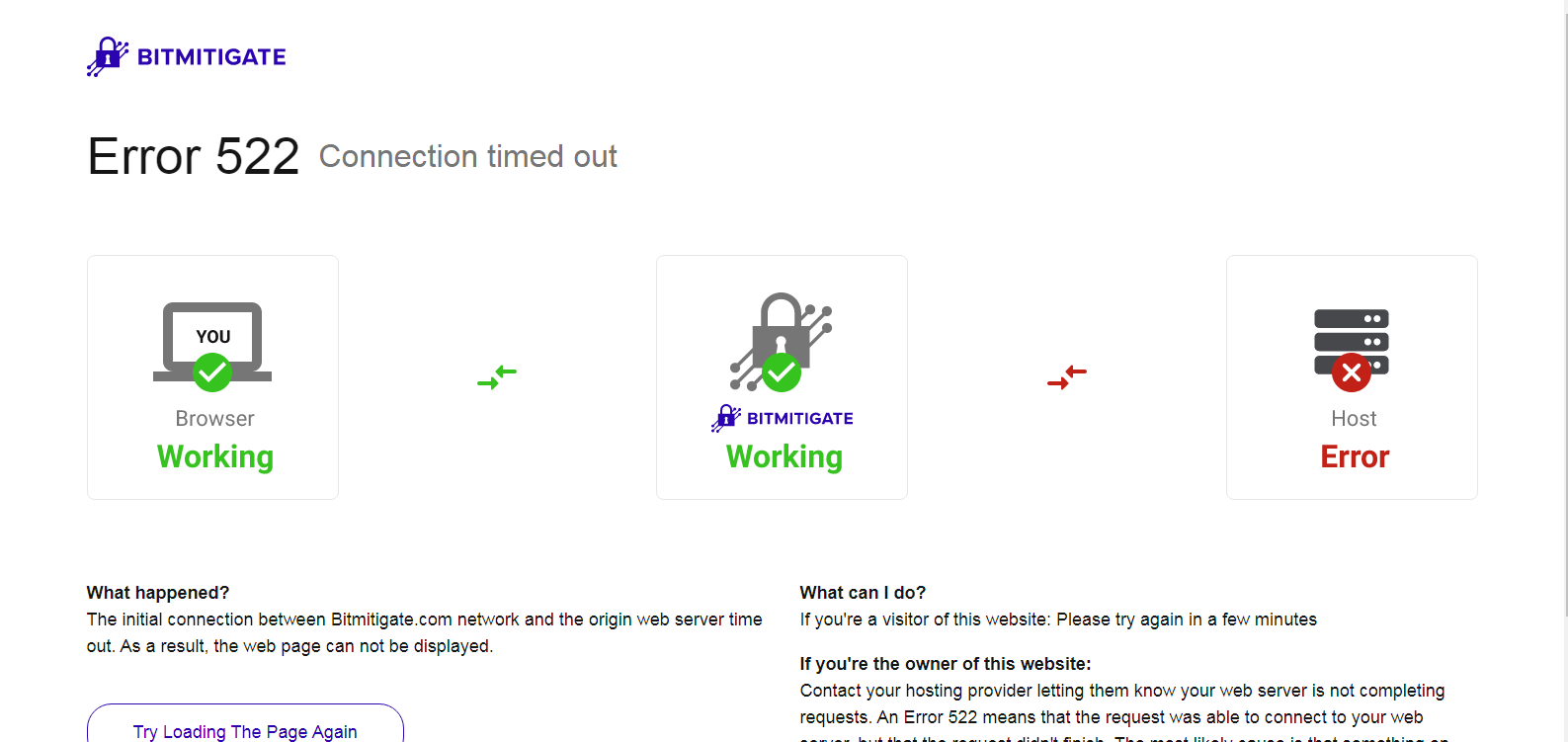
HiddenServices 2019-12-15, PDF, Computing
Por um escritor misterioso
Descrição

YO19 AC CH03 GRADER PC2 HW Instructions.docx - Grader - Instructions Access 2019 Project YO19 Access Ch03 Prepare - Turquoise Oasis Spa Data Management

Illuminating the hidden challenges of data-driven CDNs Proceedings of the 3rd Workshop on Machine Learning and Systems
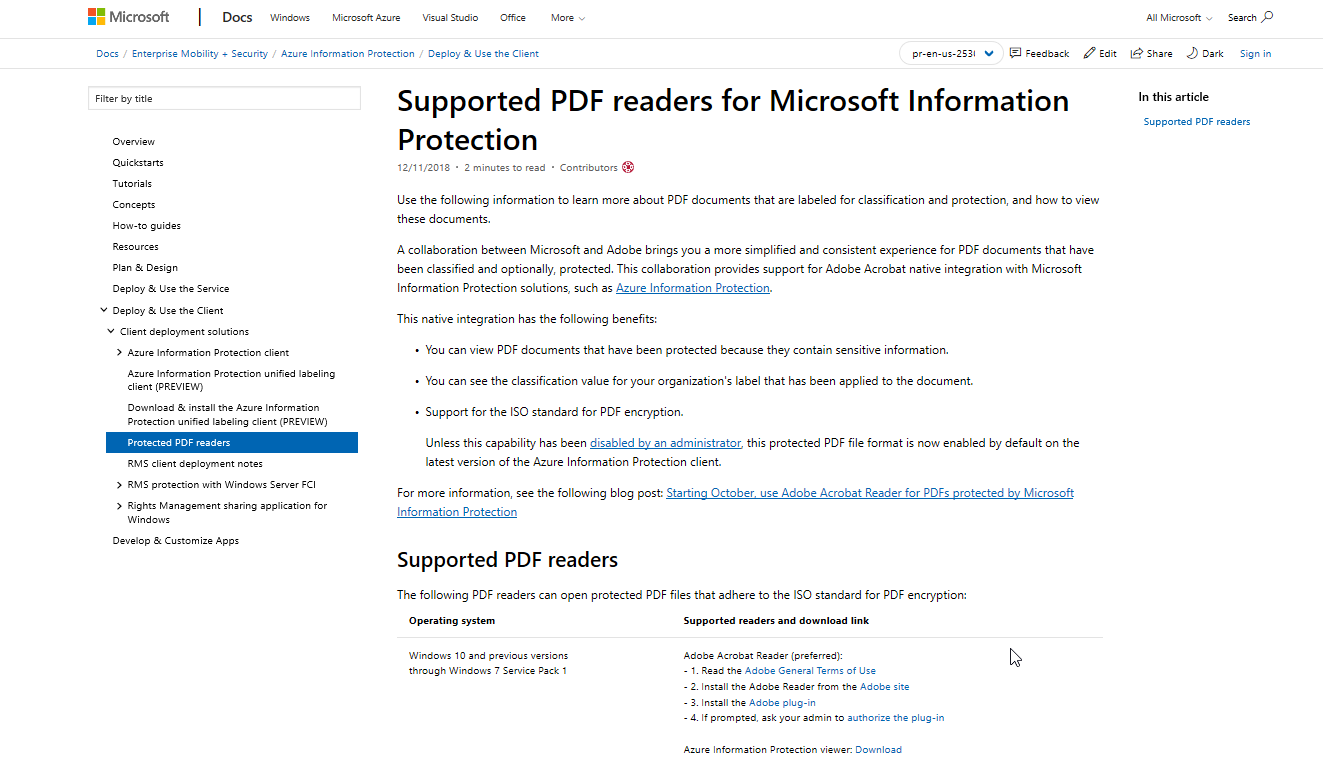
General Availability of Adobe Acrobat Reader Integration with Microsoft Information Protection - Page 2 - Microsoft Community Hub

heartbeat-percentiles-default-90.jpg

BQT® HID® Prox 125kHz and DESfire® 13.56MHz Dual Technology Reader - Encrypted (E22025) - Electronic Security Sales

Network Forensics: Tracking Hackers through Cyberspace eBook : Davidoff, Sherri, Ham, Jonathan: Kindle Store

HiddenServices 2019-12-18, PDF, Computing

The Impact of Group Size on the Discovery of Hidden Profiles in Online Discussion Groups

YO19 AC CH03 GRADER PC2 HW Instructions.docx - Grader - Instructions Access 2019 Project YO19 Access Ch03 Prepare - Turquoise Oasis Spa Data Management

PDF) Protecting against Website Fingerprinting with Multihoming

Computers and Internet Crossword Puzzle Clues, PDF, Crossword

Navigate eBook Access for Hacker Techniques, Tools, and Incident Handling with Cloud Labs: 9781284172614
de
por adulto (o preço varia de acordo com o tamanho do grupo)