Information, Free Full-Text
Por um escritor misterioso
Descrição
The connected or smart environment is the integration of smart devices (sensors, IoT devices, or actuator) into the Internet of Things (IoT) paradigm, in which a large number of devices are connected, monitoring the physical environment and processes and transmitting into the centralized database for advanced analytics and analysis. This integrated and connected setup allows greater levels of automation of smart systems than is possible with just the Internet. While delivering services to the different processes and application within connected smart systems, these IoT devices perform an impeccably large number of device-to-device communications that allow them to access the selected subsets of device information and data. The sensitive and private nature of these data renders the smart infrastructure vulnerable to copious attacks which threat agents exploit for cyberattacks which not only affect critical services but probably bring threat to people’s lives. Hence, advanced measures need to be taken for securing smart environments, such as dynamic access control, advanced network screening, and monitoring behavioural anomalies. In this paper, we have discussed the essential cyberthreats and vulnerabilities in smart environments and proposed ZAIB (Zero-Trust and ABAC for IoT using Blockchain), a novel secure framework that monitors and facilitates device-to-device communications with different levels of access-controlled mechanisms based on environmental parameters and device behaviour. It is protected by zero-trust architecture and provides dynamic behavioural analysis of IoT devices by calculating device trust levels for each request. ZAIB enforces variable policies specifically generated for each scenario by using attribute-based access control (ABAC). We have used blockchain to ensure anonymous device and user registrations and immutable activity logs. All the attributes, trust level histories, and data generated by IoT devices are protected using IPFS. Finally, a security evaluation shows that ZAIB satisfies the needs of active defence and end-to-end security enforcement of data, users, and services involved in a smart grid network.
How to Do a Review of the Literature?
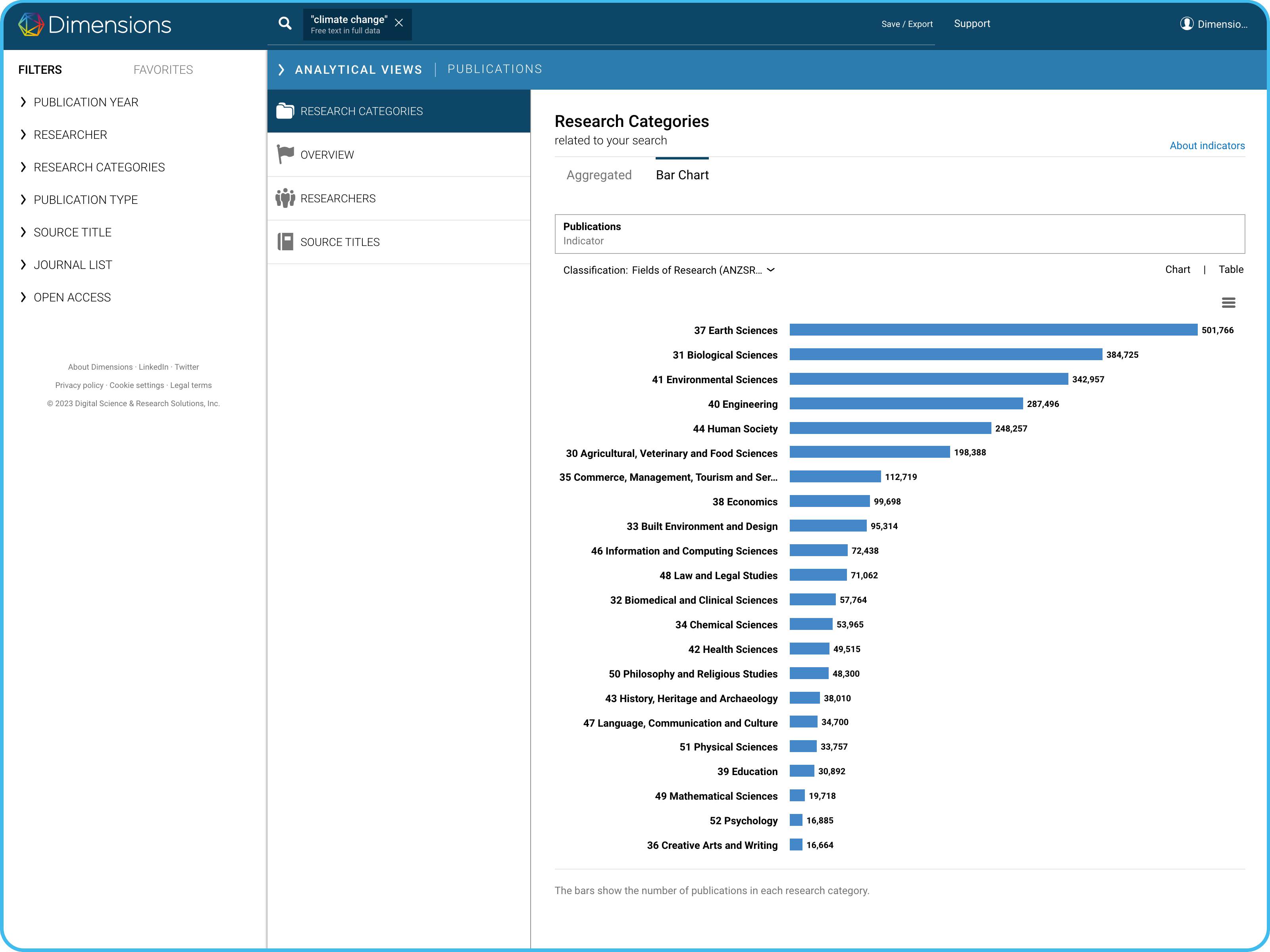
Dimensions - free version
Accentuate Custom Fields - Accentuate Custom Fields: Advanced Store Customization

50 Free Vintage Dictionary Page Printables - Rose Clearfield
Submission Guidelines
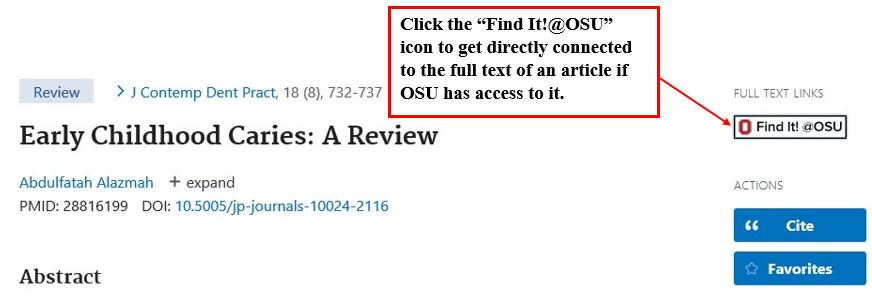
How Do I Find The Full Text Of An Article?

3 Smart Ways to Download Free Full Text Articles for Your Literature Review

Find free PDF of scientific publications
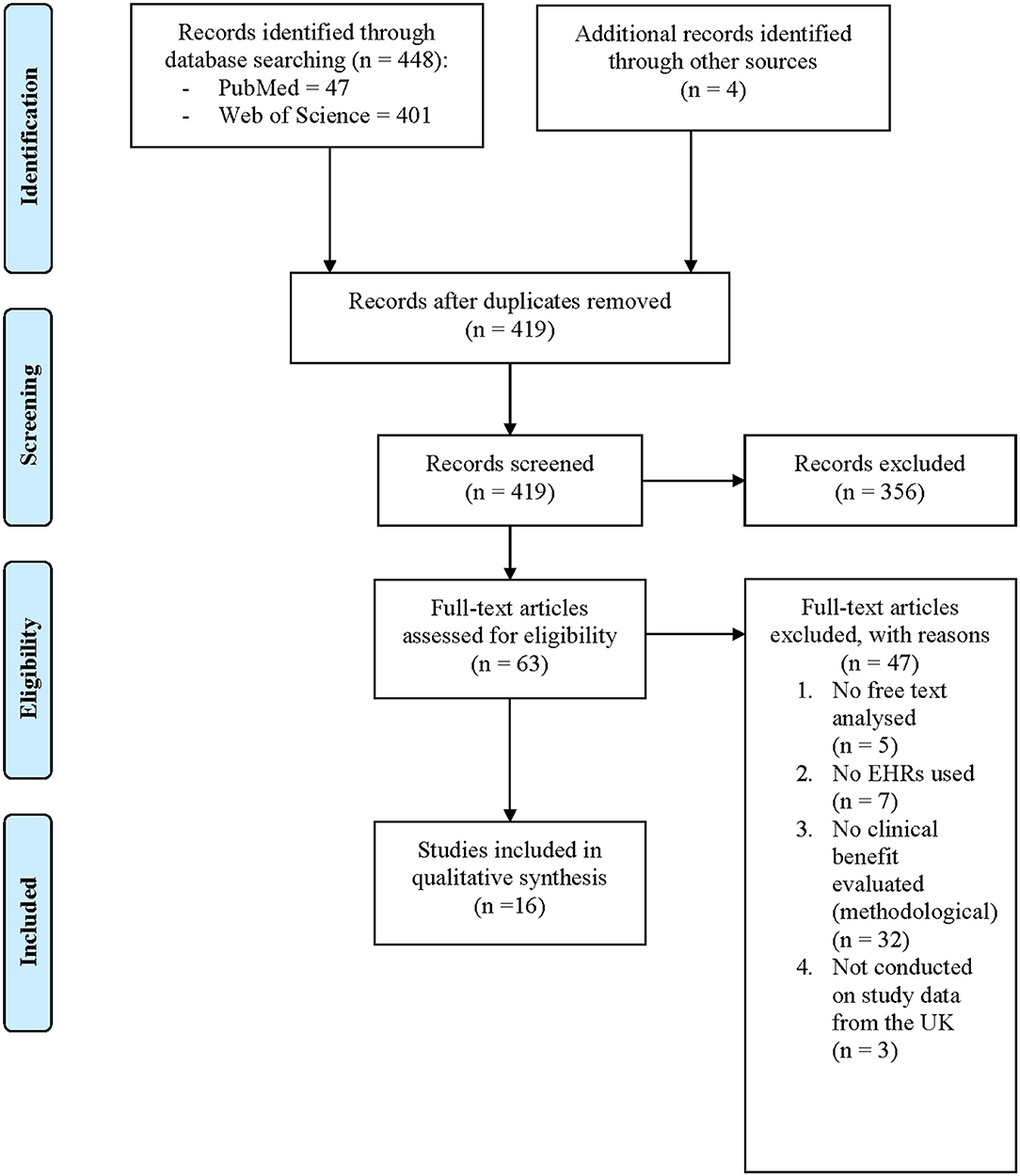
Frontiers The Potential of Research Drawing on Clinical Free Text to Bring Benefits to Patients in the United Kingdom: A Systematic Review of the Literature

Free Birthday Nutrition Facts PNG - Pretty Party & Crafty

The Library Genesis project: The easiest way to find full-text articles online (illegally)? – A Way of Happening
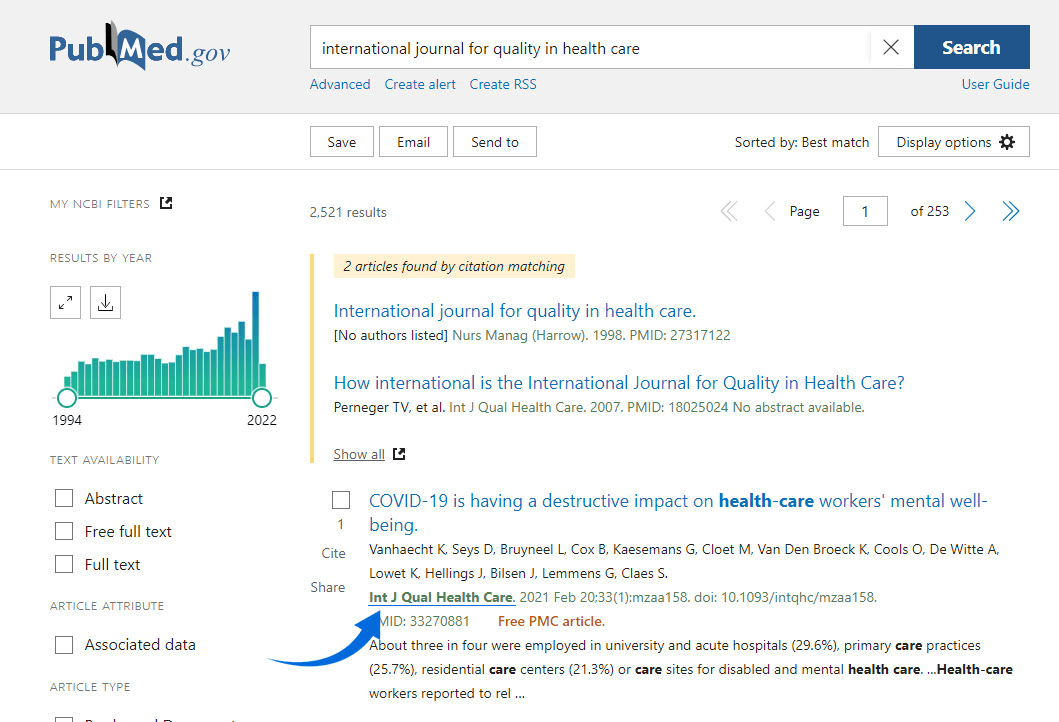
AMA Journal Citation
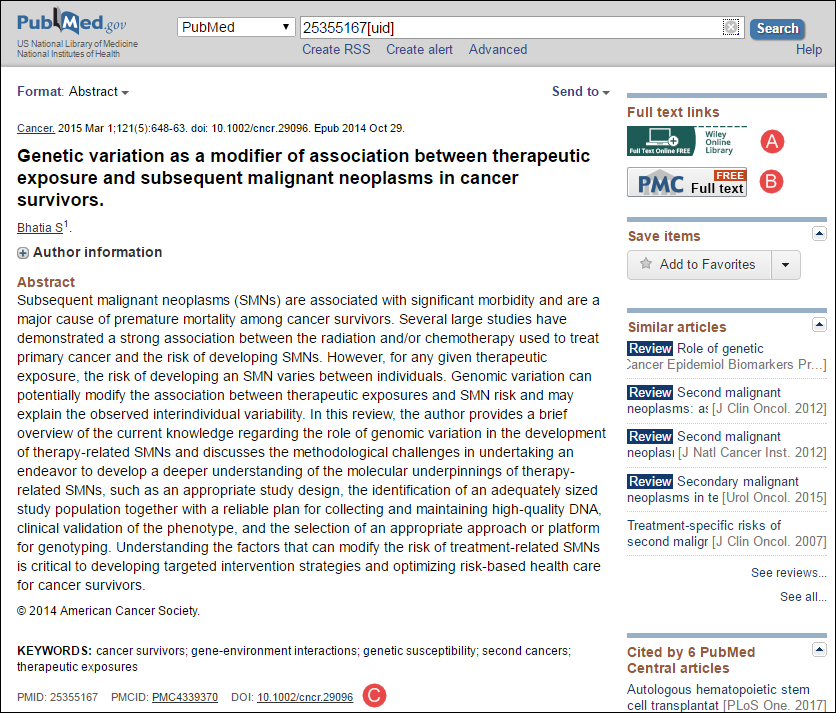
Institutional Repository LinkOut: A New Full Text Access Feature in PubMed. NLM Technical Bulletin. 2017 Mar–Apr
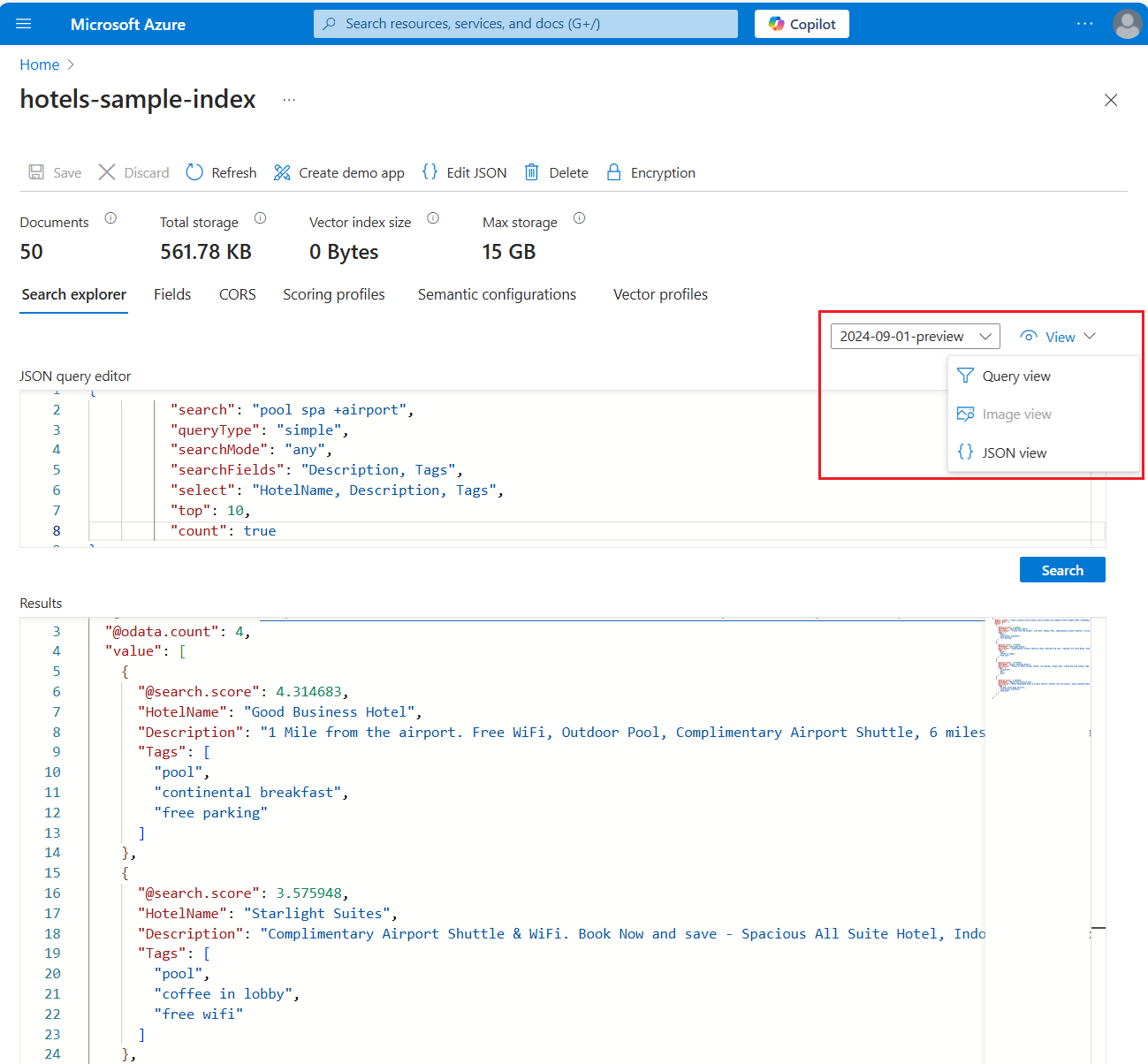
Full-text query how-to - Azure AI Search

Mining fall-related information in clinical notes: Comparison of rule-based and novel word embedding-based machine learning approaches - ScienceDirect
de
por adulto (o preço varia de acordo com o tamanho do grupo)