Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

PortSwigger Academy Server-side request forgery (SSRF) : 服务器

PortSwigger SSRF Labs. Hey all! This write-up is about my…

翻译]盲SSRF利用链术语表-腾讯云开发者社区-腾讯云

Exploiting Blind SSRF - Passion
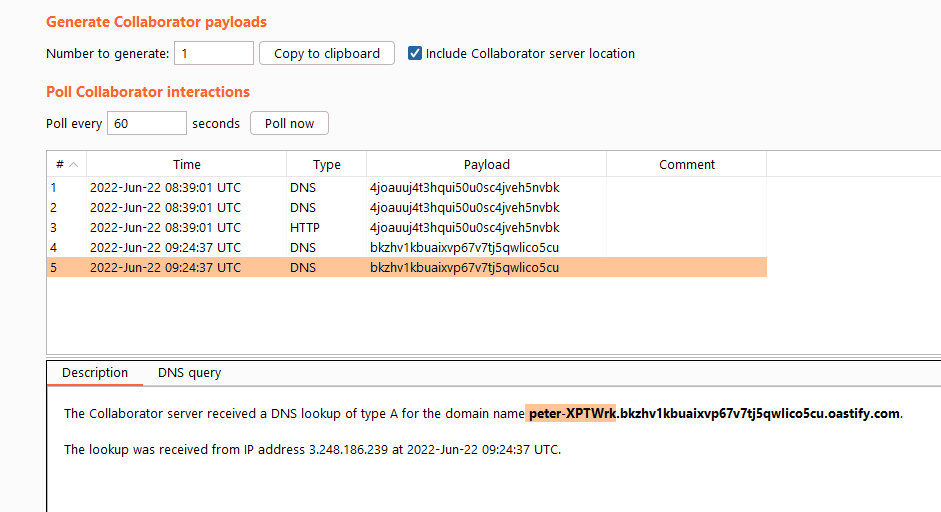
Web Application Hacking - Server-Side Request Forgery

0xdf hacks stuff CTF solutions, malware analysis, home lab

Server-Side Request Forgery (SSRF) - Intigriti
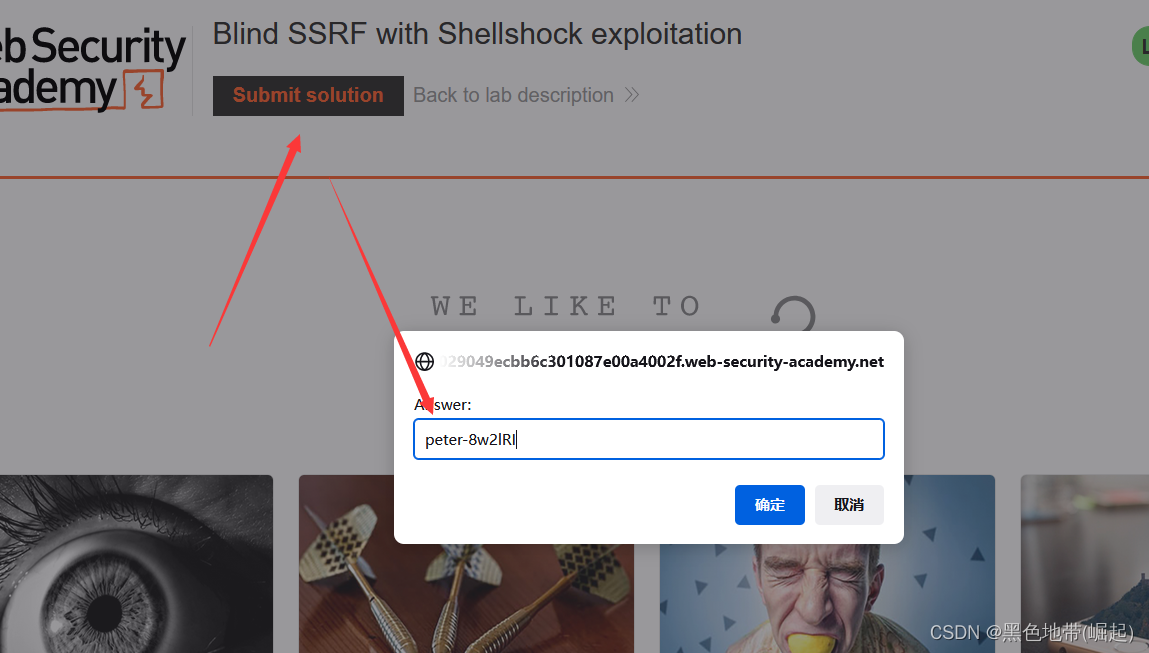
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云

PortSwigger SSRF Labs. Hey all! This write-up is about my…

Linux Exploitation – Shellshock exploit and privilege escalation
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
A Glossary of Blind SSRF Chains – Assetnote
Web Security Academy Series Course
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re
de
por adulto (o preço varia de acordo com o tamanho do grupo)







