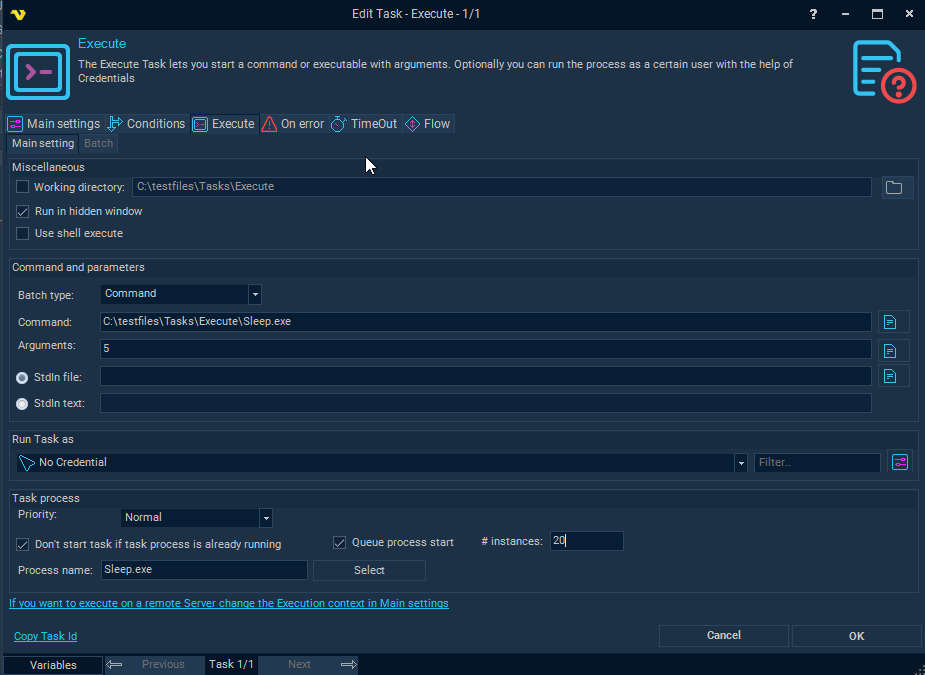
Windows Command Shell — Malware Execution, by Kamran Saifullah
Por um escritor misterioso
Descrição
In my previous article I have talked about Windows Registry Keys i.e. what are they and how attackers/adversaries can alter their values in order to stay persistent and keep on doing what they want…
Map of hebden bridge yorkshire

Search for Prevalence

Moin Khokhar, 🟣purple teamer on LinkedIn: #soc
Analyzing Malicious Word Documents - GISPP - Global InfoSec Pakistani Professionals
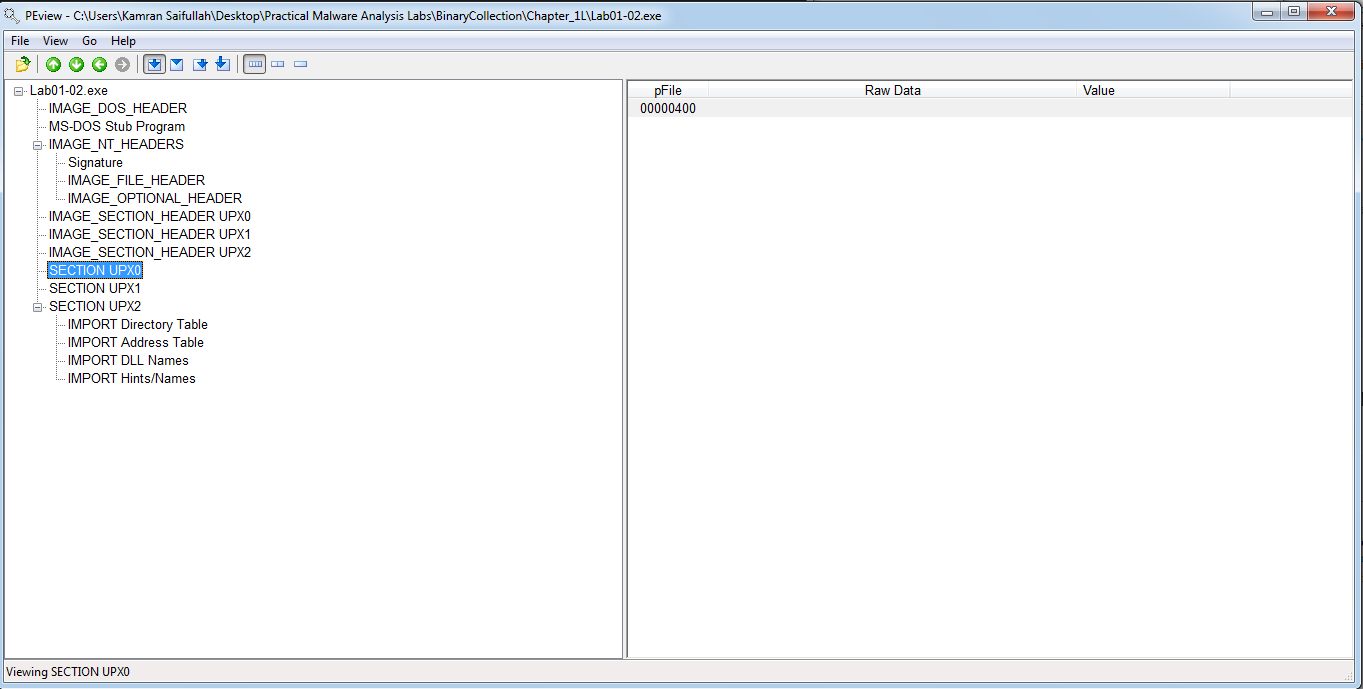
Practical Malware Analysis — Chapter 1 — Lab 1-2 — Solution, by Kamran Saifullah

Analyzing Malicious Word Documents - GISPP - Global InfoSec Pakistani Professionals
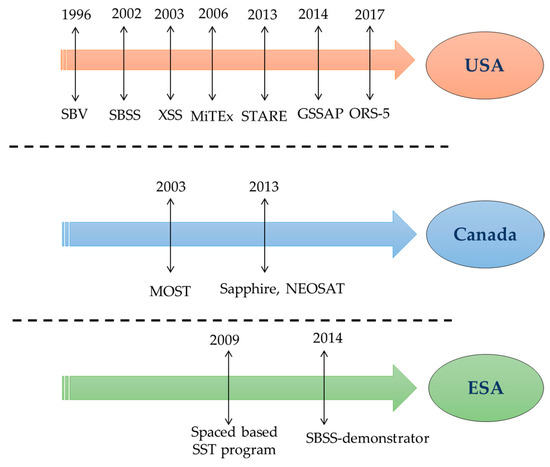
Remote Sensing March-2 2023 - Browse Articles

Memory Analysis and Forensics using Volatility - GISPP

DevTunnels Unleashed
de
por adulto (o preço varia de acordo com o tamanho do grupo)