Utilizing Morse Code to Evade Signature Based Detection Systems
Por um escritor misterioso
Descrição

Provenance-based Intrusion Detection Systems: A Survey
New phishing attack uses Morse code to hide malicious URLs
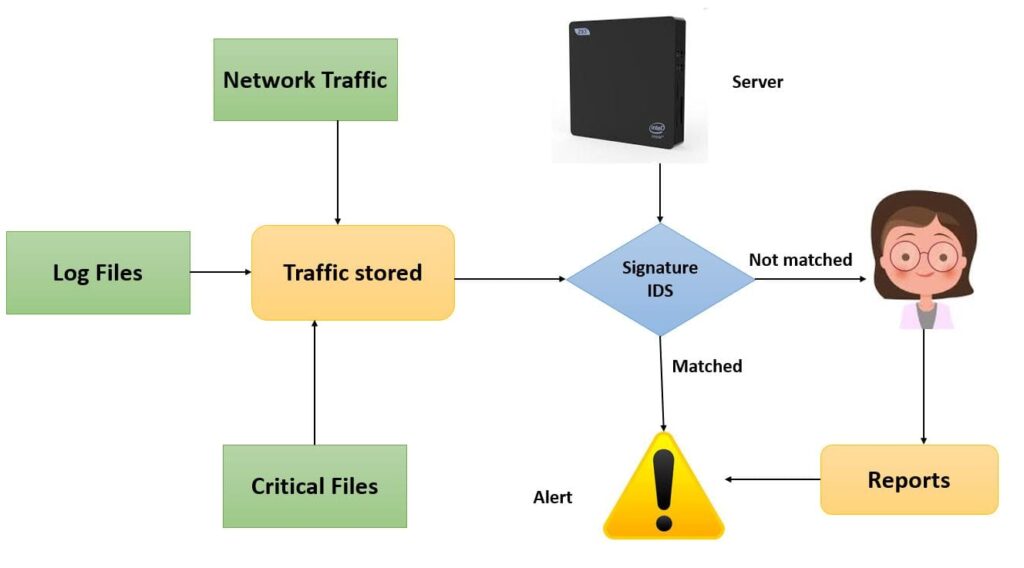
What is Intrusion Detection System [IDS]? - UseMyNotes

Attackers use Morse code, other encryption methods in evasive phishing campaign
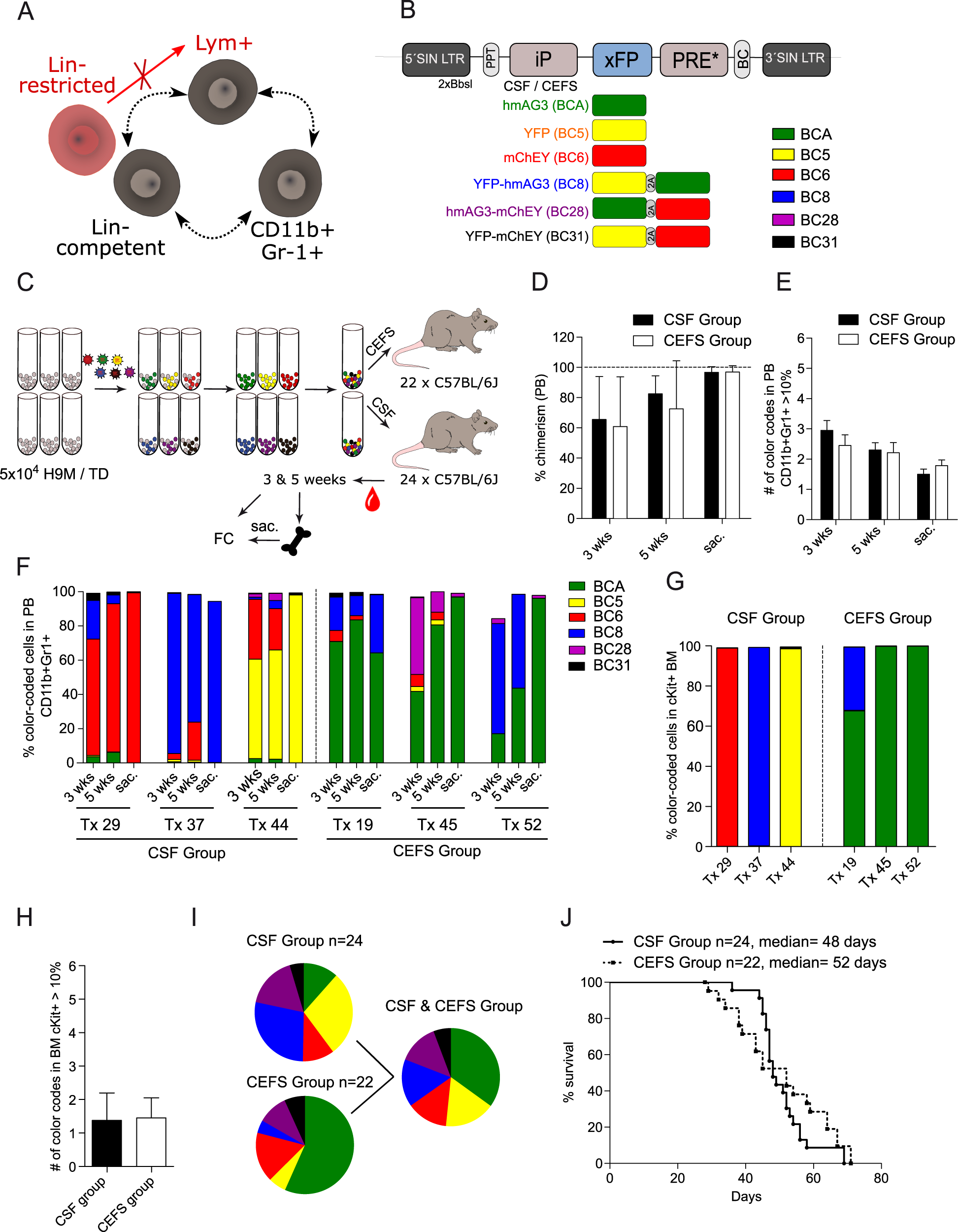
A pro B cell population forms the apex of the leukemic hierarchy in Hoxa9/Meis1-dependent AML
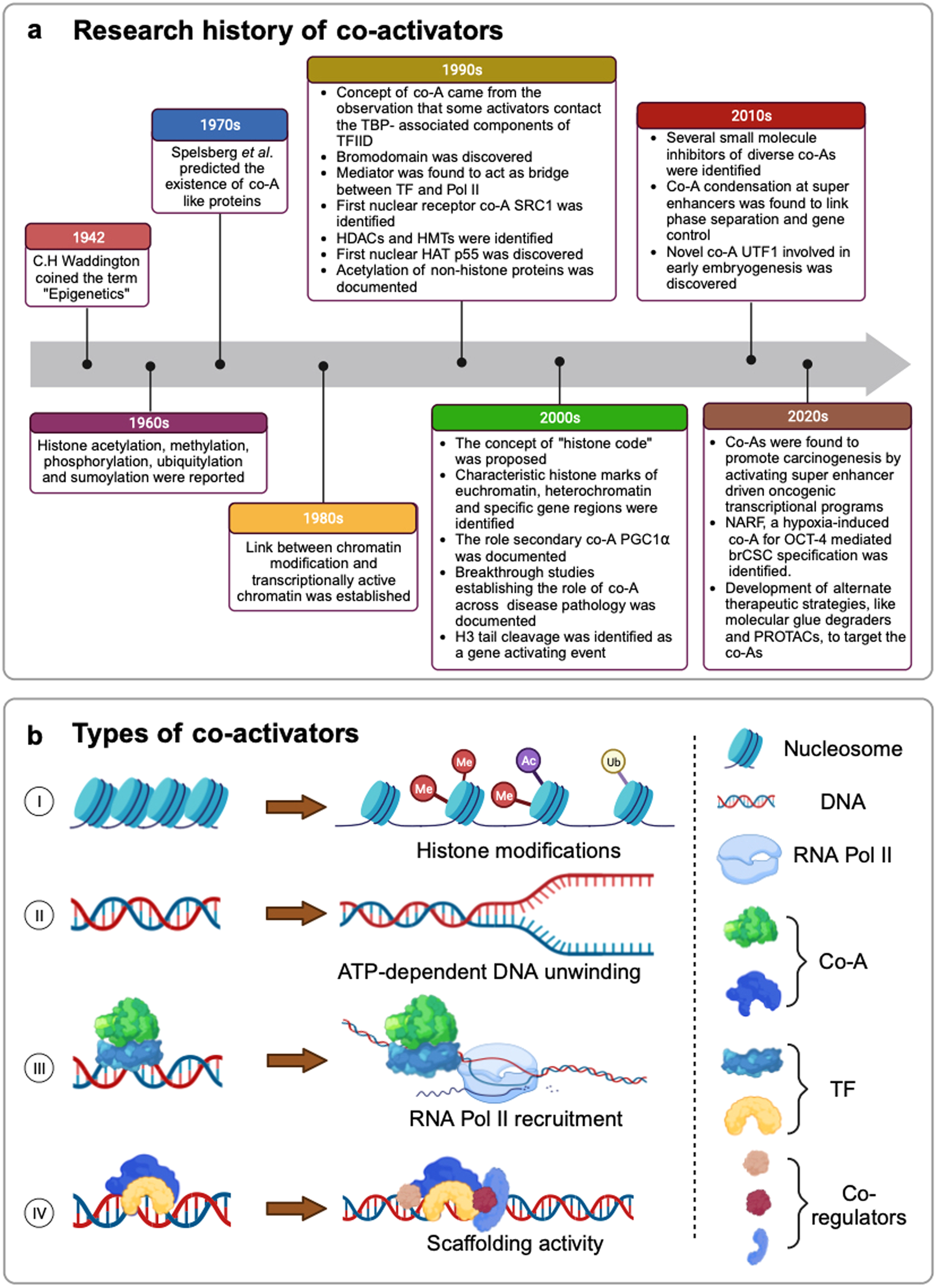
Transcriptional co-activators: emerging roles in signaling pathways and potential therapeutic targets for diseases

Multifunctional Conductive Double-Network Hydrogel Sensors for Multiscale Motion Detection and Temperature Monitoring

EXTERNAL - Whitepaper - How 3 Cyber ThreatsTransform Incident Response 081516

Morse Code Engineer – Gyokov Solutions

Attackers use Morse code, other encryption methods in evasive phishing campaign

Attackers Use Morse Code to Encode Phishing Attachments

Blind Spot: A Braille Patterned Novel Multiplex Lateral Flow Immunoassay Sensor Array for the Detection of Biothreat Agents
de
por adulto (o preço varia de acordo com o tamanho do grupo)







