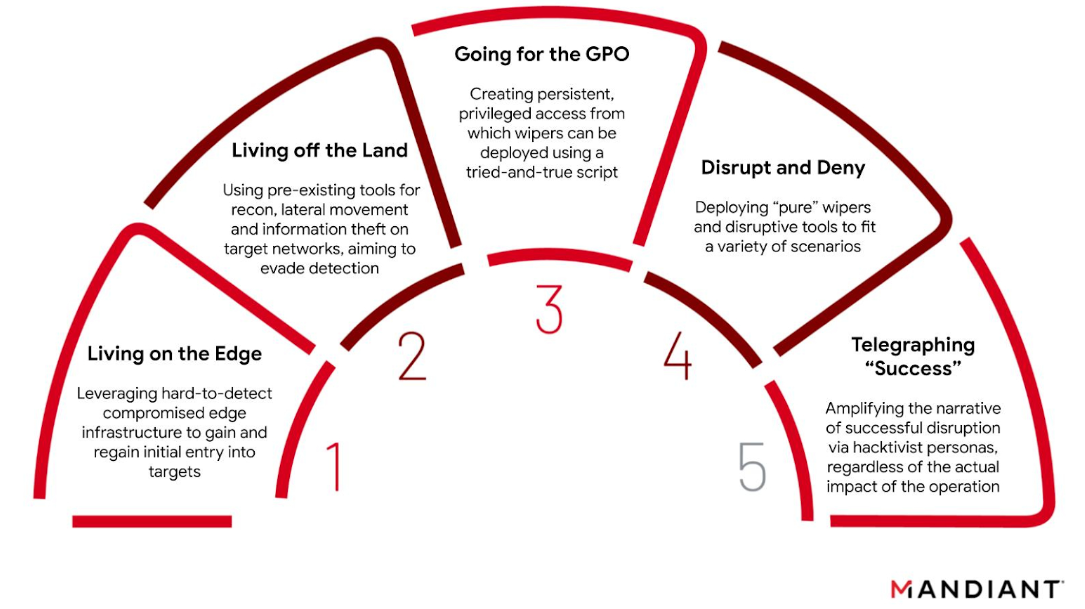
Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Descrição
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation

BlackLotus UEFI Bootkit Detection: Exploits CVE-2022-21894 to

Flax Typhoon Hackers Employ Advanced Tactics, Leveraging LOLBins

A Look At Some Real-World Obfuscation Techniques

PDF] Obfuscapk: An open-source black-box obfuscation tool for

The BatCloak obfuscation tool evades numerous AV solutions

Anti-virus Mechanisms and Various Ways to Bypass Antivirus

Enterprise data breach: causes, challenges, prevention, and future

Google Ads Spread Detection Evading Malware - SecureTeam

Cyble Detects STRRAT Version 1.6 Using Dual String Obfuscation

Analyzing the FUD Malware Obfuscation Engine BatCloak

Dark Web Profile: NoEscape Ransomware

macOS Payloads 7 Prevalent and Emerging Obfuscation Techniques

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors

Diversification and obfuscation techniques for software security
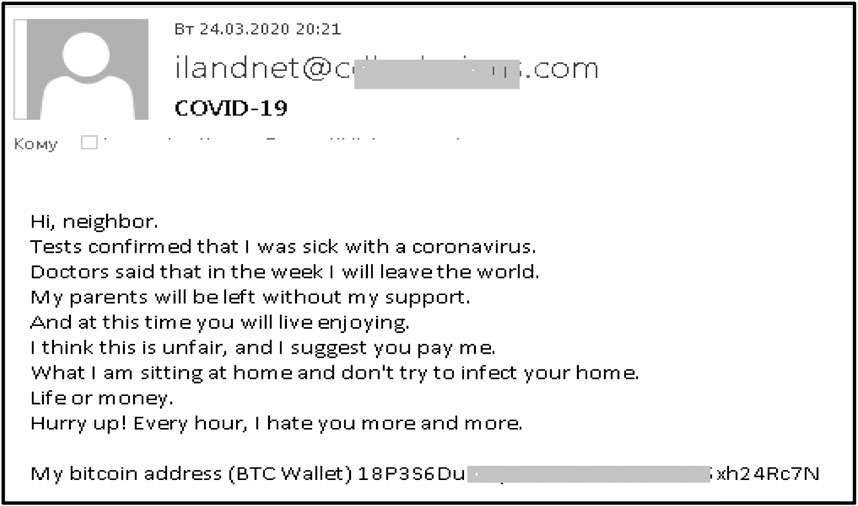
Frontiers Phishing Attacks: A Recent Comprehensive Study and a
de
por adulto (o preço varia de acordo com o tamanho do grupo)