Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
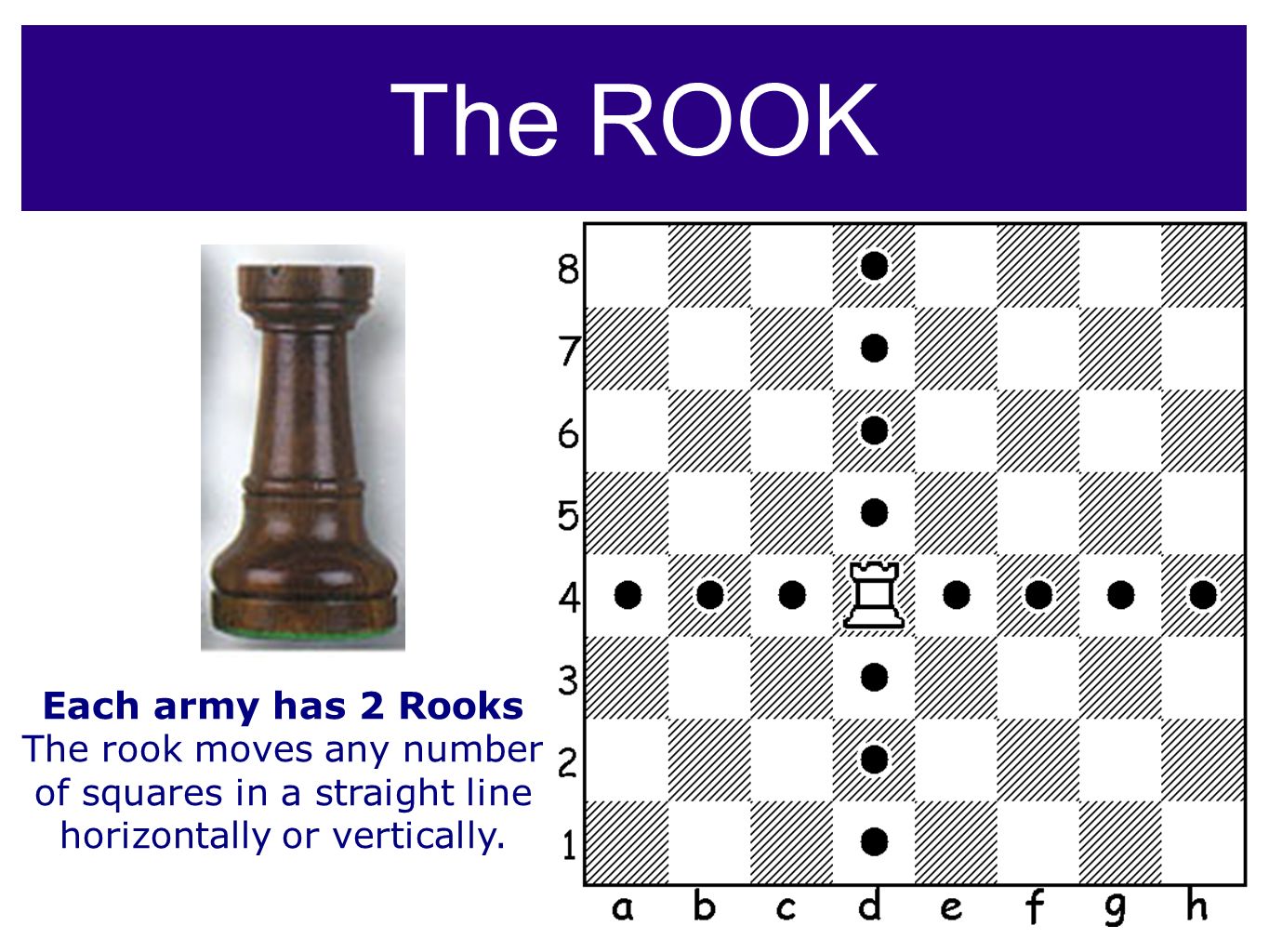
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
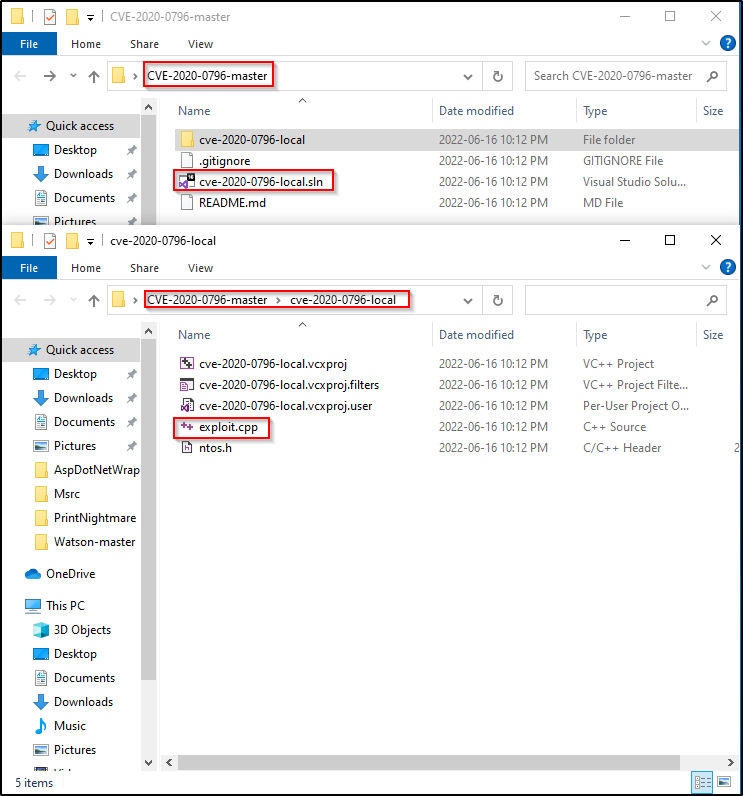
Kernel Exploits Part 2 – Windows Privilege Escalation

Flaw In Library Leaves Gnome Users Open to Remote Code Exploit

Exploit PDF Files, Without Vulnerability - 404 Tech Support

A 15-Year-Old Unpatched Python bug potentially impacts +350K projects

Open Files: How Do You Exploit them?

How I found the Grafana zero-day Path Traversal exploit that gave me access to your logs - Labs Detectify
Hack The Box — Starting Point “Responder” Solution, by Carla Ferreira, Rakulee
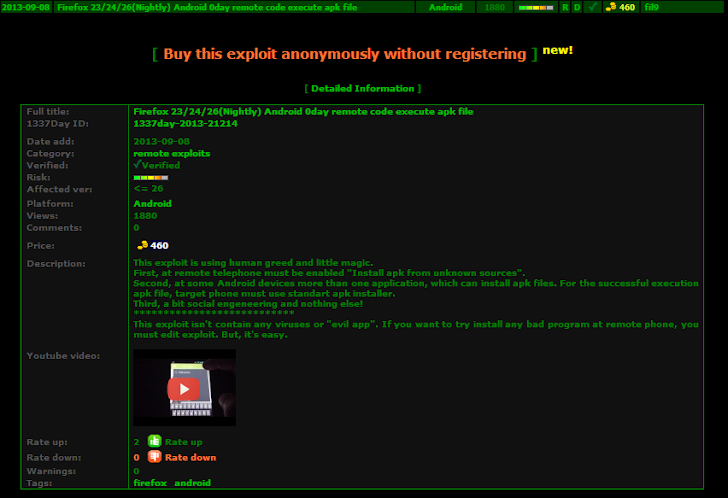
Russian Hacker put up an Android Firefox Zero-Day Exploit for Sale

CVE-Vulnerability-Information-Downloader - Downloads Information From NIST (CVSS), First.Org (EPSS), And CISA (Exploited Vulnerabilities) And Combines Them Into One List
Exploit Windows PC using Open-FTPD 1.2 Arbitrary File Upload - Hacking Articles
de
por adulto (o preço varia de acordo com o tamanho do grupo)