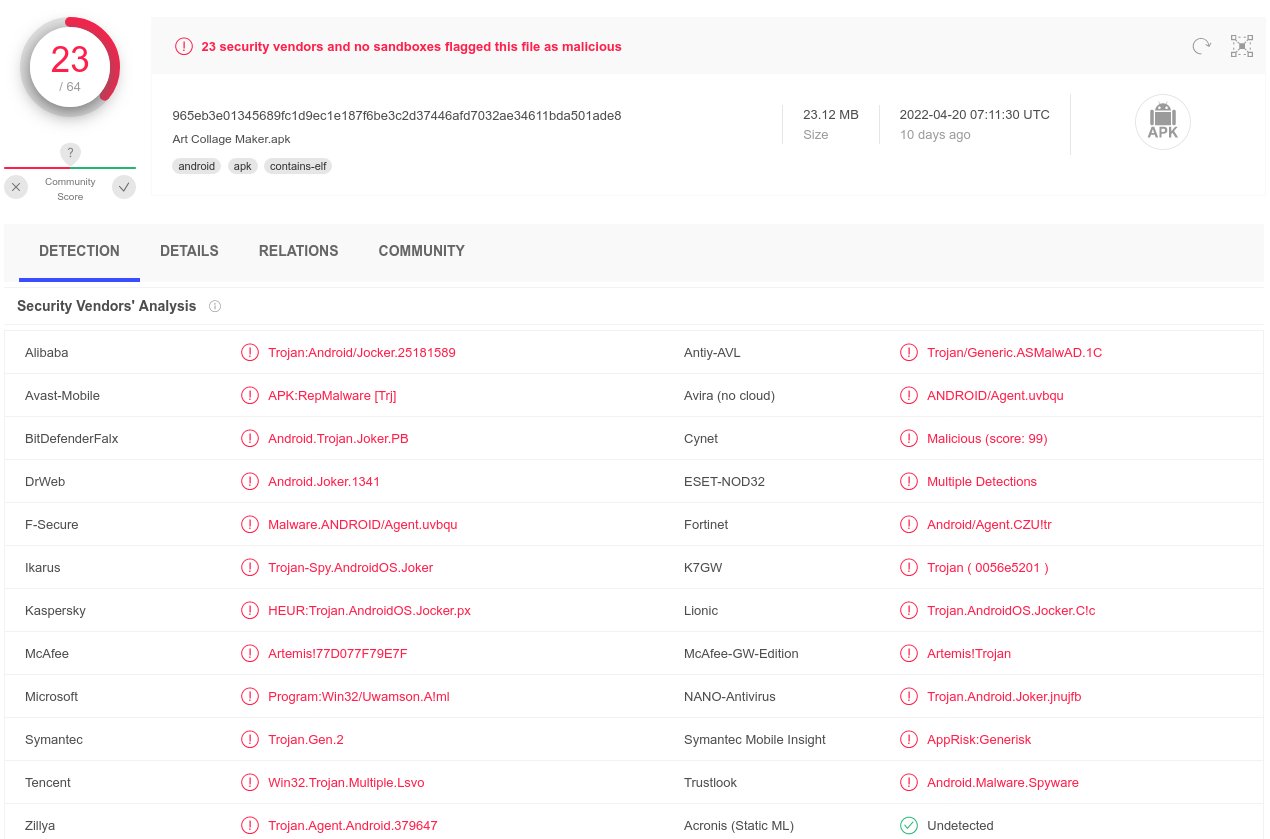
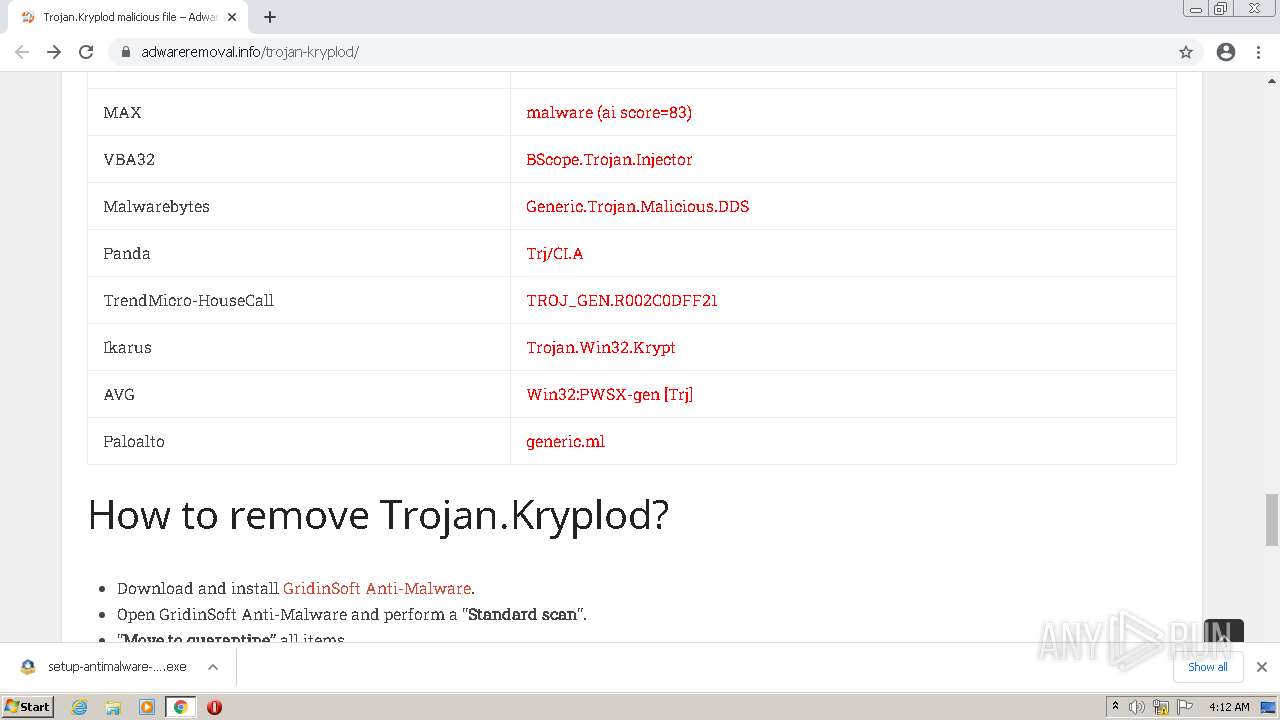
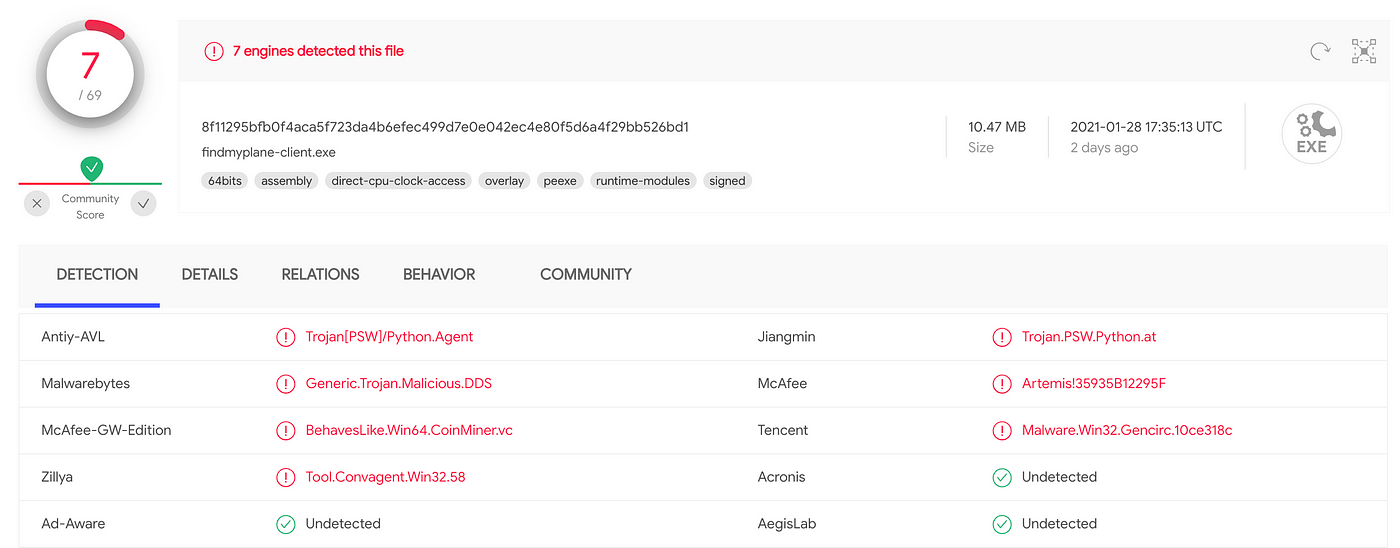
Trojan.PDF.PHISH.TIAOOHQI - Threat Encyclopedia
Por um escritor misterioso
Descrição
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.It redirects browsers to certain sites.

PDF) Spyware and Trojan Horses IJSRD - International Journal for

PDF) THE TROJAN WAR David Tew
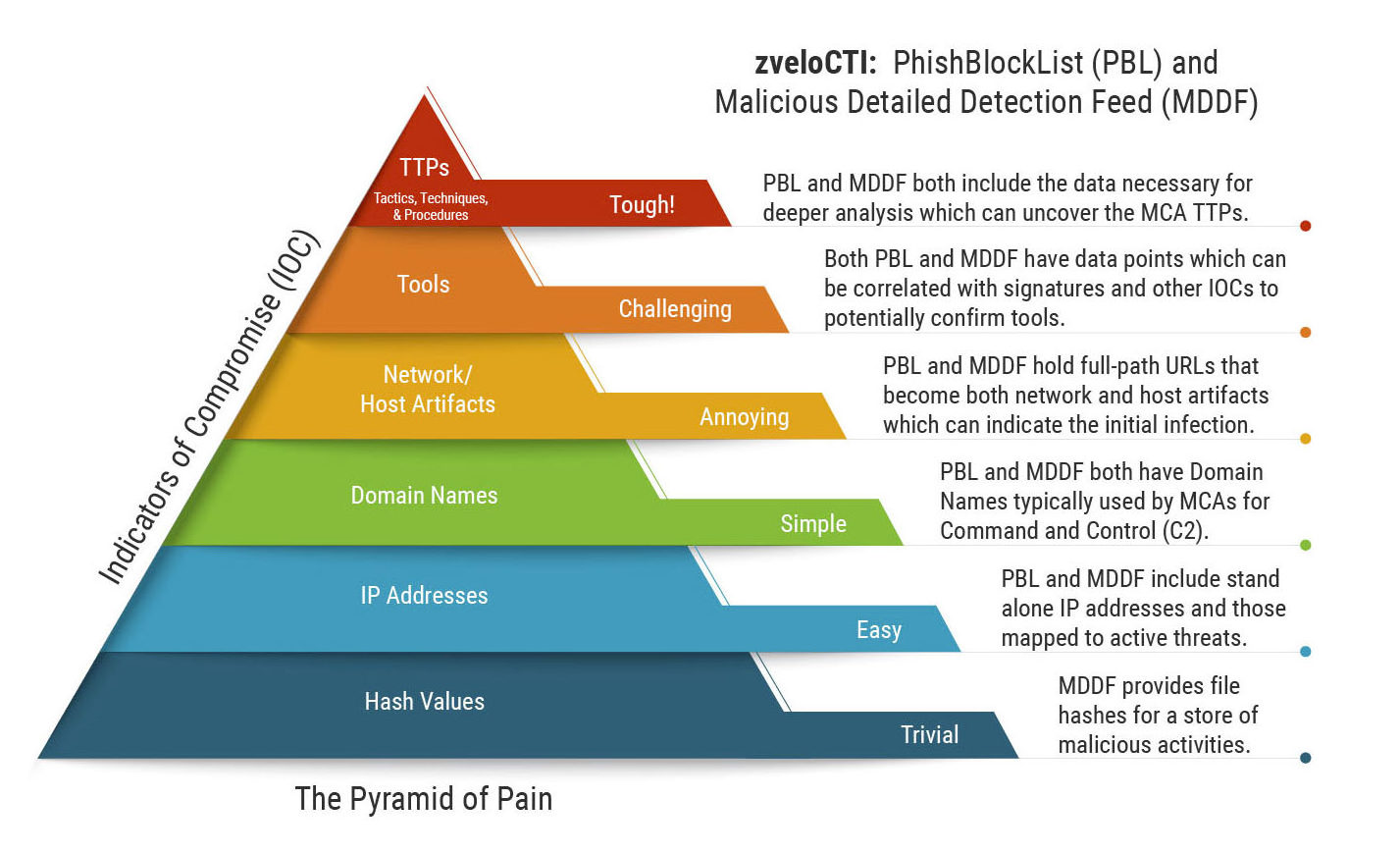
Mapping zveloCTI to the Pyramid of Pain IOCs for IR & Threat Hunting
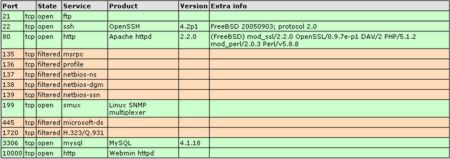
Gozi Trojan Threat Analysis

Analysis and Reverse Engineering of a Banking Trojan Malware from
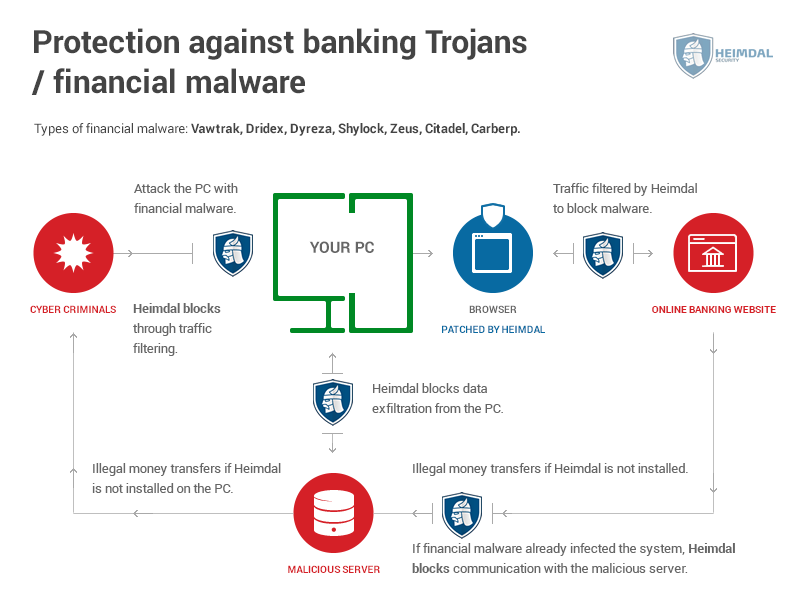
What Is a Trojan Virus? Definition, Prevention & Removal Tips
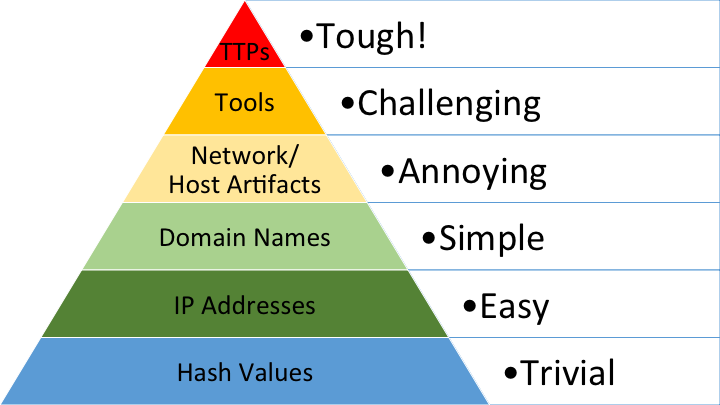
swannysec · Musings on InfoSec
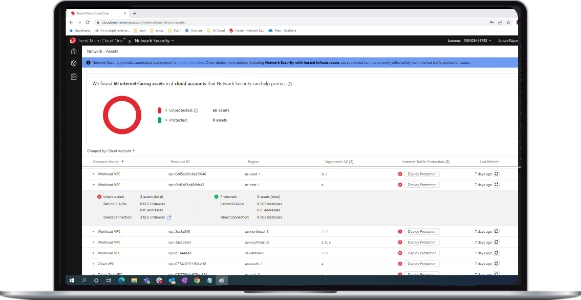
Threat Encyclopedia

PDF) THE TROJAN WAR David Tew

PDF) THE TROJAN WAR David Tew
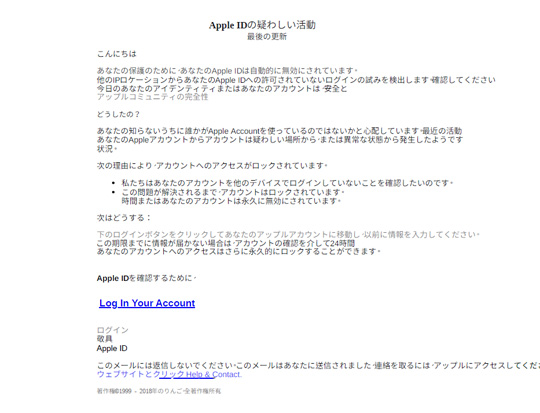
Trojan.PDF.PHISH.TIAOOHDR - 脅威データベース
TOITOIN Trojan: A New Multi-Stage Attack Targeting LATAM
.png)
Chinese hackers target script kiddies with info-stealer trojan

PDF) THE TROJAN WAR David Tew

Security Books & Articles: Must-Read List From InfoSec Experts
de
por adulto (o preço varia de acordo com o tamanho do grupo)