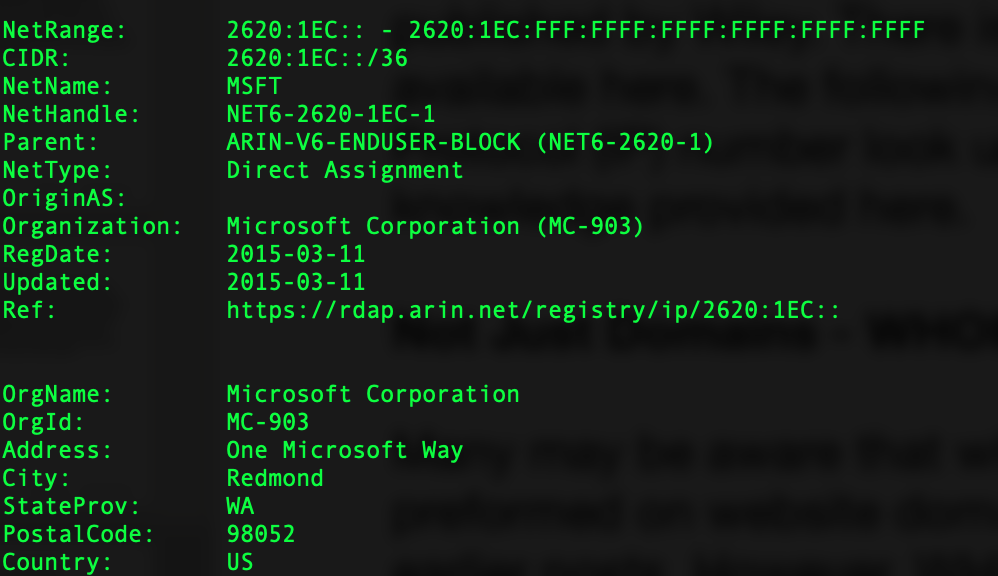
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Ethical Hacking Learning Path — A Complete Roadmap, by crawsecurity

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Hackbun

Malicious Life Podcast: Wild West Hackin' Fest
Ethical Hacking - How to start

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack

VMware Horizon servers are under active exploit by Iranian state hackers

Iranian hacker claims he acted alone in stealing digital SSL certificates, Hacking

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS

Postman Hack The Box (HTB). Hello guys today Postman got retired by…, by Musyoka Ian
de
por adulto (o preço varia de acordo com o tamanho do grupo)