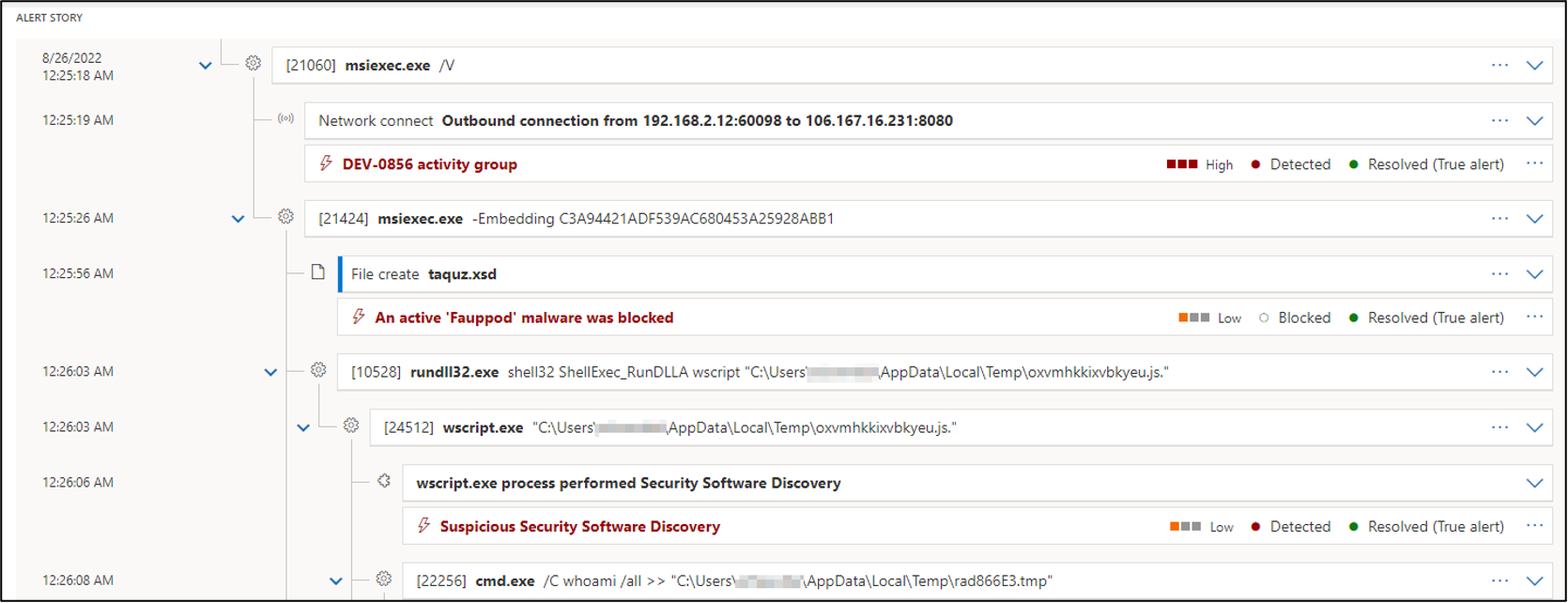
Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
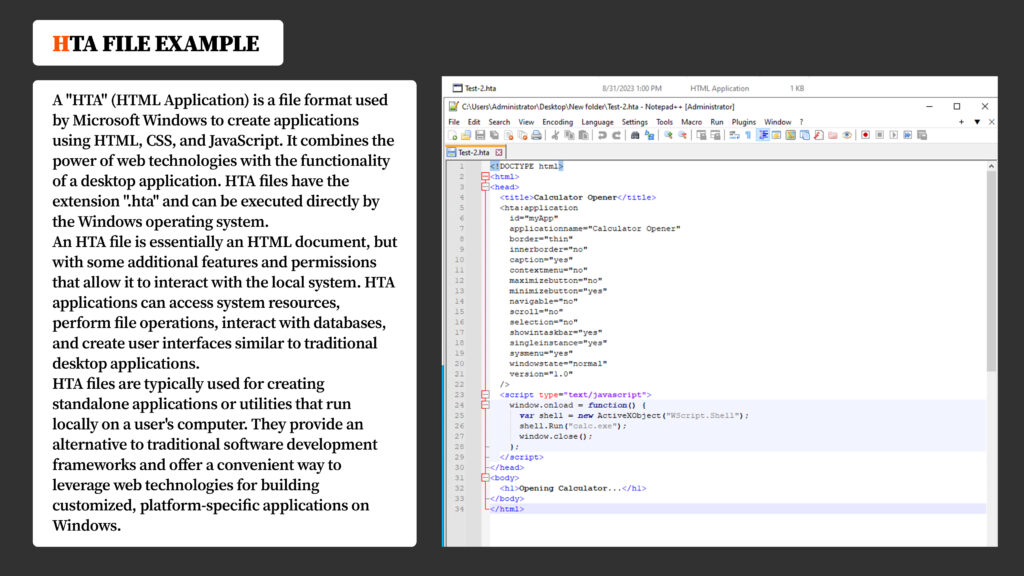
Descrição
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
eSentire eSentire Threat Intelligence Malware Analysis: Raspberry…

The Duqu 2.0: Technical Details

Cybereason auf LinkedIn: Rundll32: The Infamous Proxy for Executing Malicious Code
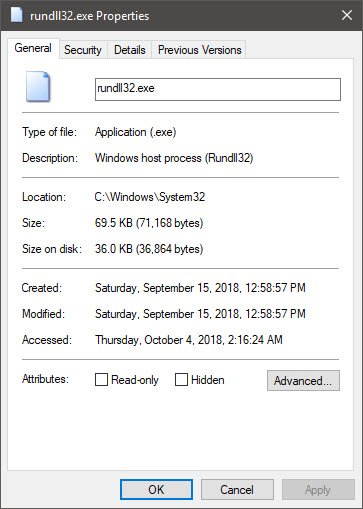
What is rundll32.exe process? Is it a virus?

The Windows Process Journey — rundll32.exe (Windows Host Process), by Shlomi Boutnaru, Ph.D.
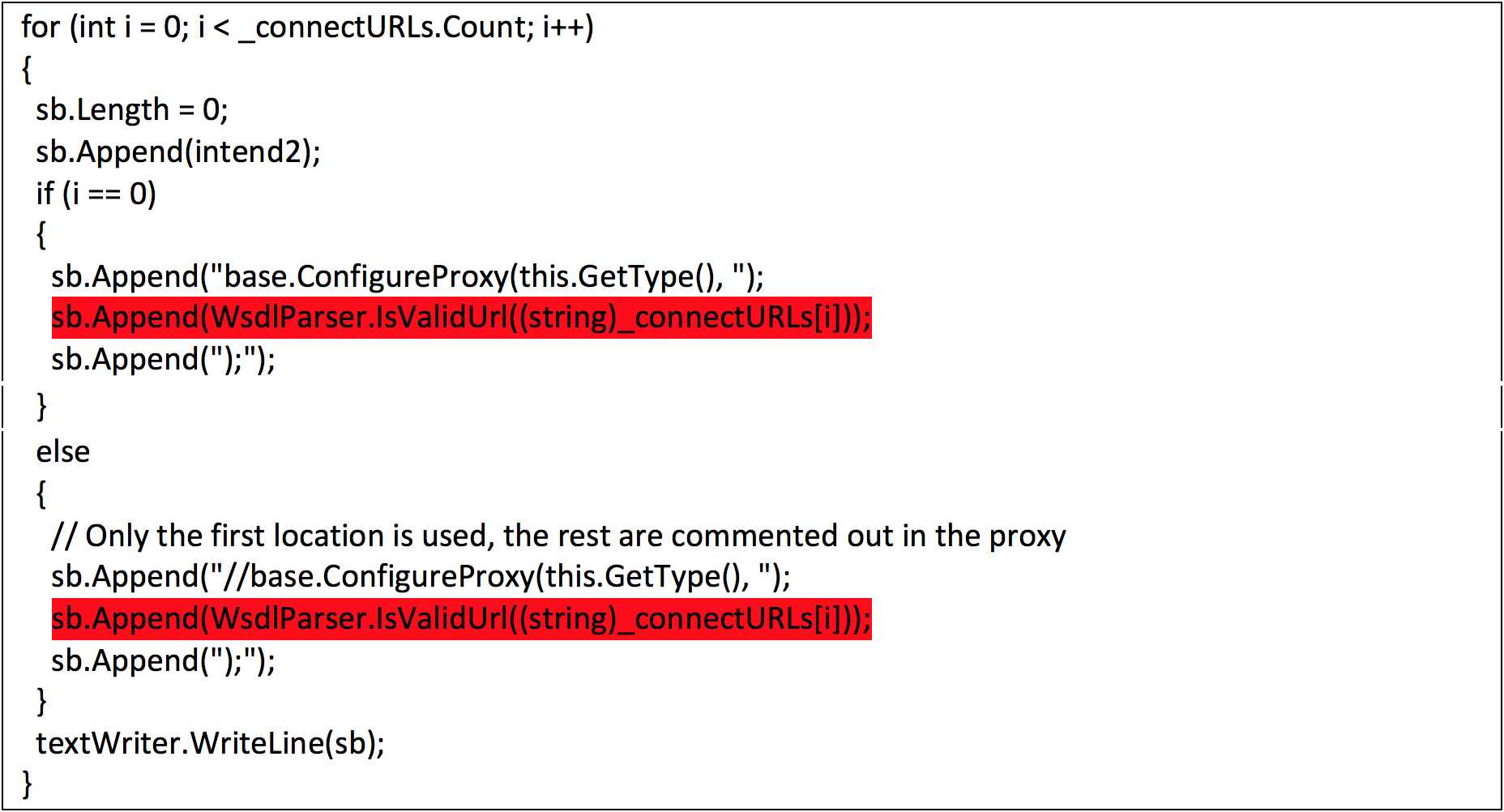
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distr - exploit database

Microsoft and FireEye Reveal New Malware Samples Tied to SolarWinds Attackers - SOC Prime

AgentTesla Information-Stealing Malware Delivered in Cyber-Attacks on Ukrainian Government Entities - SOC Prime

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks
APT Profile: Sandworm - SOCRadar® Cyber Intelligence Inc.
System Binary Proxy Execution Rundll32, Nordic Defender

Virus Bulletin on X: The Cybereason Blue Team describe how Microsoft's rundll32.exe tool, which allows code to be loaded and executed, is often used by adversaries during their offensive operations. /
System Binary Proxy Execution Rundll32, Nordic Defender
de
por adulto (o preço varia de acordo com o tamanho do grupo)