Ransomware: Build Your Own Ransomware, Part 1
Por um escritor misterioso
Descrição
Welcome back, my aspiring cyberwarriors! Ransomware is rapidly becoming the most important form of malware afflicting our digital systems. Companies across the globe are being hit with various forms of malware including the new variant, Snake, designed specifically for SCADA/ICS systems. The Colonial Pipeline in the US was shutdown for nearly a week before paying a $5 million ransom, demonstrating the danger of this ransomware to industrial systems and a nation

Build Your Own Ransomware (Project Root) Behind Enemy Lines Part 2 - SentinelOne

Ransomware Attacks Increasingly Targeting Manufacturers - NAM
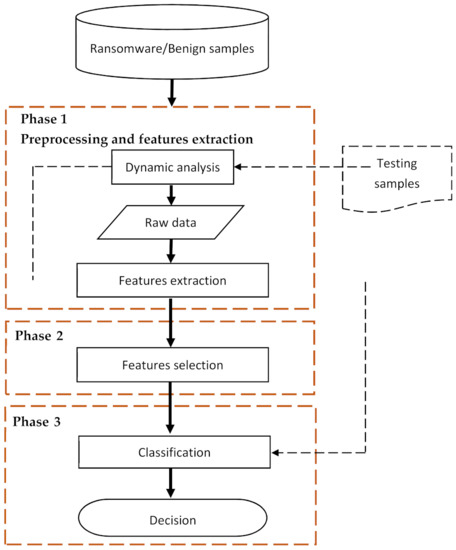
Sensors, Free Full-Text
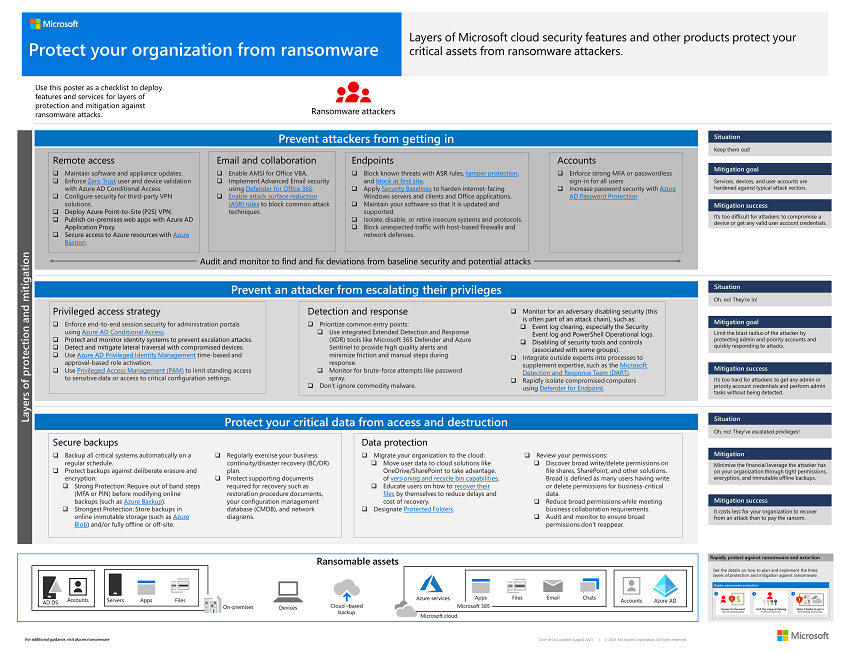
Human-operated ransomware

Life Cycle of a Ransomware Attack

7 Steps to Help Prevent & Limit the Impact of Ransomware

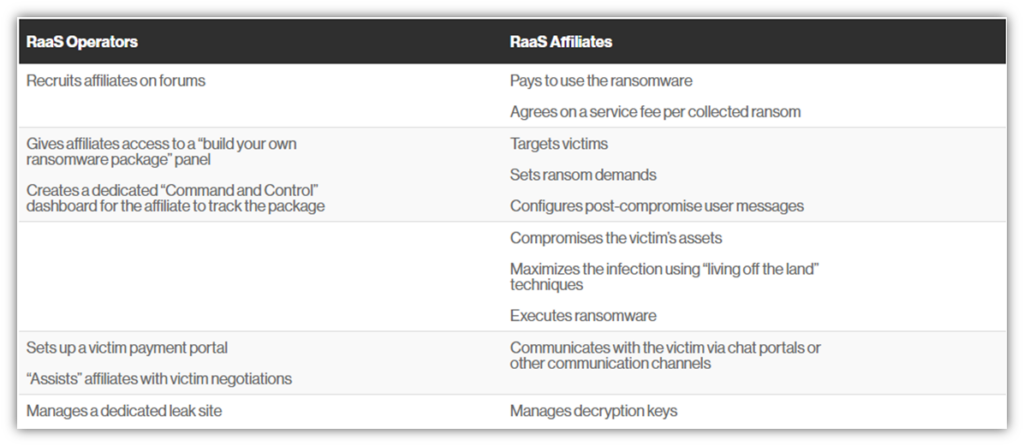
Cyble — 'NoEscape' Ransomware-as-a-Service (RaaS)

Ransomware: Build Your Own Ransomware, Part 1

Ransomware: Publicly Reported Incidents are only the tip of the iceberg — ENISA

Build Your Own Ransomware (Project Root) Behind Enemy Lines Part 2 - SentinelOne
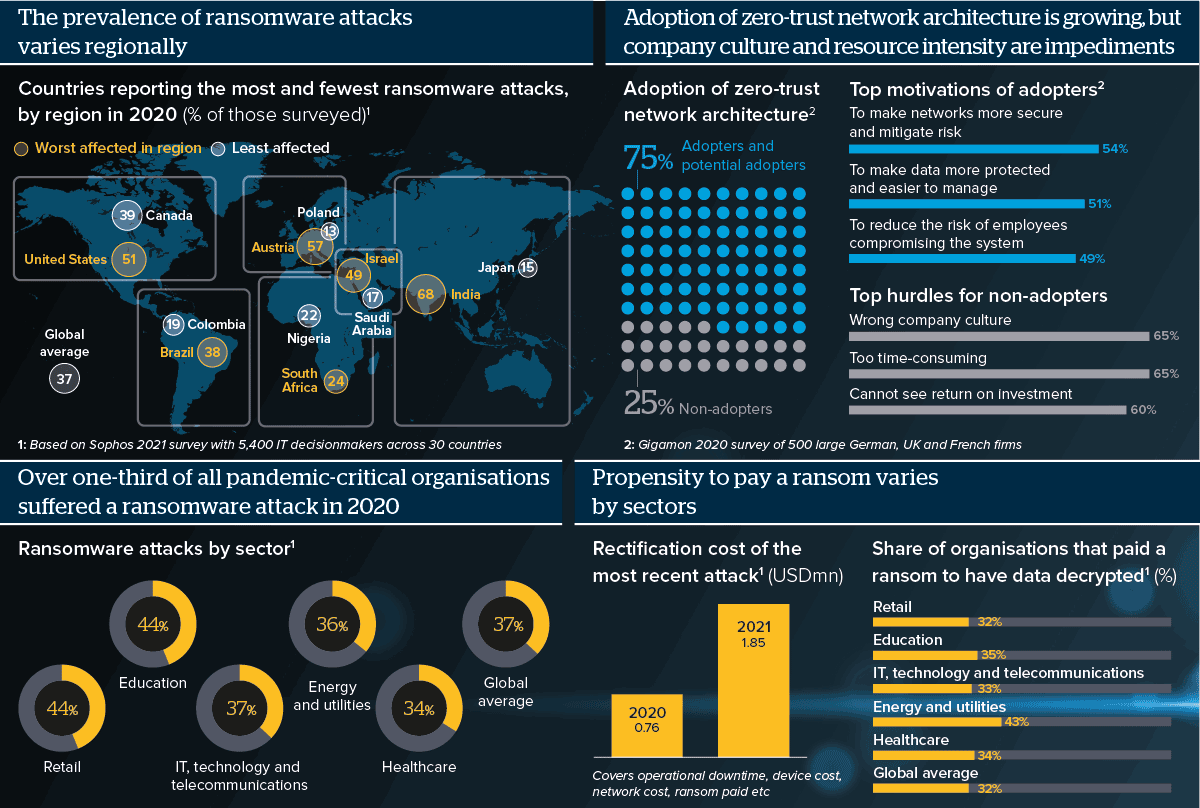
US pipeline hack to make ransomware risks a priority - Oxford Analytica Daily Brief
What Is Ransomware & How Does Ransomware Work? - Hashed Out by The SSL Store™
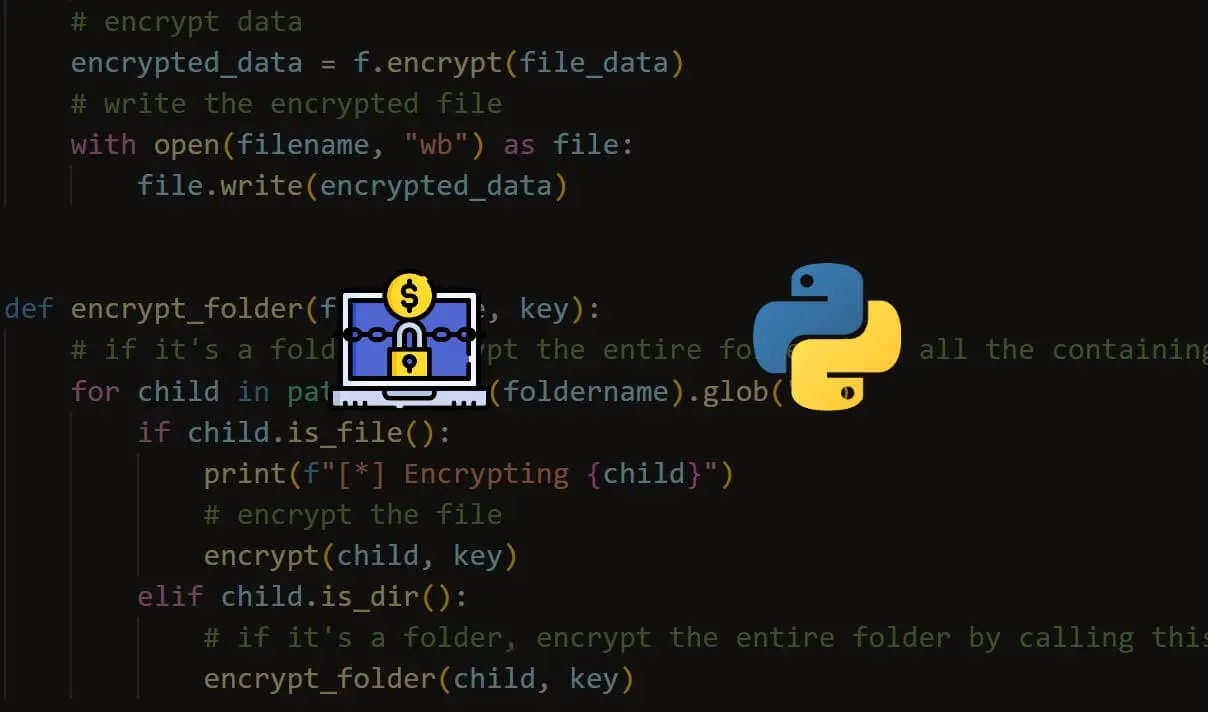
How to Make a Ransomware in Python - The Python Code
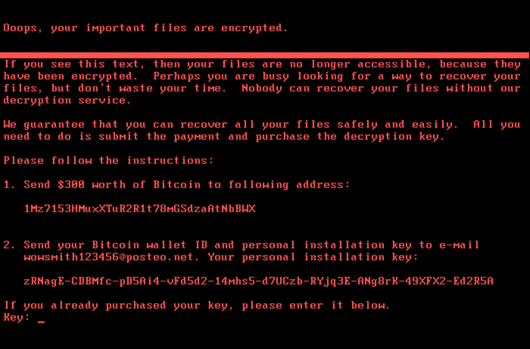
NotPetya Ransomware Attack [Technical Analysis]

Top tips: 3 ways to defend your critical IT infrastructure against ransomware
de
por adulto (o preço varia de acordo com o tamanho do grupo)