SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Descrição
As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Companies on alert after apparent hack of cloud-based security camera service

Spyder Loader: Malware Seen in Recent Campaign Targeting Organizations in Hong Kong

Cobalt Strike, Breaking Cybersecurity News

Cobalt Strike, Breaking Cybersecurity News
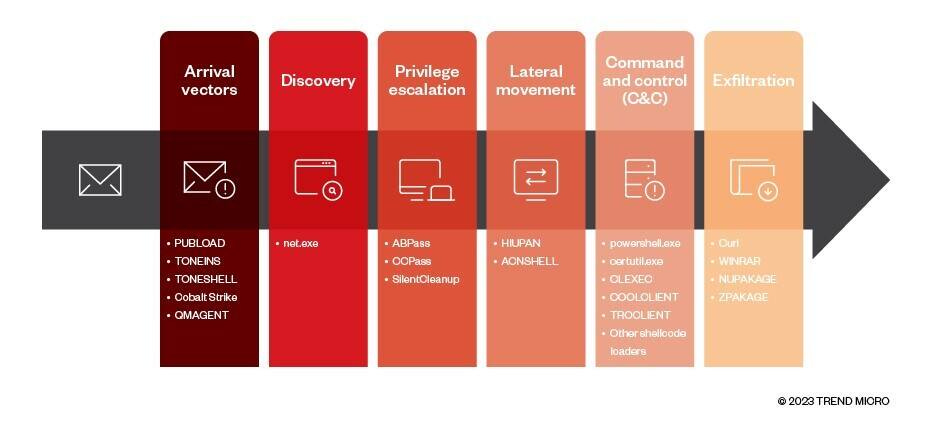
Bluepurple Pulse: week ending March 26th - by Ollie

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers : r/RedPacketSecurity

Cyber Security for Critical Infrastructure Protection - SCADAhacker

Telerik exploitation. Cloud storage re-up attacks. Phishing tackle. Cyber developments in Russia's hybrid war.

New Godlua Backdoor Found Abusing DNS Over HTTPS (DoH) Protocol - Noticias de seguridad - Trend Micro ES

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 17 March 2023
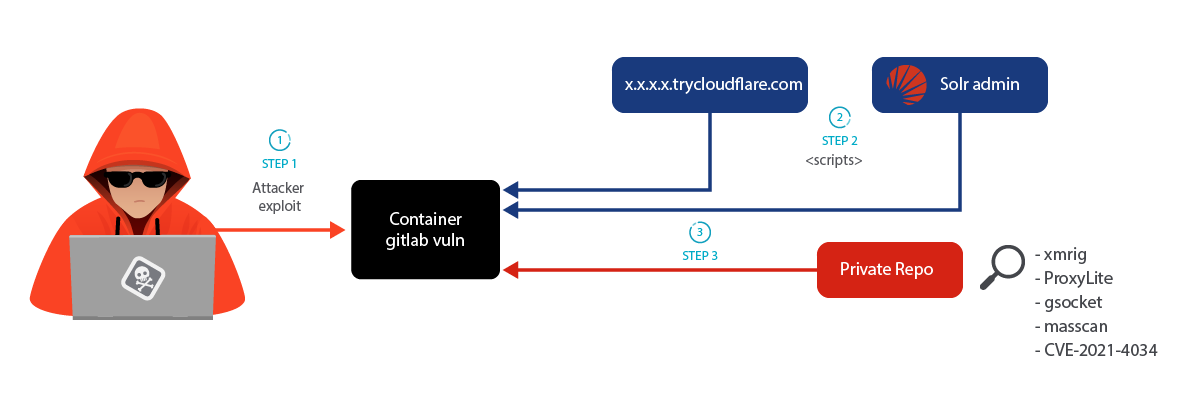
LABRAT: Stealthy Cryptojacking and Proxyjacking Campaign Targeting GitLab – Sysdig

Chinese Silkloader cyber attack tool falls into Russian hands
de
por adulto (o preço varia de acordo com o tamanho do grupo)



/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/2/j/YeifLGRRe8XH72fRXvLA/2012-04-24-batman-e-arlequina-em-arkham-city.jpg)
