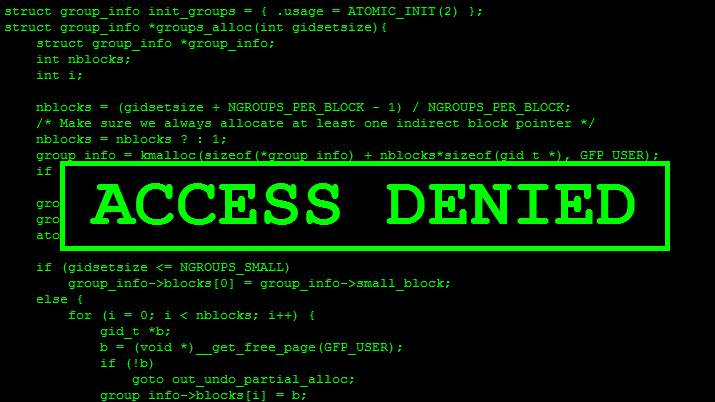
What is Sub7 & What Hackers Can Do With It
Por um escritor misterioso
Descrição
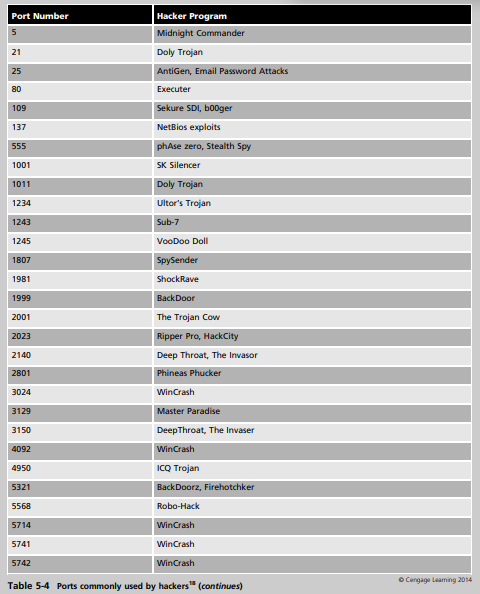
Solved) - Using Table 5-4 and a Web browser, search on a few of the port (1 Answer)

Alton Johnson, OSCP, OSCE on LinkedIn: #vonahisec #automation
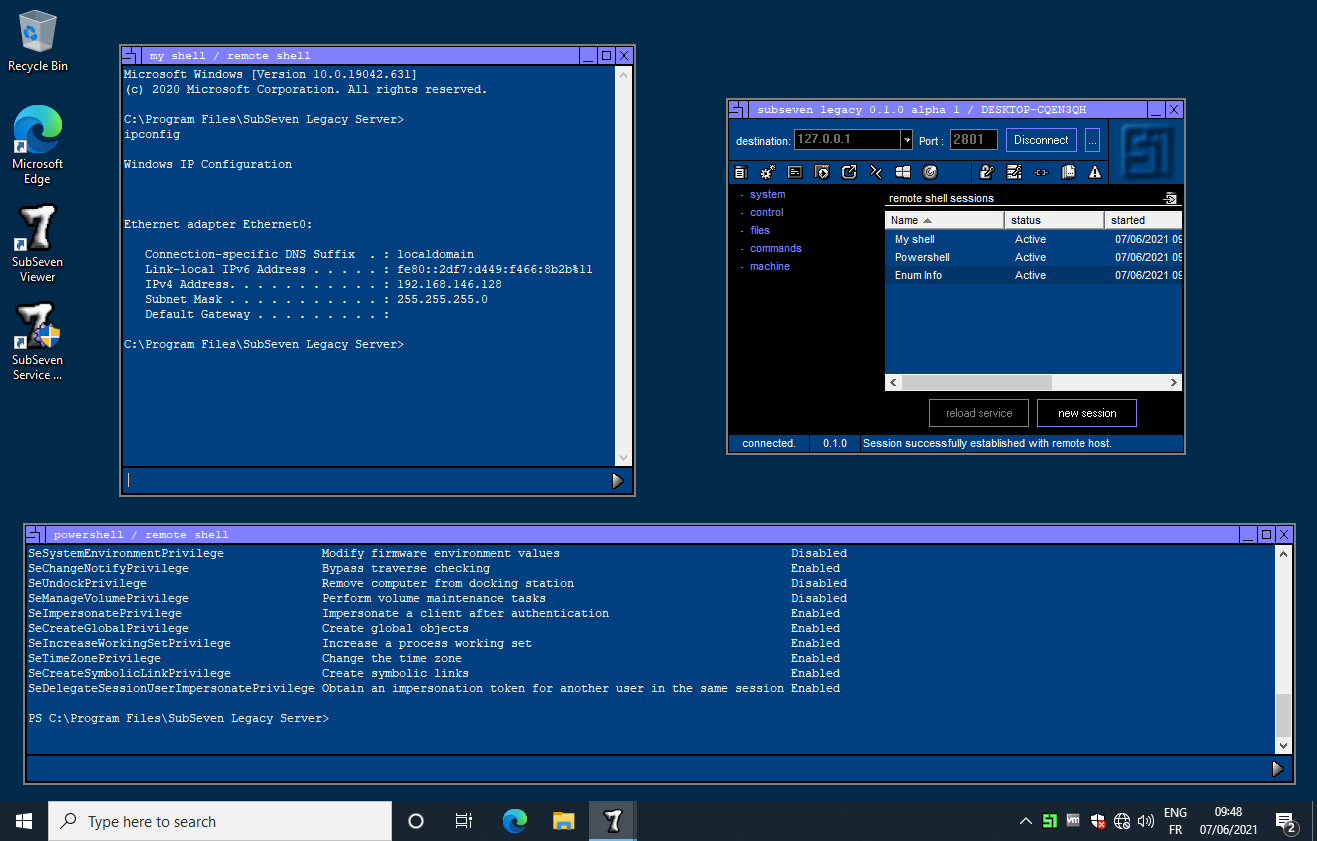
A Malware retrospective: SubSeven, by Jean-Pierre LESUEUR (Microsoft MVP), Phrozen

Hacking Exposed: Network Security Secrets & by Joel Scambray

An Introduction to Offensive Cybersecurity: A Webinar - The Association of Governance, Risk and Compliance (AGRC)

Remote access tool

Three Archaic Backdoor Trojan Programs That Still Serve Great Pranks

From pranks to APTs: How remote access Trojans became a major security threat
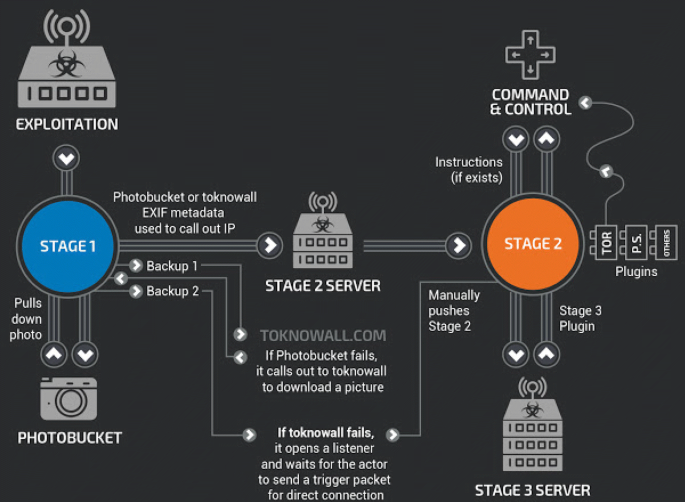
Cyber espionage through Botnets

Guide To Hacking With Sub7, PDF, Computer Virus
de
por adulto (o preço varia de acordo com o tamanho do grupo)