Windows JavaScript zero-day, Iran-based hack-and-leak, METRO
Por um escritor misterioso
Descrição
Exploited Windows zero-day lets JavaScript files bypass Mark of the Web security warnings According to Bleeping Computer, this has already been seen in ransomware attacks. Windows includes a security feature called Mark-of-the-Web (MoTW) that flags a file as having been downloaded from the Internet

Webinars Archives - DarkOwl, LLC

Security Vulnerability in WinRAR Allows Hackers to Execute Programs via Opening RAR Archives

Hornetsecurity IT Security Incident Center - Hornetsecurity

Kubernetes Ransomware Protection with Kasten K10 v4.0 - Storcom, Lombard, Illinois, United States of America

Timeline of computer viruses and worms - Wikipedia
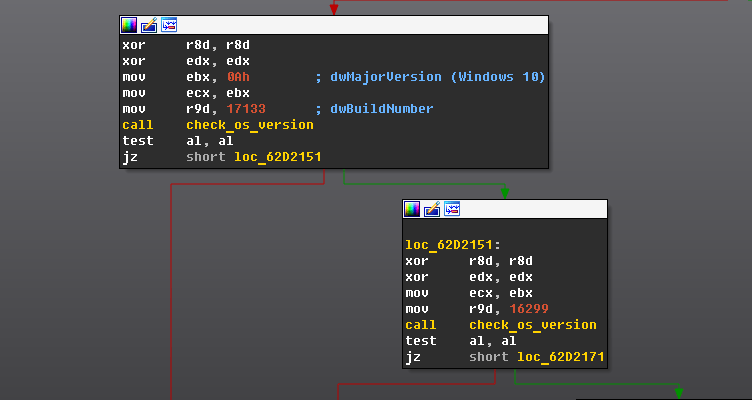
Zero-day in Windows Kernel Transaction Manager (CVE-2018-861 - vulnerability database

CyberWire Daily Podcast Republic

1-15 August 2023 Cyber Attacks Timeline – HACKMAGEDDON

Webinars Archives - DarkOwl, LLC

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect
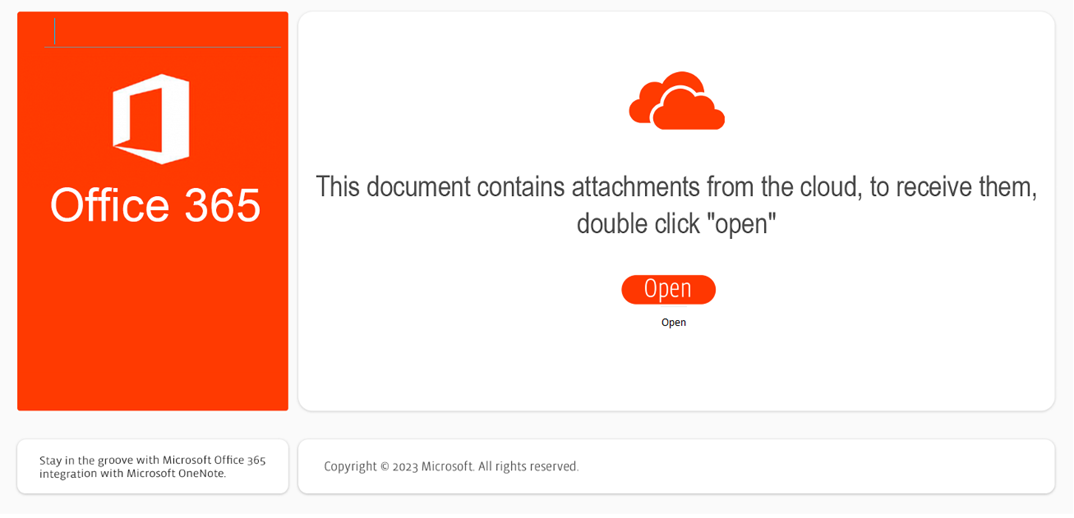
Black Basta ransomware - vulnerability database
de
por adulto (o preço varia de acordo com o tamanho do grupo)






