The Hidden Threat to Your SecOps: Tampered Log Data
Por um escritor misterioso
Descrição
Log data plays a critical role in SecOps by providing insights into systems. This makes log data a popular target for cybercriminals.

CI/CD Security: 5 Best Practices
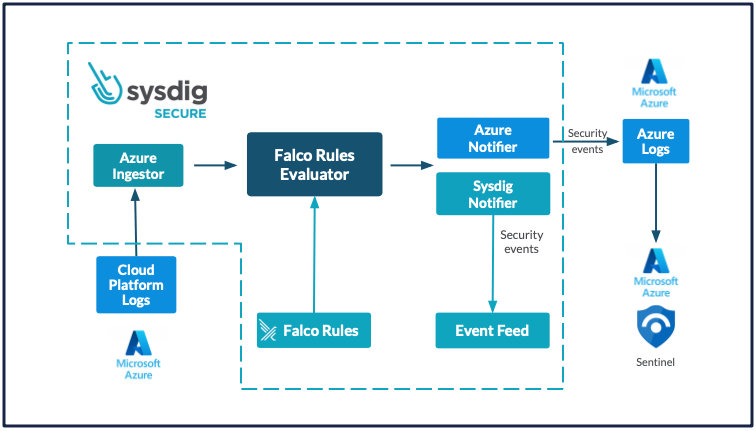
Microsoft Sentinel SIEM - Extract maximum value with Sysdig
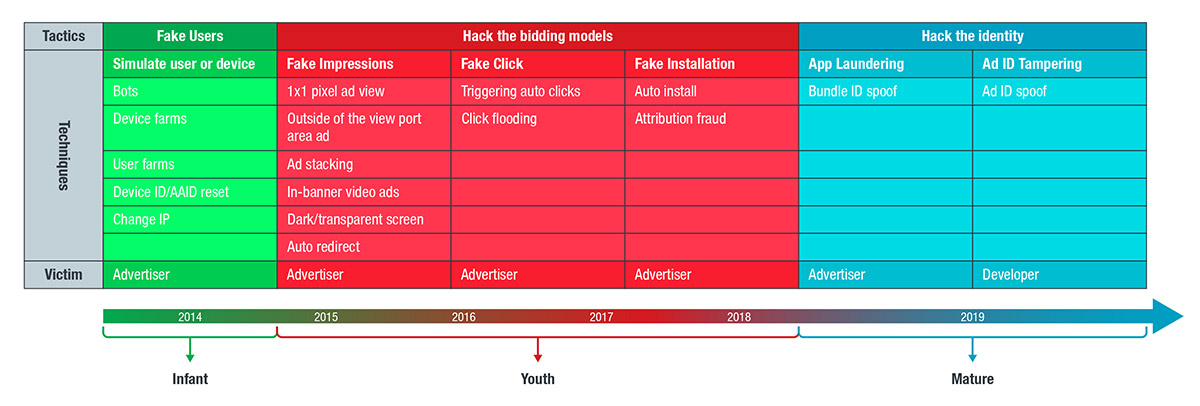
Review, Refocus, and Recalibrate: The 2019 Mobile Threat Landscape - Security Roundup

Unveiling Unvalidated Redirects: The Hidden Web Security Threat, by SecOps Solution, Nov, 2023
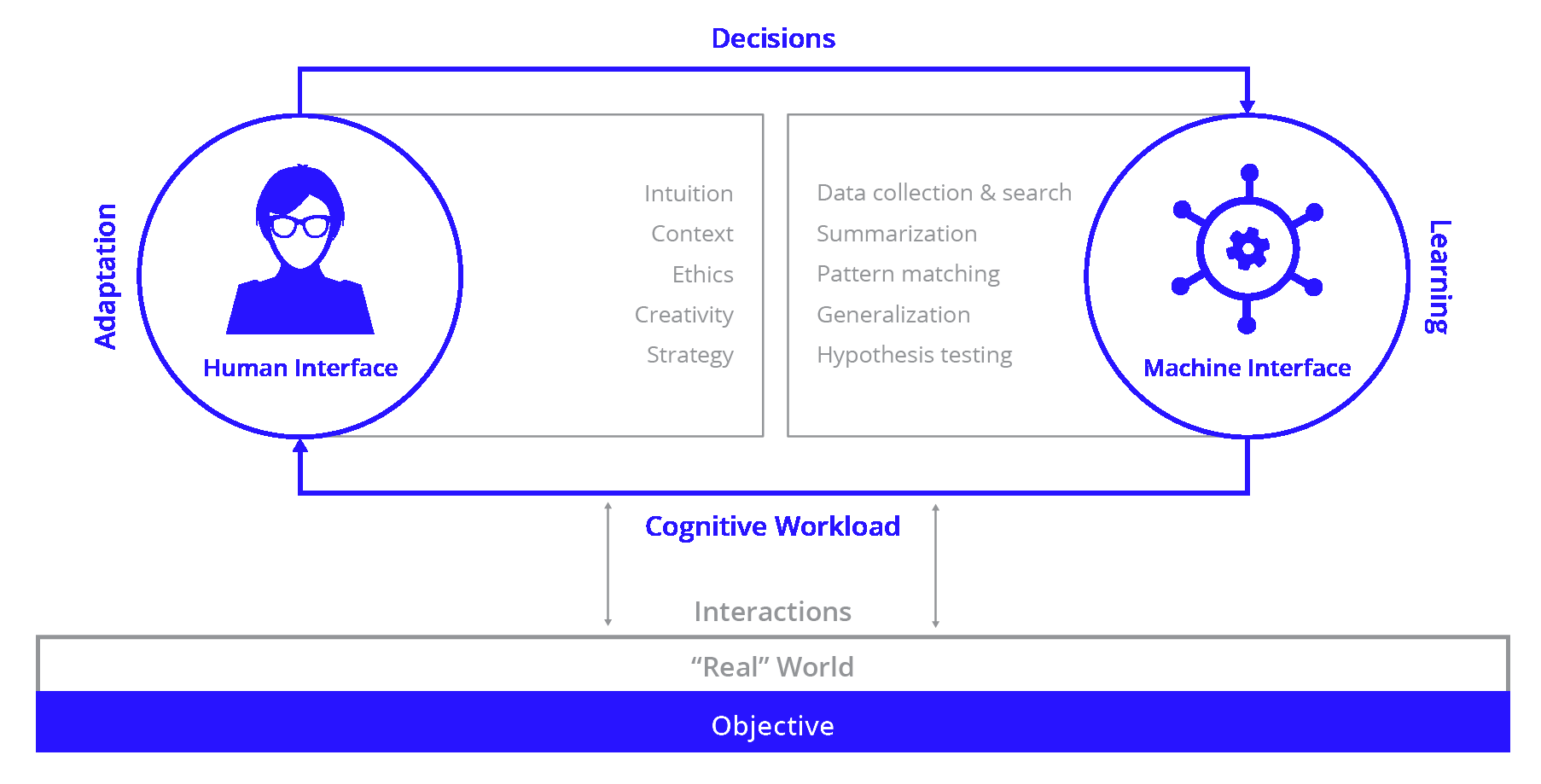
What Is Cyber Threat Hunting?

What is Log Tampering? - GeeksforGeeks

SOAP Security: Top Vulnerabilities and How to Prevent Them

Security operations - Cloud Adoption Framework

Network 101 Cheat Sheet, PDF, Denial Of Service Attack

Cybersecurity Fundamentals - Attack Surfaces and Vulnerabilities - Orange Matter

What is cyber risk? Essential terminology
de
por adulto (o preço varia de acordo com o tamanho do grupo)