Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.
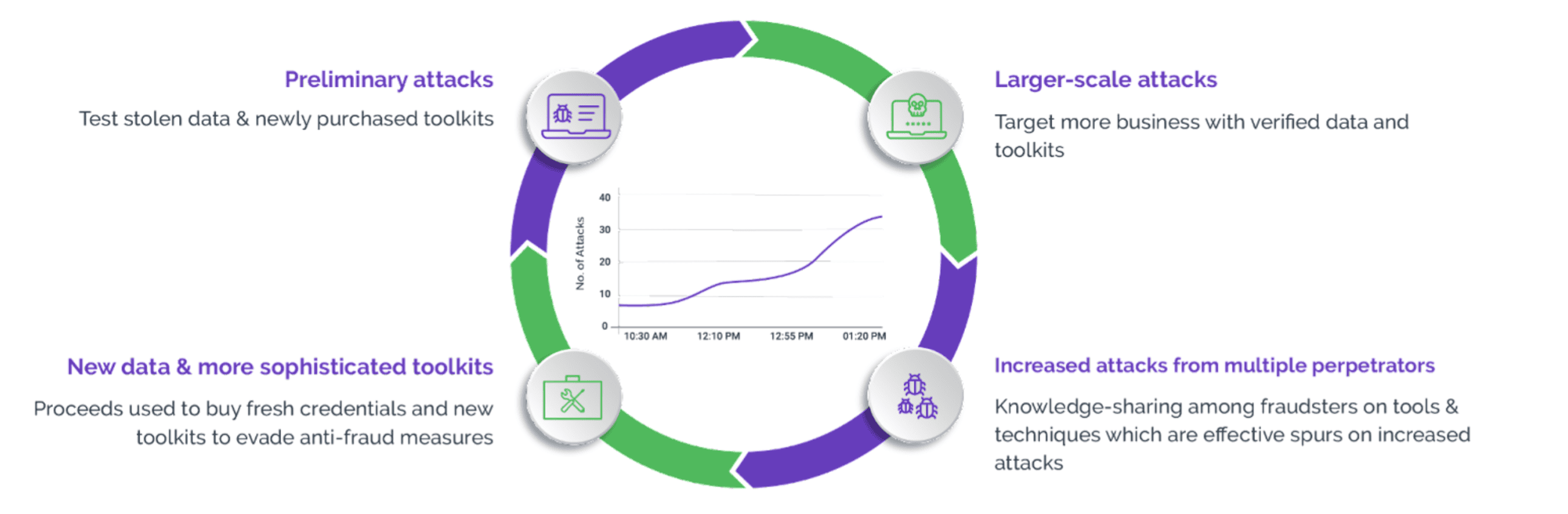
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Growing Cybercrime Outsourcing Model: Initial Access Brokers
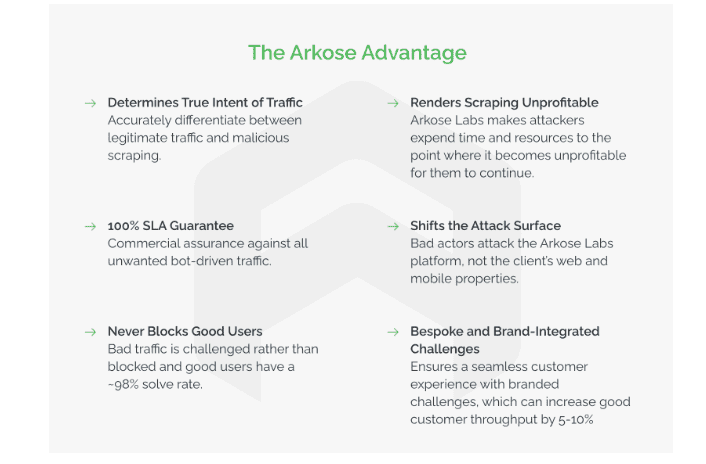
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
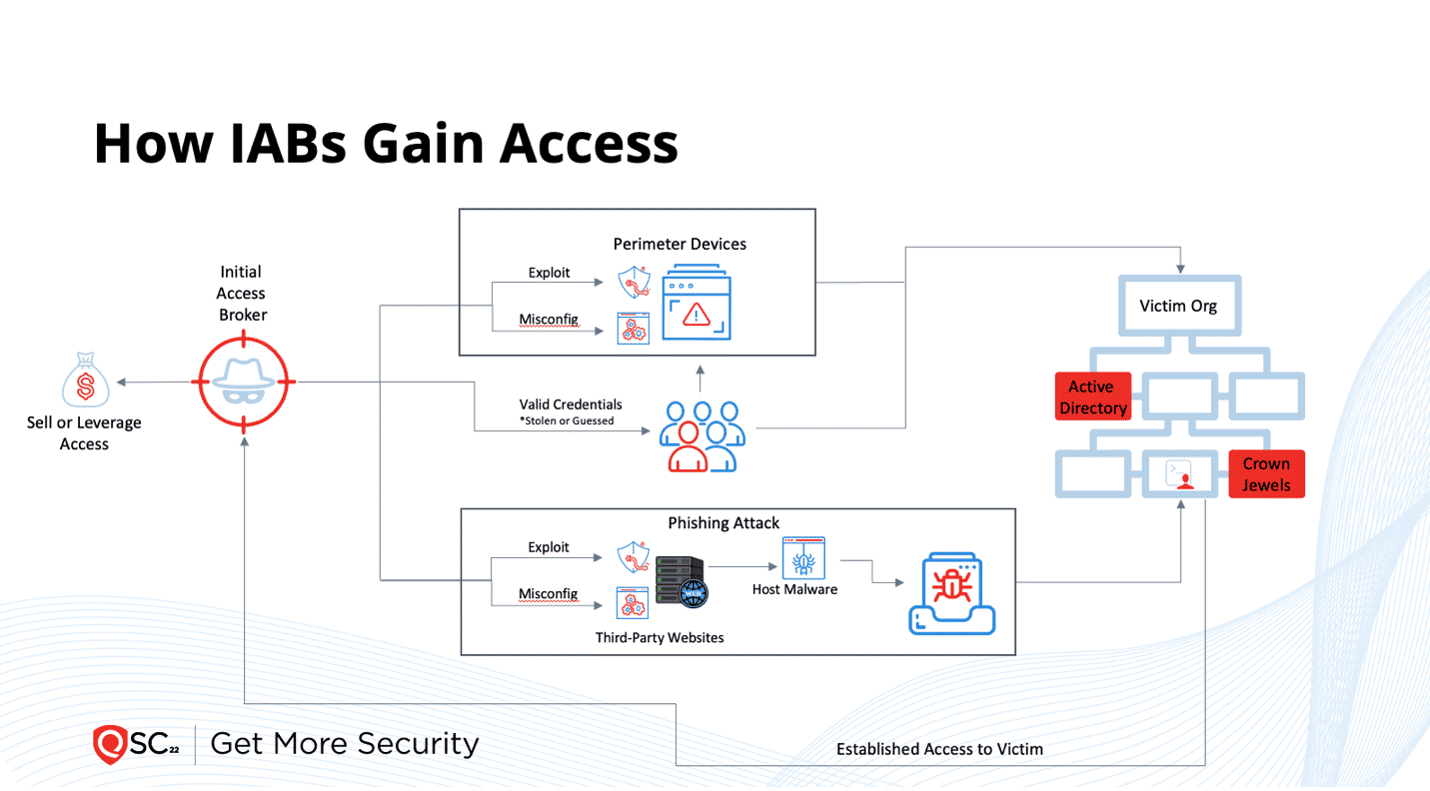
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Initial access brokers: How are IABs related to the rise in ransomware attacks?
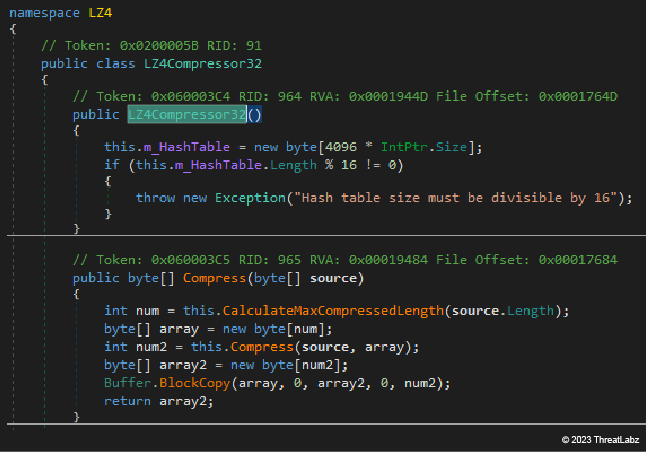
JanelaRAT ThreatLabz Zscaler Blog
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak

US20080120240A1 - Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management - Google Patents

Security in product lifecycle of IoT devices: A survey - ScienceDirect
New Report: Risky Analysis: Assessing and Improving AI Governance Tools
6 Types of Database Hacks Use to Obtain Unauthorized Access
de
por adulto (o preço varia de acordo com o tamanho do grupo)







