Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Descrição

CSO: Confronting the Threats of Cryptojacking and Ransomware
How to Monitor for Cryptomining in the Cloud

A deep learning approach for host-based cryptojacking malware

Cryptojacking: Understanding and defending against cloud compute

The Threat of Cryptojacking: Unveiling the Silent Cyber Robbery

Cryptojacking: Understanding and defending against cloud compute
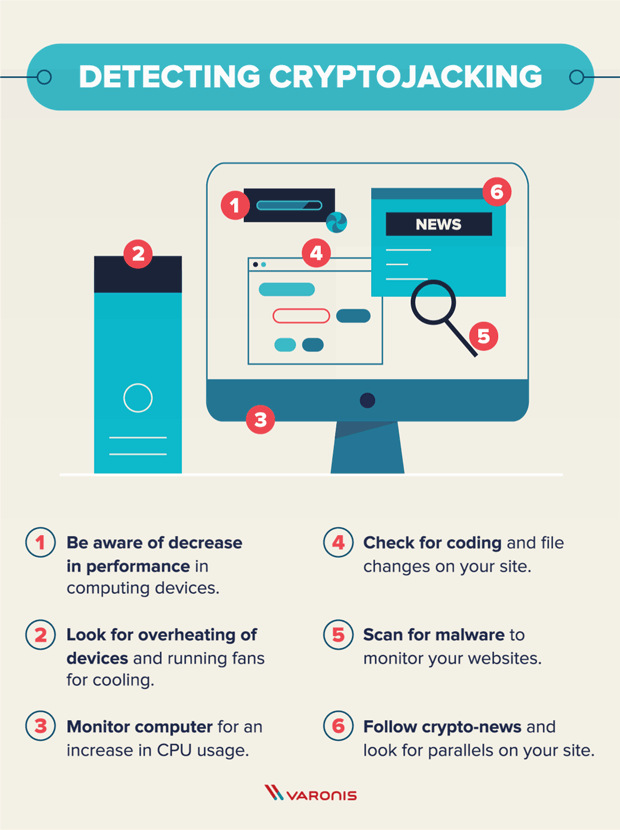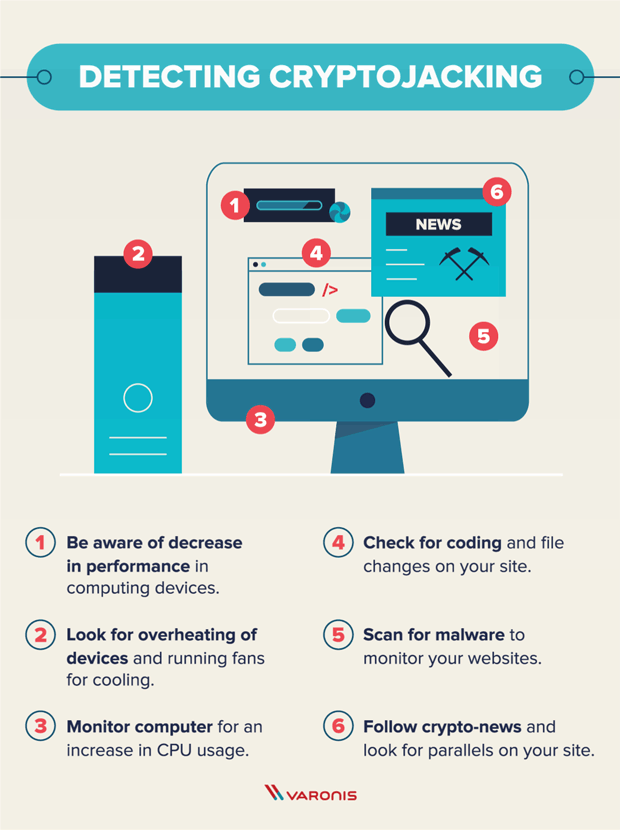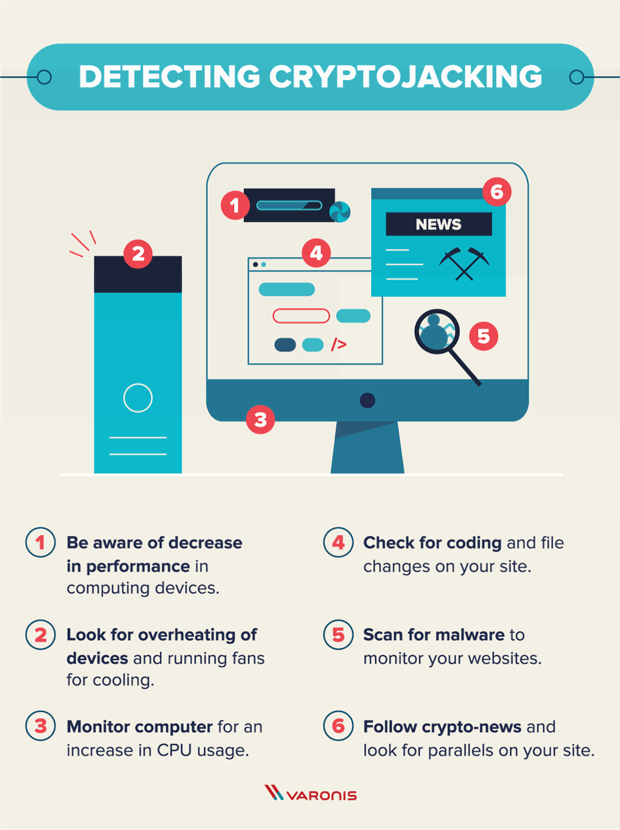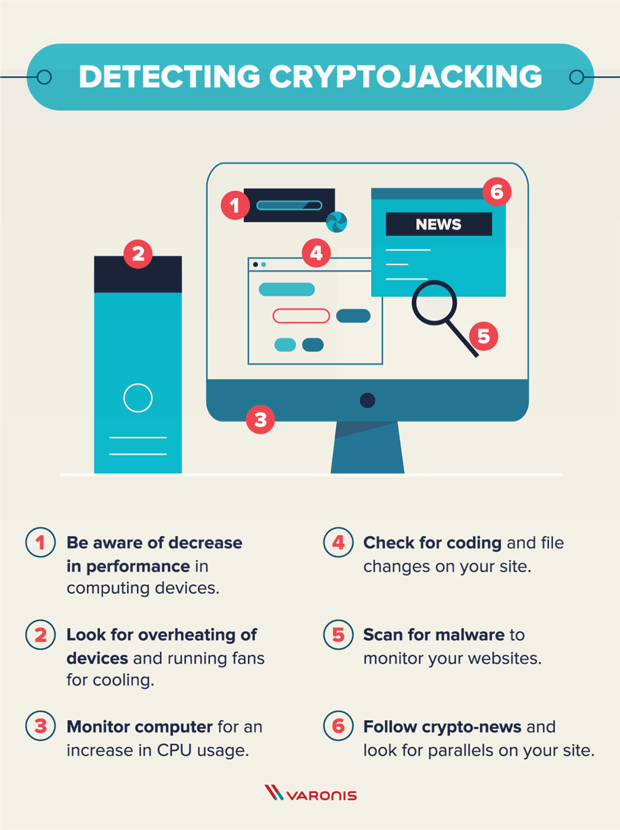
What Is Cryptojacking? Prevention and Detection Tips
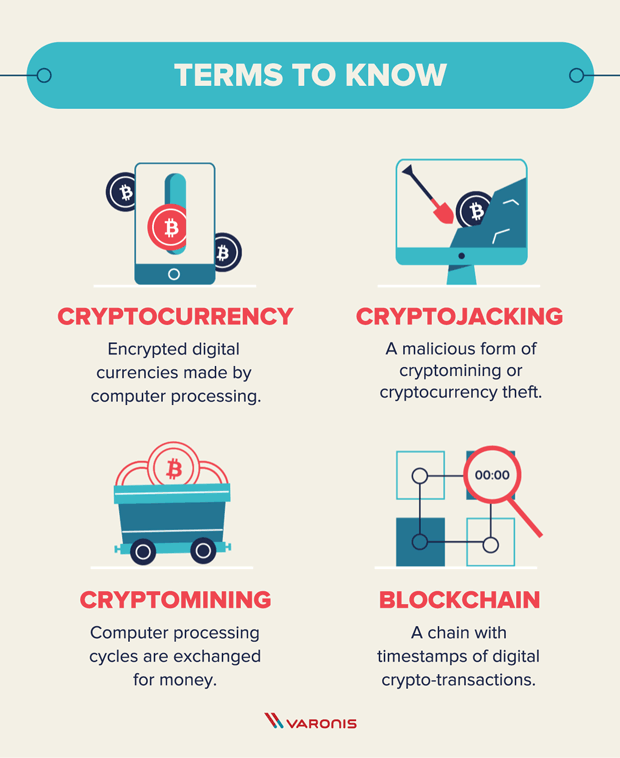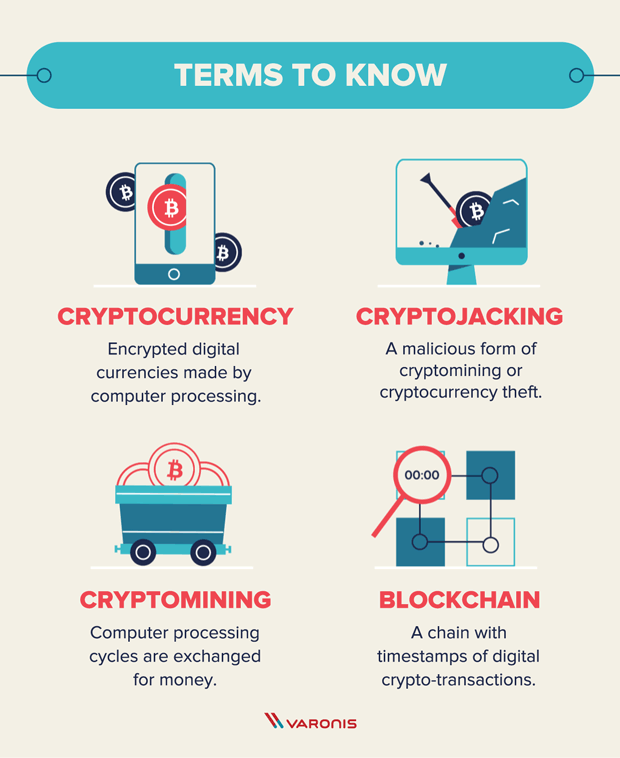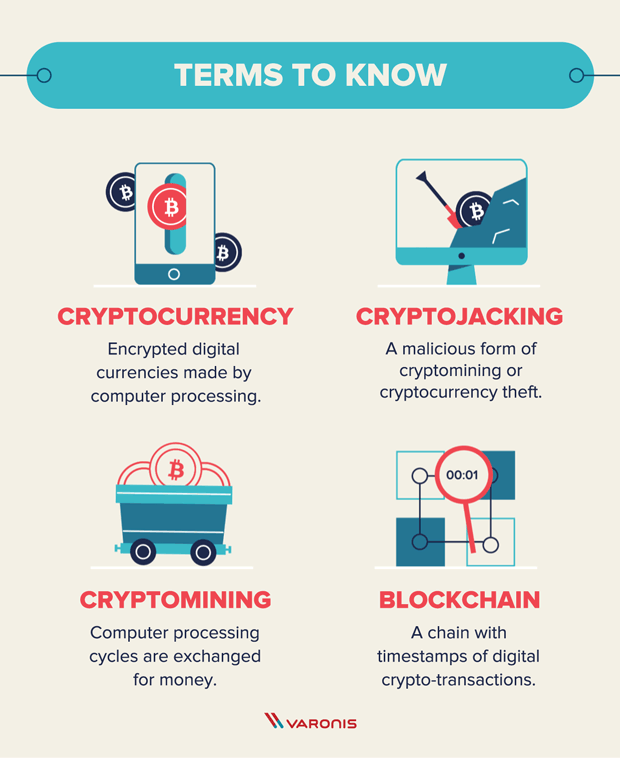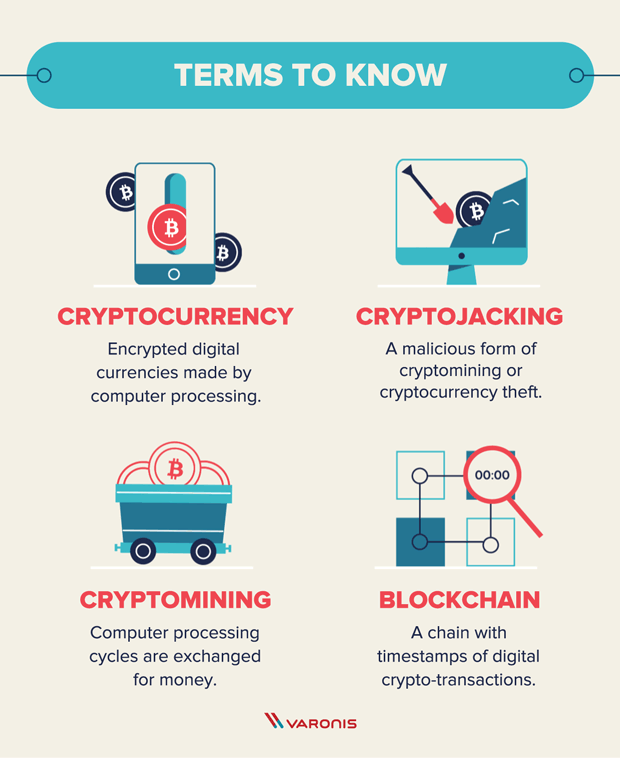
What Is Cryptojacking? Prevention and Detection Tips
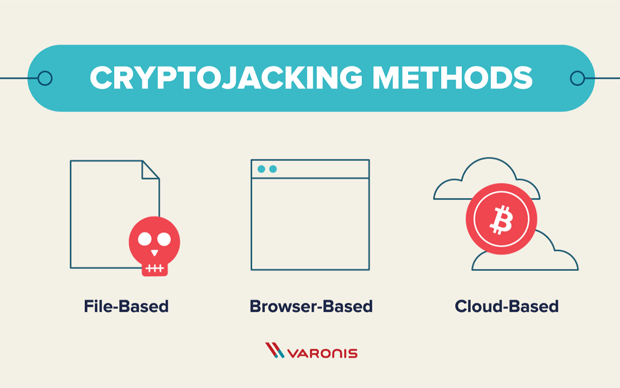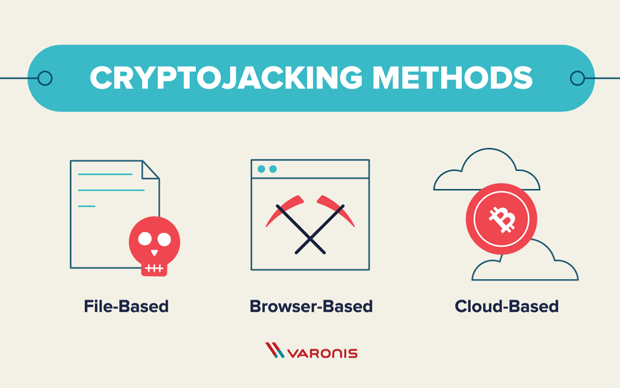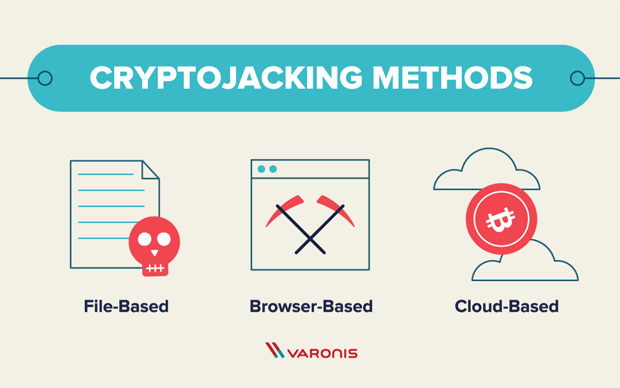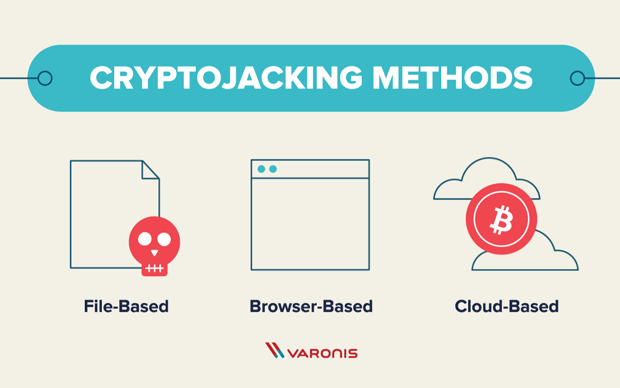
What Is Cryptojacking? Prevention and Detection Tips

What Is Cryptojacking? Prevention, Detection, Recovery
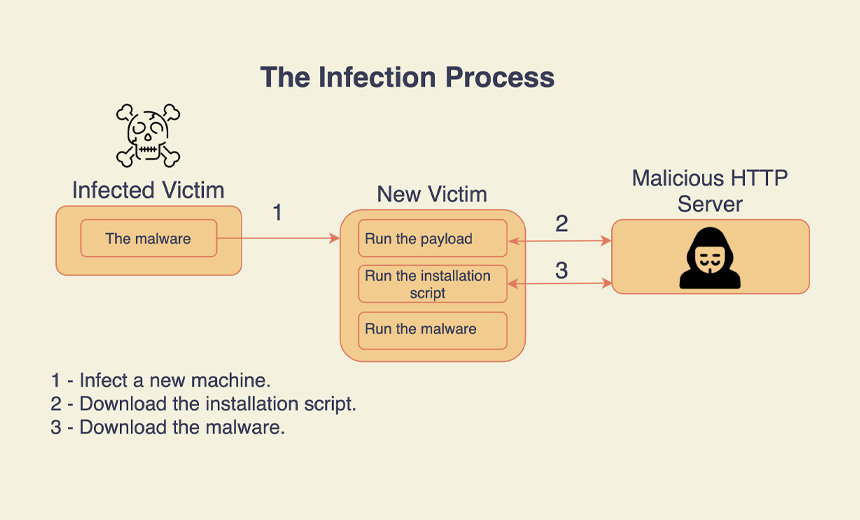
Cryptojacking Malware Adds Rootkit, Worming Capabilities
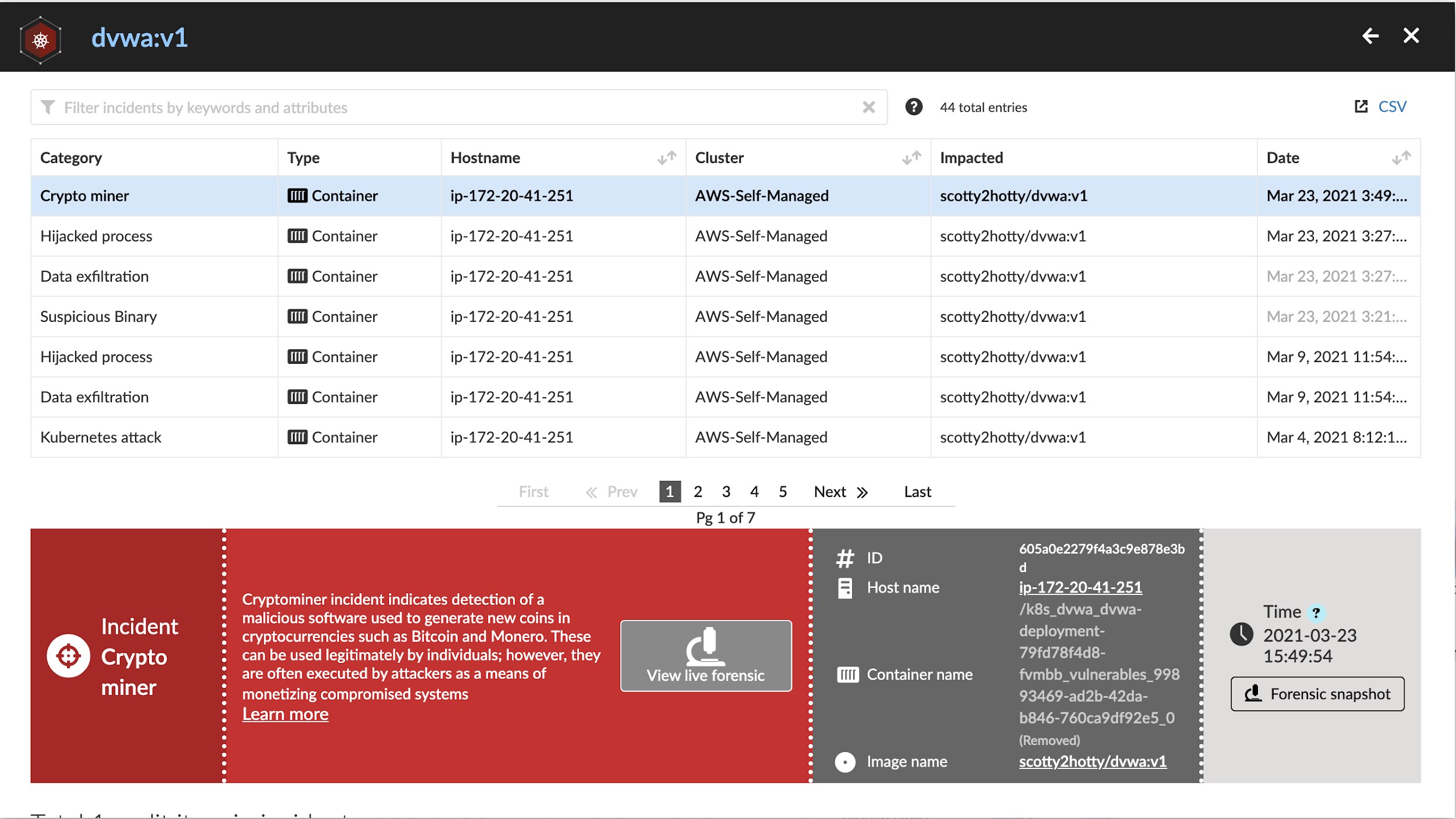
WAAS-Up with Cryptojacking Microservice-Based Web Apps?

How to keep your devices safe from cryptojacking

Cryptojacking explained: How to prevent, detect, and recover from
de
por adulto (o preço varia de acordo com o tamanho do grupo)







