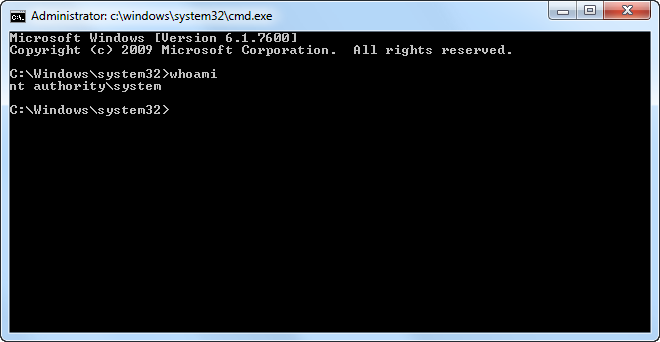
The Windows Process Journey — cmd.exe (Windows Command Processor), by Shlomi Boutnaru, Ph.D.
Por um escritor misterioso
Descrição
“cmd.exe” is the “Windows Command Processor” which is the default CLI (command line interface/interpreter) of Windows (and also reactOS). By the way, it is also known as “Command Prompt”. It is the…

Use nim compiled language to evade Windows Defender reverse shell detection, by Nol White Hat
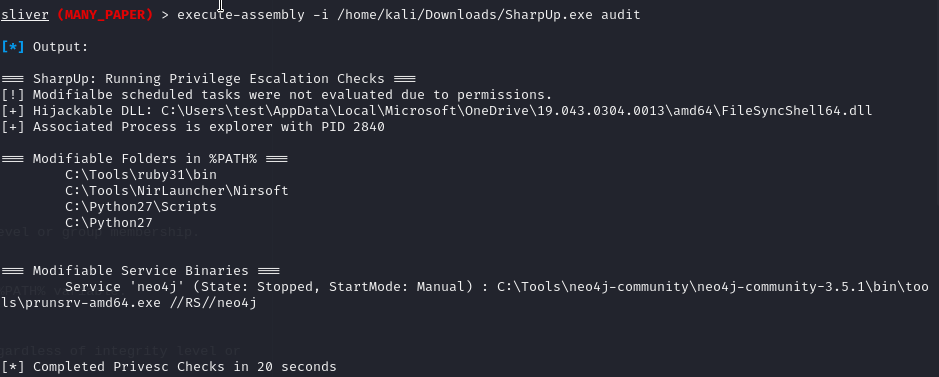
Exploring Execute-Assembly: A Deep Dive into In-Memory Threat Execution, by Tho Le

Detecting Malicious Drivers on Windows, by Tuomo Makkonen

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry
Process injection: How attackers run malicious code in other processes

Exploring Execute-Assembly: A Deep Dive into In-Memory Threat Execution, by Tho Le
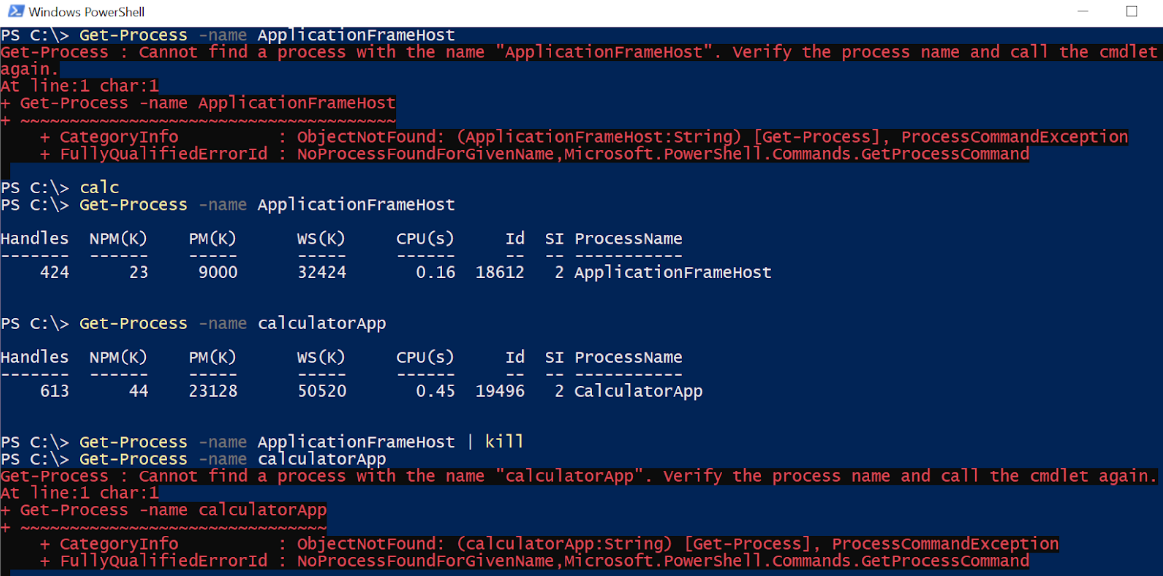
The Windows Process Journey — “ApplicationFrameHost.exe”, by Shlomi Boutnaru, Ph.D.

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry
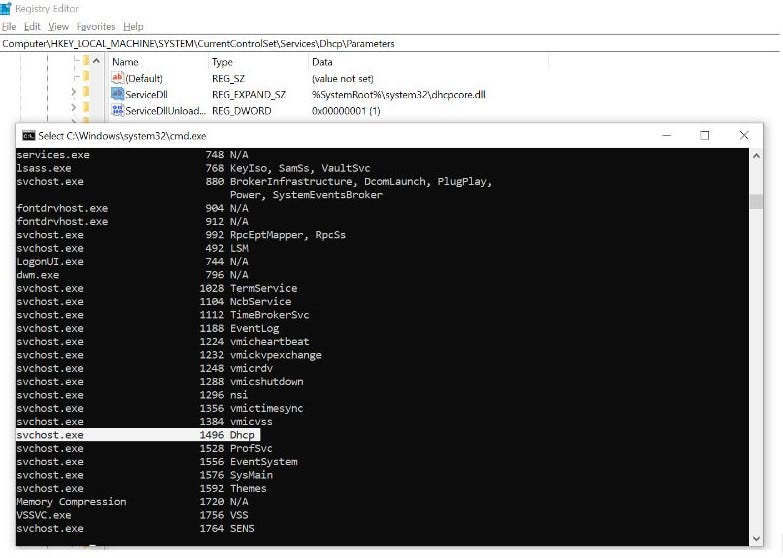
The Windows Process Journey — svchost.exe (Host Process for Windows Services), by Shlomi Boutnaru, Ph.D.

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry

Evading Detection with Hoaxshell Obfuscation — A Tool to Bypass Windows Defender, by Cybertech Maven

Detecting Malicious Drivers on Windows, by Tuomo Makkonen

Bypass “Mimikatz” using the Process Injection Technique, by Usman Sikander

Bypass “Mimikatz” using the Process Injection Technique, by Usman Sikander
de
por adulto (o preço varia de acordo com o tamanho do grupo)