window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
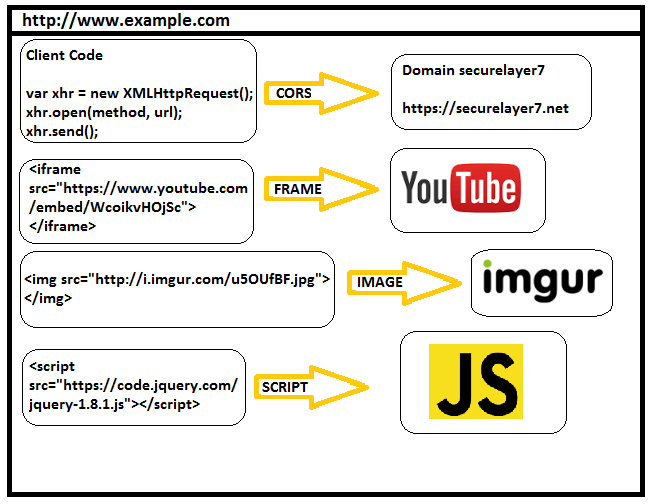
OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports

Pre-Authentication
GitHub - CrazyProger1/Simple-XSS: Simple-XSS is a multiplatform cross-site scripting (XSS) vulnerability exploitation tool.
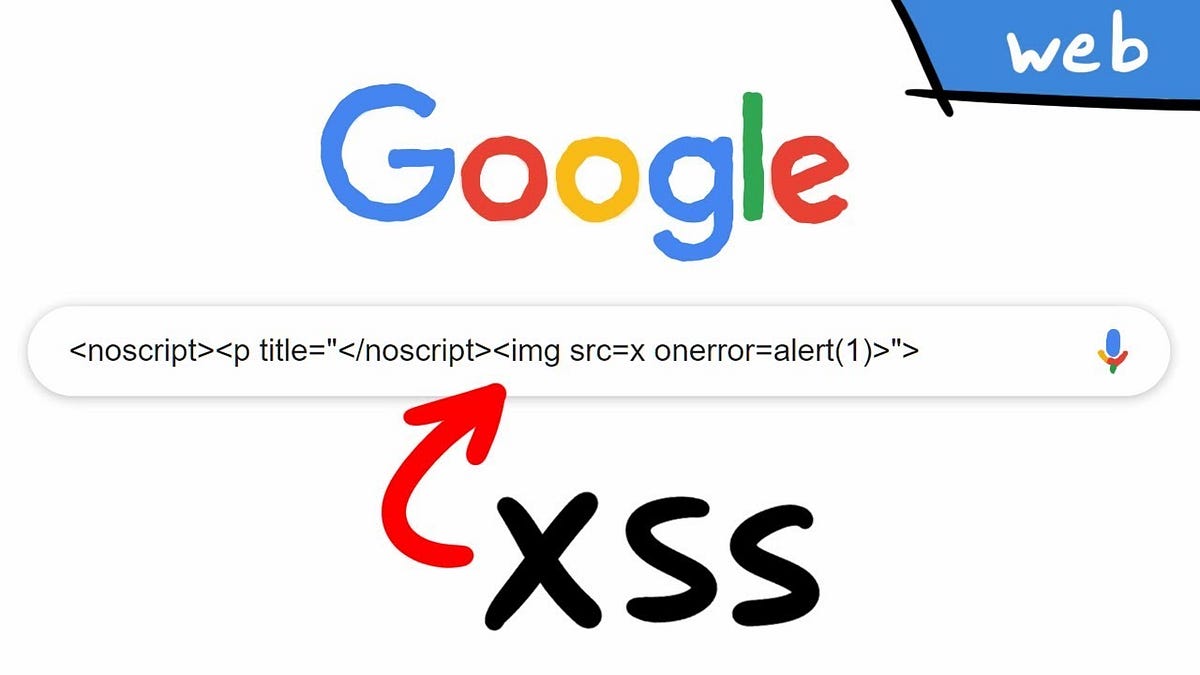
Cross Site Scripting ( XSS ) Vulnerability Payload List, by Ismail Tasdelen

XSS-Reflected (User_Agent). This is my first blog so, in this blog…, by Syed Munib Ahmed

Penetration testing & window.opener — XSS vectors part 1, by Josh Graham, TSS - Trusted Security Services

Web Security Academy Lab solution: ” Reflected XSS into HTML context with most tags and attributes blocked”, by Nidal Mahmud
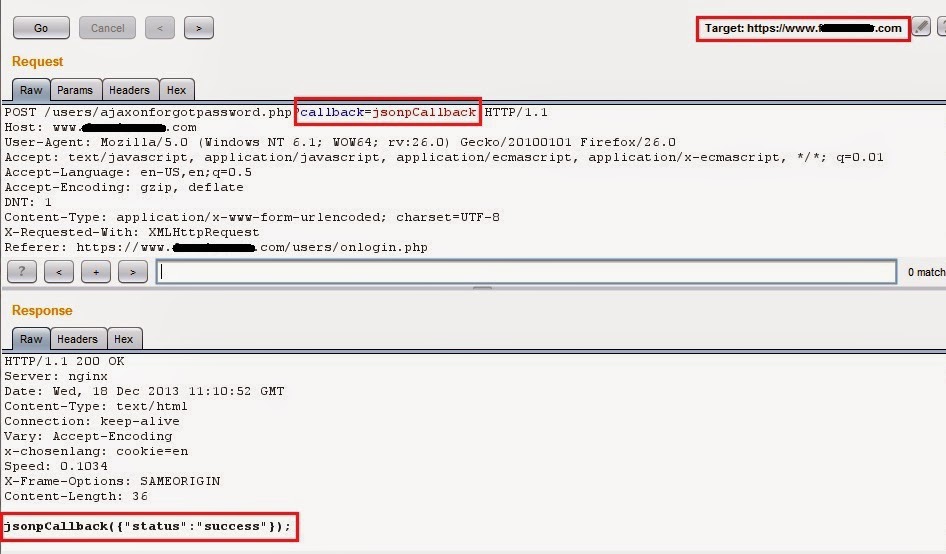
Cross Site Scripting through callback functionality

Add support for inline JS/CSS with #attached [#2391025]
de
por adulto (o preço varia de acordo com o tamanho do grupo)