Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

100+ essential penetration testing statistics [2023 edition

What is a fileless attack? How hackers invade systems without

Cyber Attacks: Tips for Protecting Your Organisation

For Cybersecurity Awareness Month (and Halloween) – Some Scary
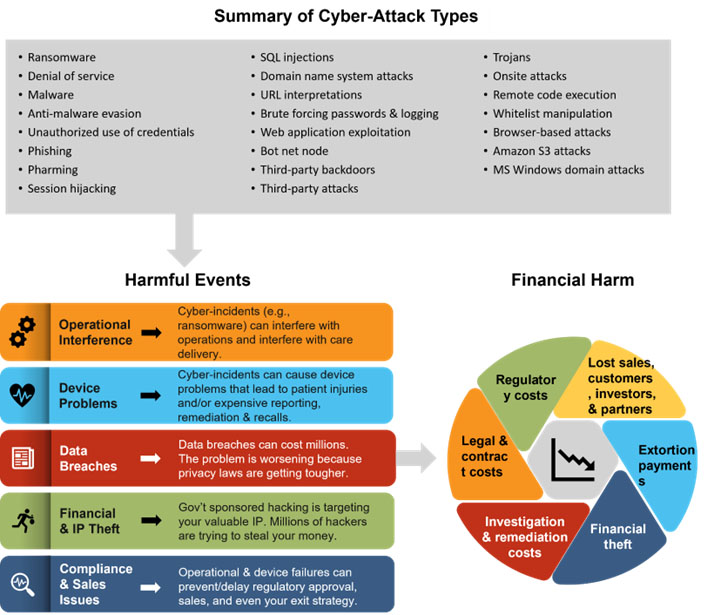
Medtech Cyber-Incidents A Costlier Problem Than You Think

Types of Cyber Attacks You Should Be Aware of in 2024

115 cybersecurity statistics + trends to know in 2024

Enterprise data breach: causes, challenges, prevention, and future

Runtime Attacks In-Memory Require a Different Response
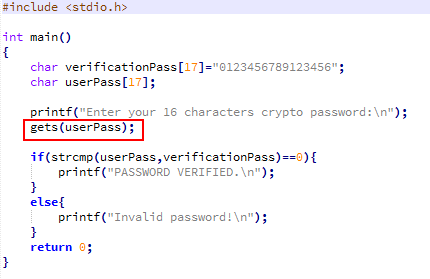
Inside the Mind of a Hacker: Attacking the Memory

Exploring Prompt Injection Attacks
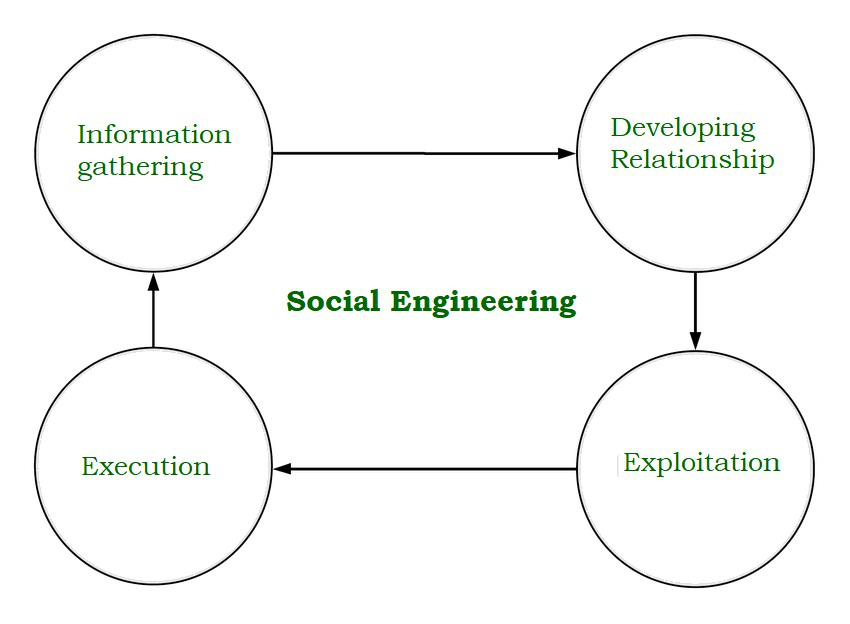
Types of Cyber Attacks - GeeksforGeeks

Metador APT hackers target telecommunications, ISPs, universities

How Hackers Rob Banks, 2018-05-21
de
por adulto (o preço varia de acordo com o tamanho do grupo)