How hackers use idle scans in port scan attacks
Por um escritor misterioso
Descrição
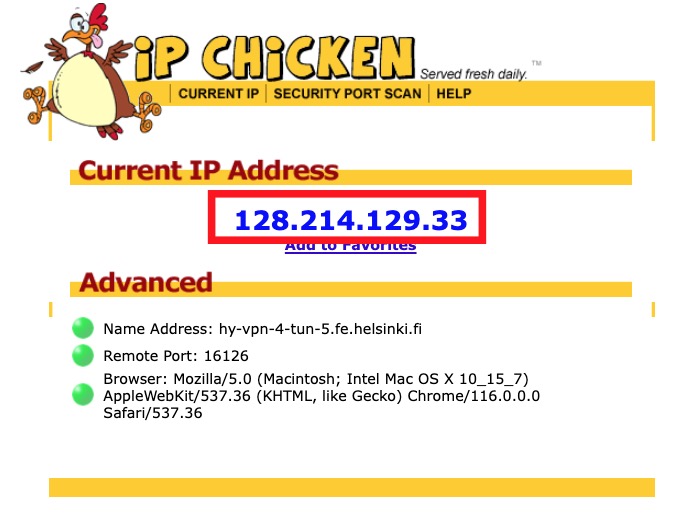
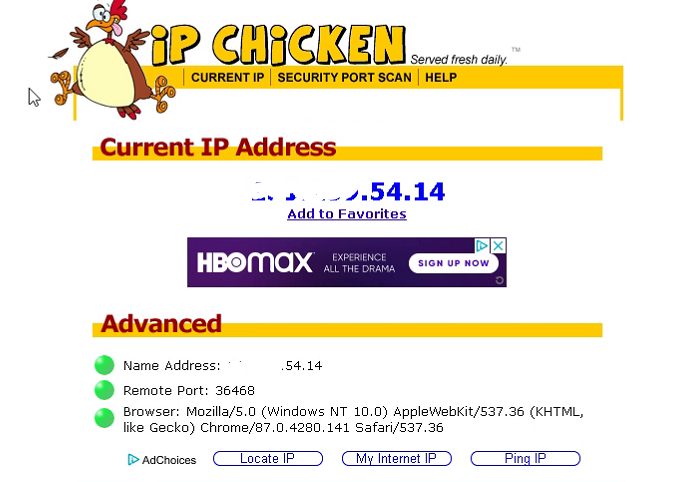
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

PDF) Surveying Port Scans and Their Detection Methodologies

Legal Issues Nmap Network Scanning

How hackers use idle scans in port scan attacks
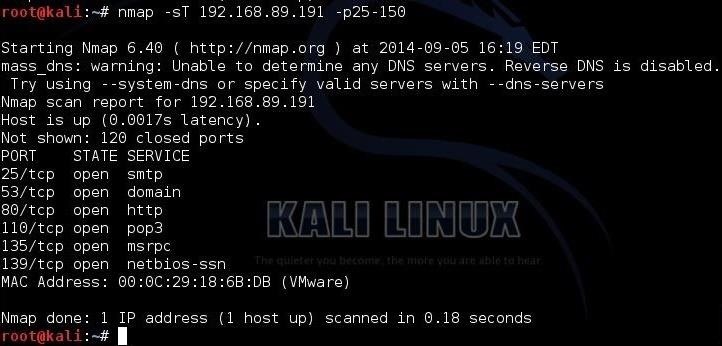
Hack Like a Pro: Advanced Nmap for Reconnaissance « Null Byte :: WonderHowTo

Port Scanning: A Comprehensive Guide for Safeguarding Cyberspace
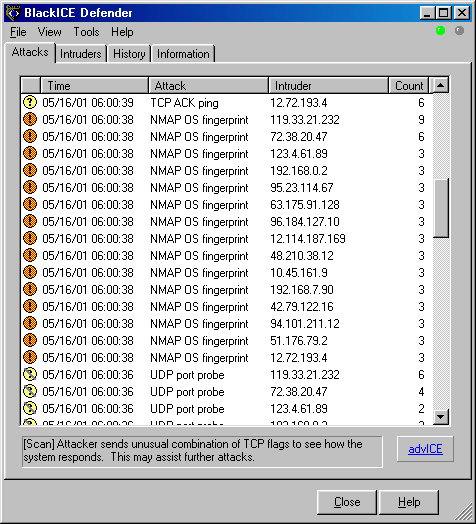
Subverting Intrusion Detection Systems

A Complete Guide to Nmap, Nmap Tutorial
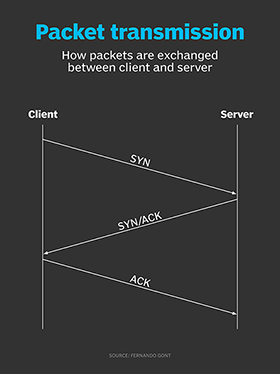
How hackers use idle scans in port scan attacks

Scanning Techniques (EC-Council) EC-Council. Certified Ethical Hacker (CEH) Version 10 eBook w/ iLabs (Volumes 1 through 4). EC-Council Academia, 08/2018. VitalBook file. Flashcards
PDF) Port Scanning: Techniques, Tools and Detection
IDLE scan executing process Download Scientific Diagram
Network Scanning Techniques
de
por adulto (o preço varia de acordo com o tamanho do grupo)